硬件安全
硬件安全
安全的定义
- Create, maintain and attest a secure state for an embedded device Ensure confidentiality, integrity and availability of the data processed on the device
- Ensure the safety of the people and the environment interacting with the device
- Protect the device itself, its environment and other data from processed malicious data
Abstraction Layers and Attack Vectors
skipped
Secure Embedded System Design
Typical Criteria
- Time to market
- Design + manufacturing setup cost
- Component + manufacturing cost
- Security
- Maintainability
- Energy
- Performance
- Features
System architecture
Attack surface is lower if critical data and functions are integrated into few ICs
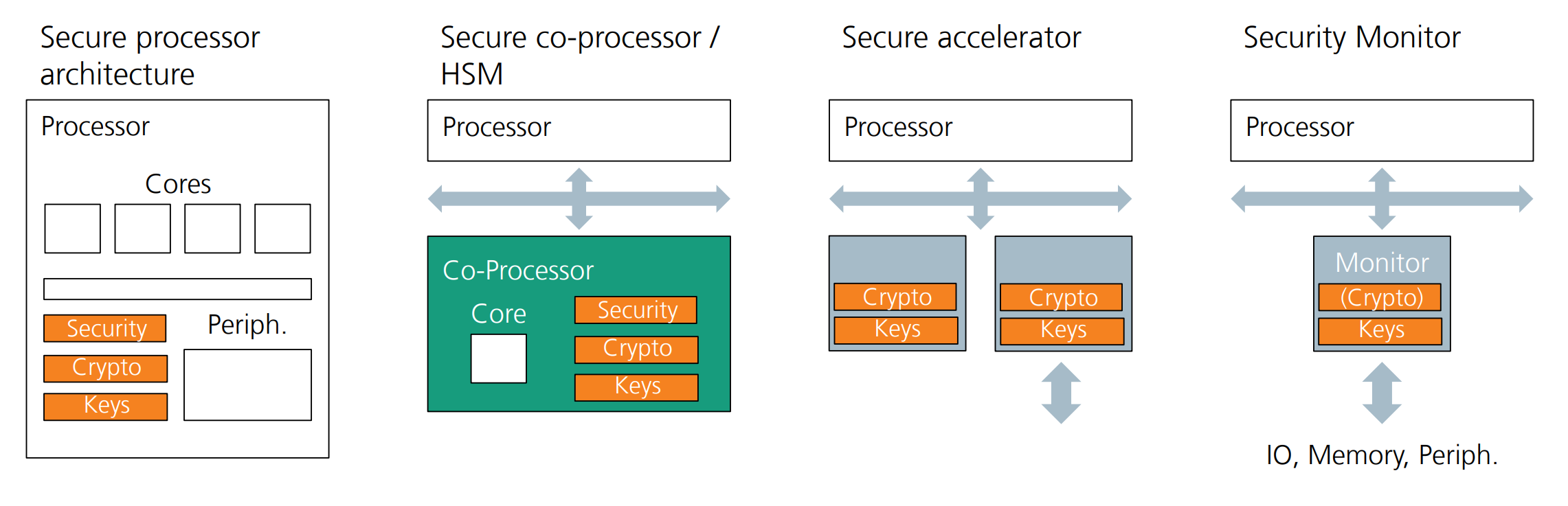
Secure processor architecture
Tight integration of cryptographic and security functionality in the processor
HW support for SW separation
Secure co-processor / HSM
- Separation of application processor and security functionality
- Dedicated interface: High latency, low throughput
Secure accelerator
- Encapsuled cryptographic functionalit
Security monitor
- Lightweight module outside the main data-path
- Provide HW dedicated security functionality
Security-focused component
- Implementation of cryptographic algorithms
- Root of trust
- Randomness
- Clock
- Protected debug interface
Cryptographic algorithms and parameters
Never use proprietary ciphers!
Use good sources of randomness!
Asymmetric vs. symmetric cryptography
- Symmetric ciphers are fast, Key management more difficult
- Implementation and computation complexity significant, Only makes sense with Public Key Infrastructure (PKI)
TODO: add rest slides
Cryptography Implementation
AES
1 | KeyExpansion(CipherKey,ExpandedKey); |
Round function
1 | Round(State,ExpandedKey[i]) { |
final round (no mix columns)
1 | FinalRound(State,ExpandedKey[Nrb]) { |
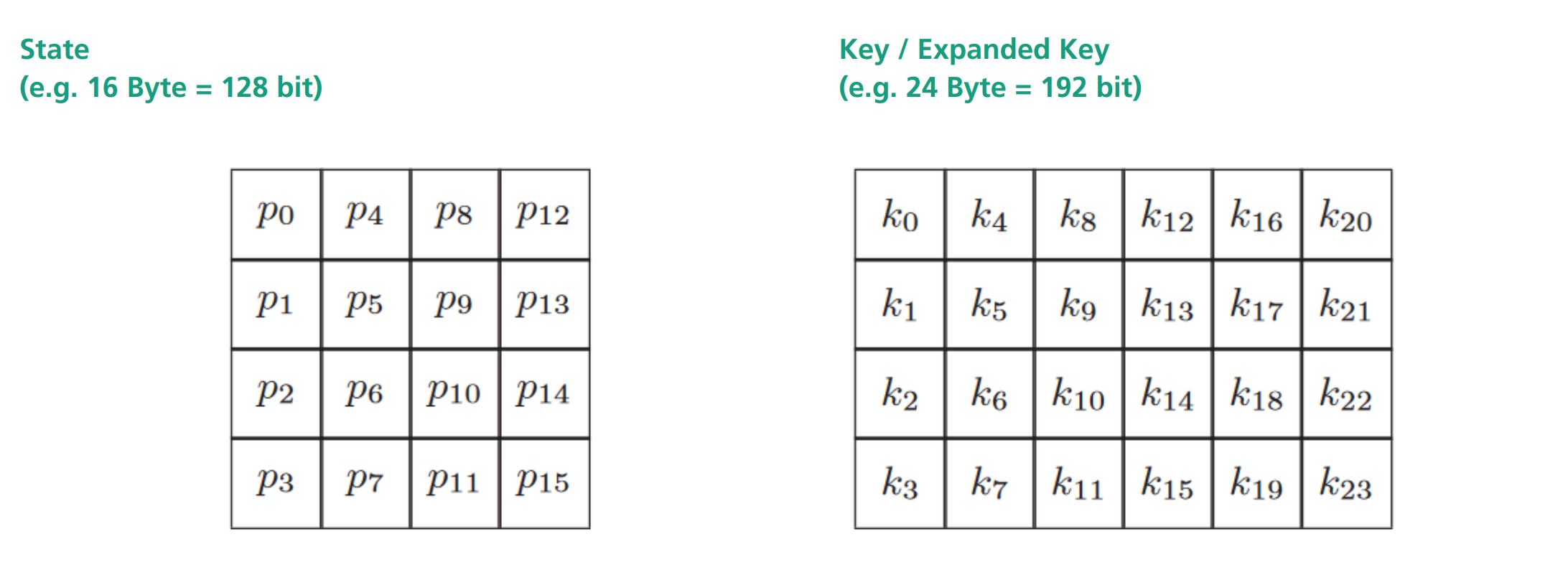
State
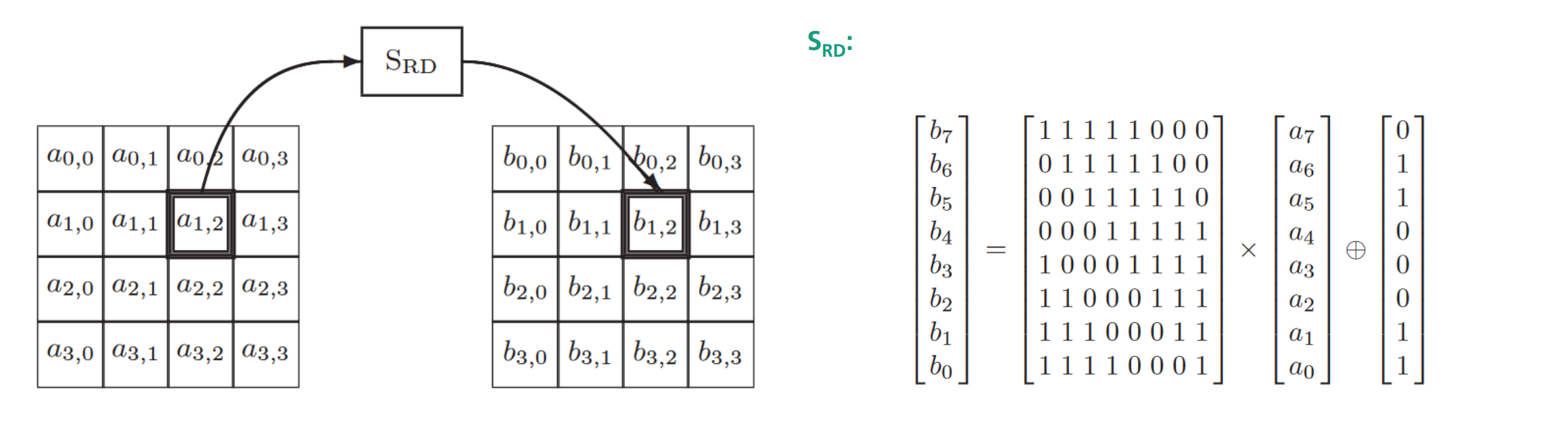
SubBytes
每个byte 通过 \(S_{RD}\)
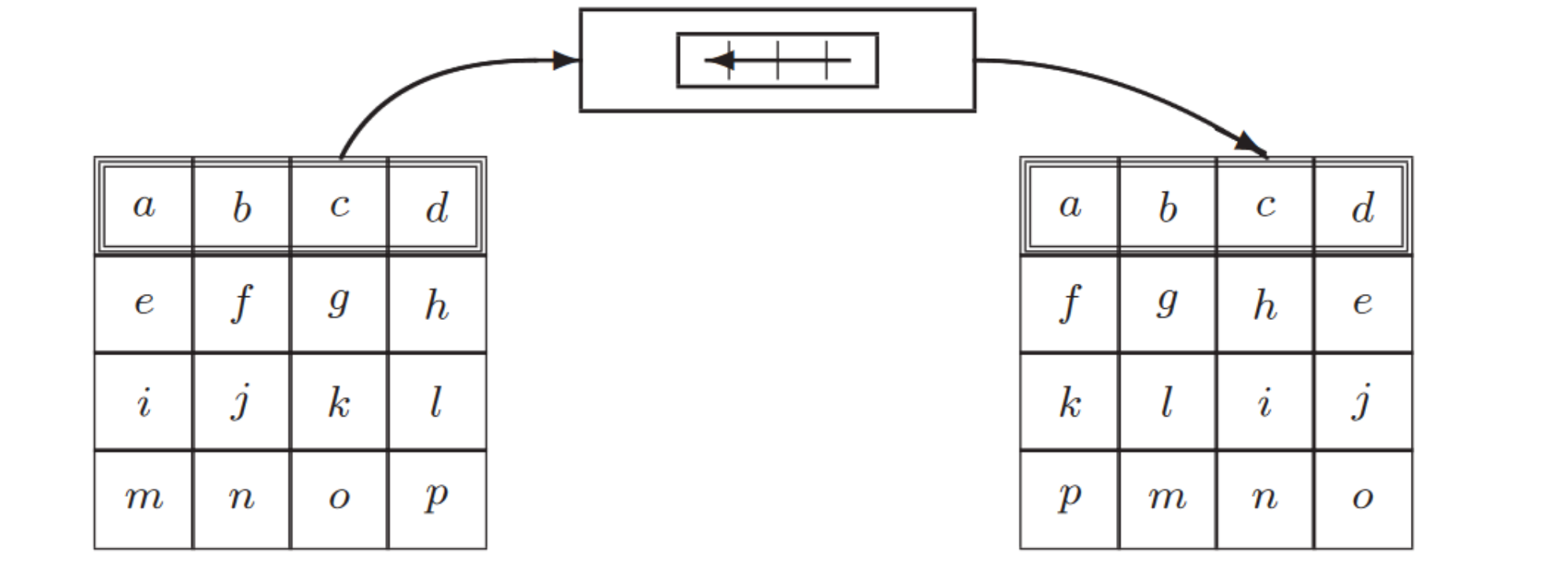
ShiftRows
第 \(i\) 行向左shift \(i-1\)
Mix column
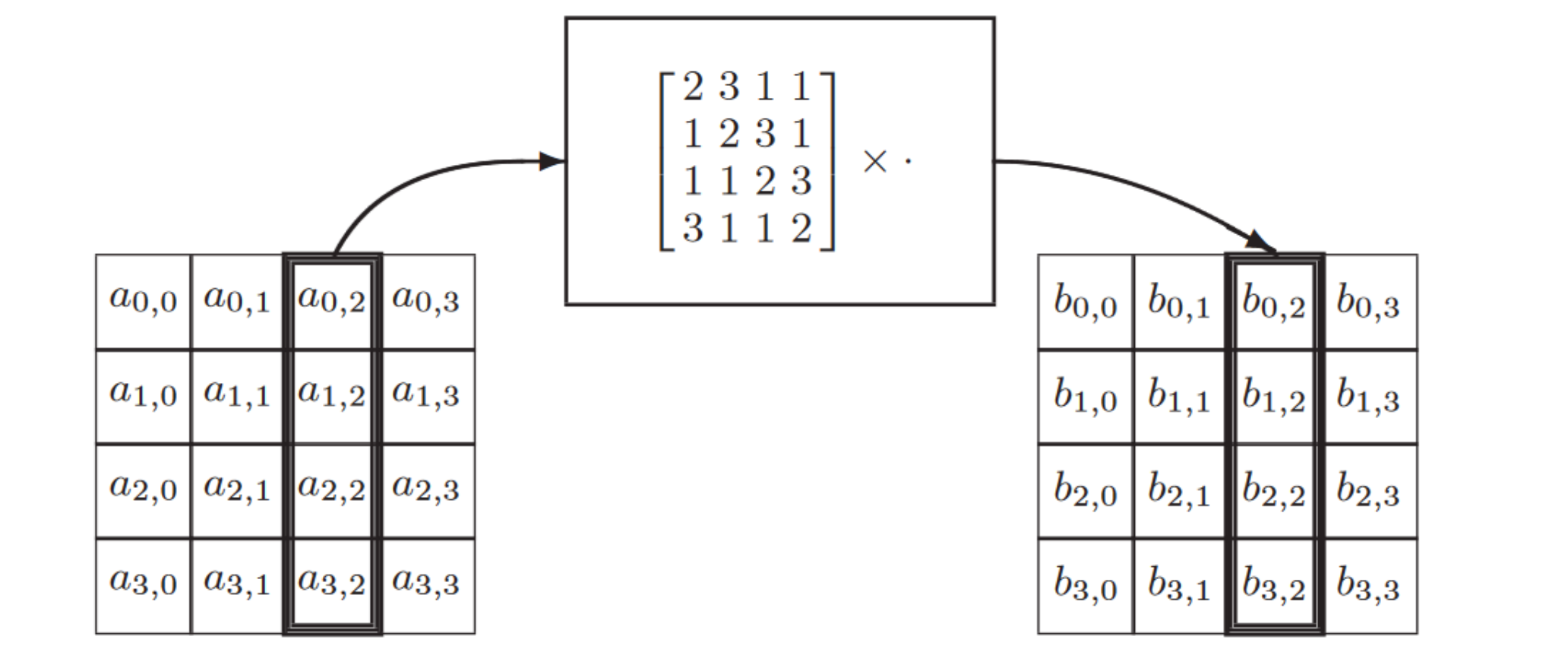
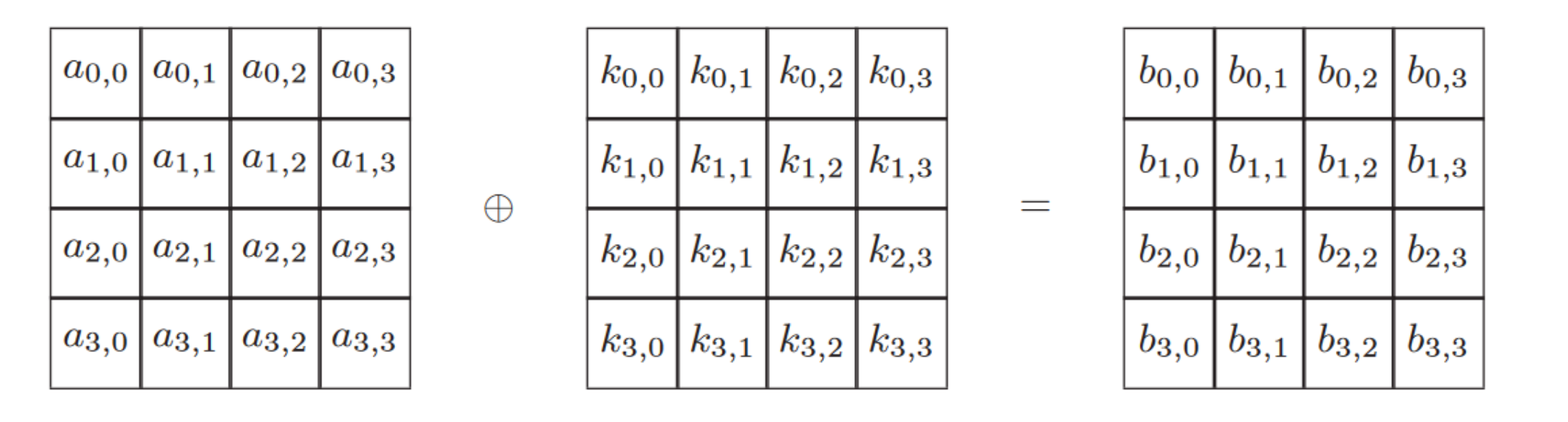
Add round key
把key xor 上去
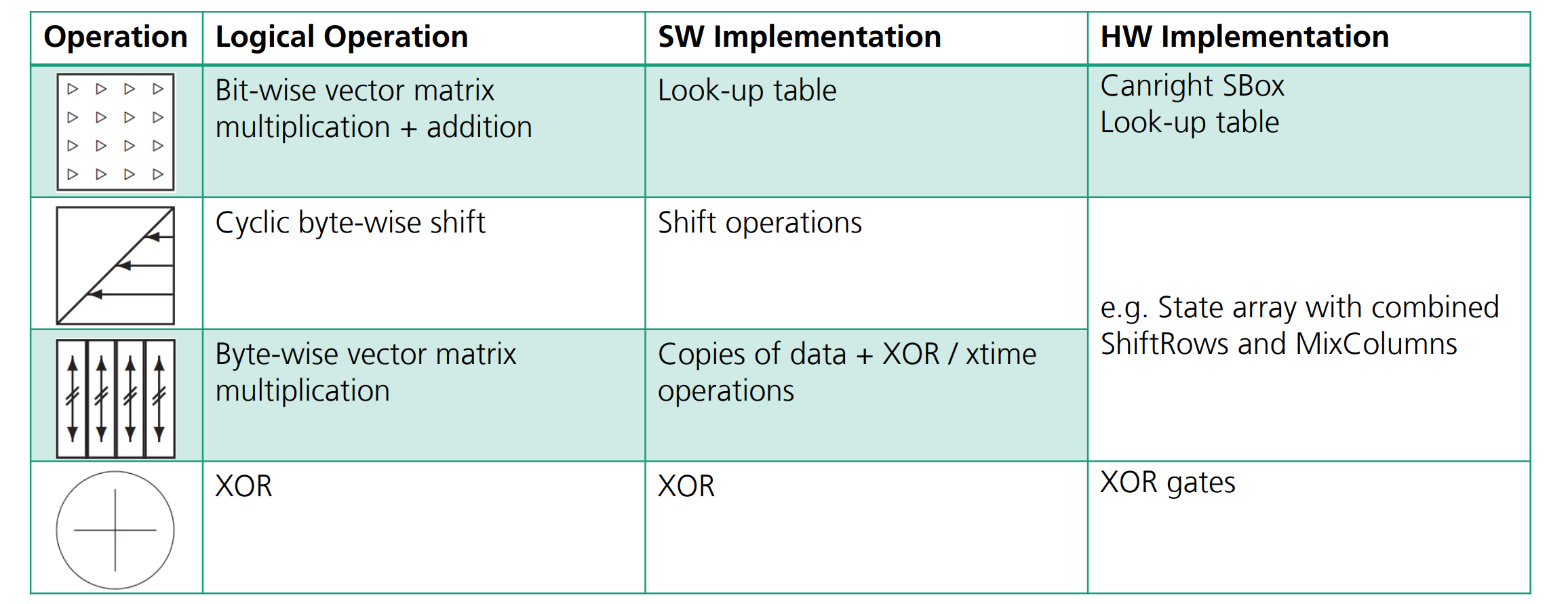
Implementation
Elliptic curve
\(a, b \in \mathbb{F}_p\) satisfy \(4 a^3+27 b^2 \neq 0(\bmod p)\) \[ y^2=x^3+a x+b \]
Addition
P+Q
Let \(P \neq \mathcal{O}\), and \(Q \neq \mathcal{O}\) such that \(P \neq \pm Q\).
\(P+Q=\left(x_R, y_R\right)\) , Let \(\lambda=\left(y_Q-y_P\right) /\left(x_Q-x_P\right)\) , \(P+Q=-R\). \[ x_R=\lambda^2-x_P-x_Q, \quad y_R=\lambda\left(x_P-x_R\right)-y_P \text {. } \]
P+P
\(P \neq \mathcal{O}, P \neq-P\) , \(\lambda=\left(3 x_P^2+a\right) /\left(2 y_P\right)\) , \([2] P=-R\) \[ x_R=\lambda^2-2 x_P, \quad y_R=\lambda\left(x_P-x_R\right)-y_P \text {. } \]
Neutral element
The point at infinity is the neutral element.
\(P+(-P)=0\)
Discrete elliptic curves
\[ P+Q: \lambda=\left(y_2-y_1\right)\left(x_2-x_1\right)^{-1} \bmod p \]
\[ P+P: \lambda=\left(3 x_1{ }^2+a\right)\left(2 y_1\right)^{-1} \bmod p \]
curve symmetrical at p/2
Elliptic curves for cryptography
- parameter \(a,b\), modulus \(p\)
- \(ord(E)\) large enough
- \(g\) generator
key generation
- private key: \(d\) selected uniformly at random from \([1, n − 1]\)
- public key is \(Q = d P\)
elliptic curve discrete logarithm problem
Given \(Q\) , determine \(d\)
Encryption
plaintext \(m\) is represented by point \(M\) \[ E(k,M)=(kP, M + kQ) \]
\[ D(k,c_1,c_2)= c_2-d(c_1)=c_2-d(kP)=c_2-k(dP)=c_2-kQ \]
Point addition and point doubling

Montgomery reduction
Given two numbers \(X\) and \(Y\) in \([0, N-1]\). Let \(Z=MonPro(X,Y)\) , \(R\) is a power of \(2\)
\(Z=(XY)R^{-1} \bmod N\)
so, \((XR^{-1})(YR^{-1})=Z R^{-1} \bmod N\)
Side Channel Attack
- Side channel: any source of information on some secret besides actual communication channel
- Side-channel analysis / attacks: making use of side information to recover the secret
Side-channels
- Memory accesses, Bus accesses
- Time, Light, Sound
- Behaviour of other computers
- Power comsumption
- Radiation,EM,
Microarchitectural attacks
- Attacks purely in software
Cache attacks
Cache hits 和 Cache misses 需要的 CPU cycles 不一样
Prime+Probe Attack
- attacker fill the cache
- victim evicts cache
- attacker probe data to determine if accessed
CMOS Dynamic + Static power
\[ P=P_{\text {static }}+P_{\text {dynamic }}+P_{\text {noise }} \]
- 动态功耗 是由CMOS电路中开关变动引起的
Power
Global measurement of the entire system’s power consumption: High noise
Electromagnetic (EM) side channel attacks
Allows low signal to noise ratio (SNR)
High resolution in location and time
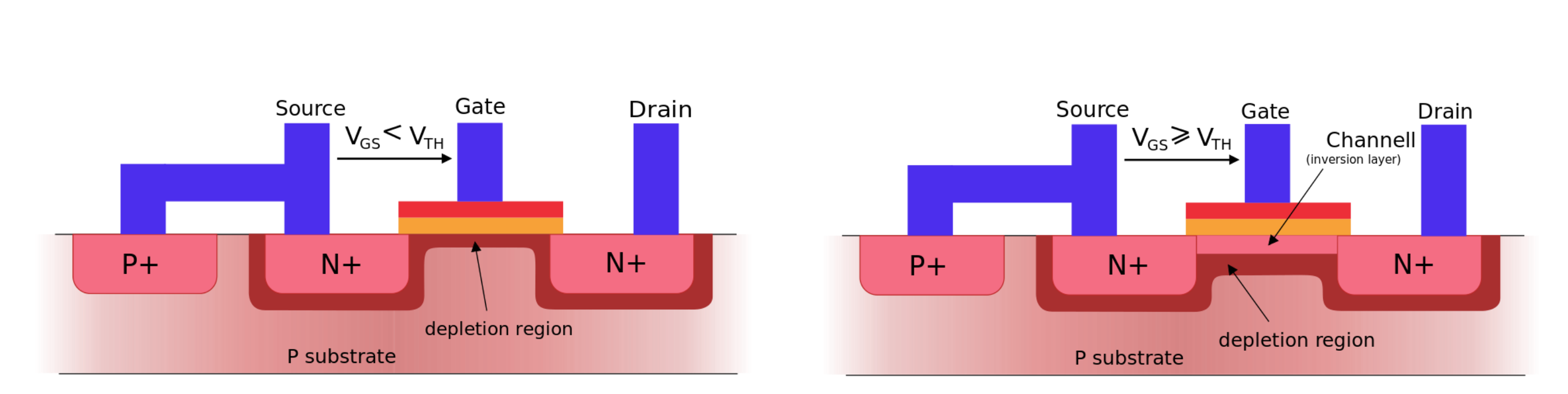
MOSFET basics
Low input voltage: no current from Source to Drain
High input voltage: current from Source to Drain
Photonic Emission
- Switching of transistors causes emission of photons
Decapsulation
Necessary e.g. for local EM, photonic emission, and later laser fault attacks
蚀刻 (Etching):
- 使用化学溶液(如强酸)溶解芯片封装材料,暴露出内部电路。
- 常用于去除塑料封装。
研磨 (Grinding):
- 使用机械方法逐层研磨掉封装材料。
- 适用于硬质封装材料。
芯片薄化 (Thinning):
- 通过研磨或化学蚀刻将芯片背面变薄,以便进行背面攻击。
- 这种方法通常用于需要从芯片背面进行攻击的场景。
热激光刺激Thermal laser stimulation
If a transistor is heated locally, a voltage is generated
No effect on high-ohmic transistors as ends are drains are floating.
Low-ohmic channel: increase in drain voltage effects source of the connected transistor当低电阻通道的漏极电压增加时,会影响连接的晶体管的源极。
这种电压变化会导致连接晶体管的电阻降低
Leads to decrease in resistance that is observable at the power supply pins of device.在设备的电源引脚上可以观察到电阻的减少。这种变化可以用来检测和分析SRAM单元的状态和工作原理。
Simple Power Analysis
Record single measurement for the attac
Leaked information is detectable in single trace
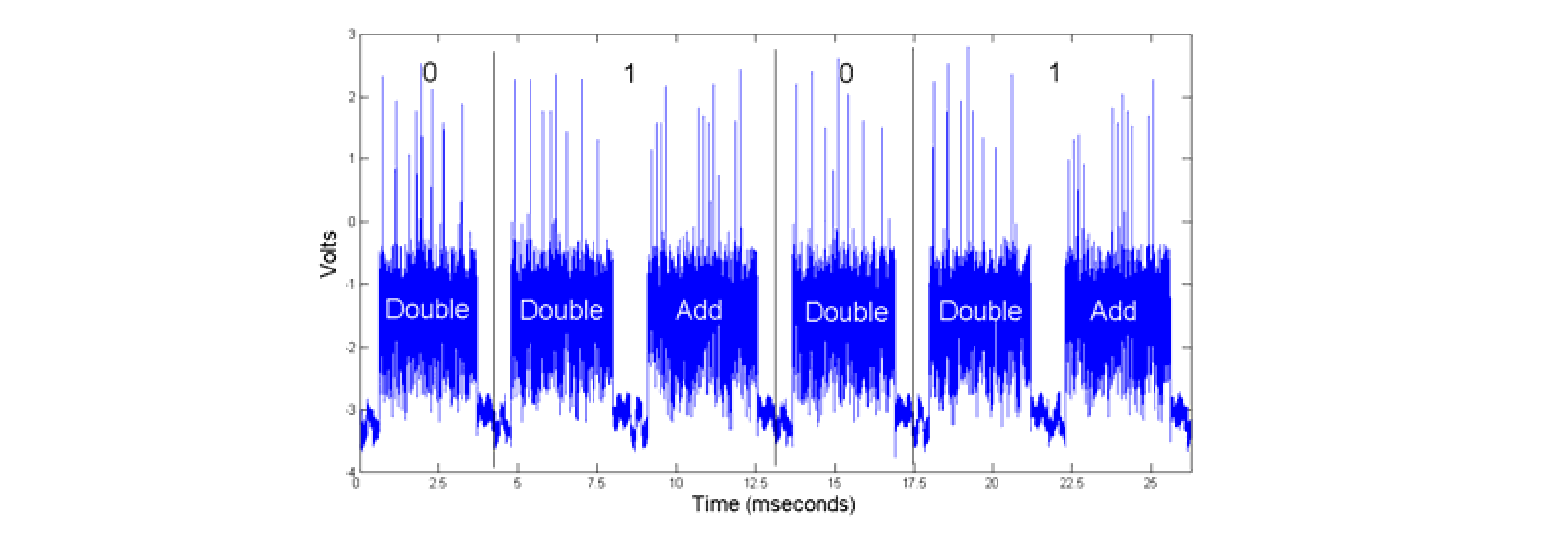
Some criteria affecting the measurements
- Target complexity: (Noise of other activities / components)
- Bare metal SW, small HW architecture.
- Large SoC
- SW / HW implementation (Number of involved logic gates and
registers)
- SW implementation
- HW implementation
- Manufacturing technology (Lower voltages and currents)
- Older / larger technologies
- Newer / smaller technologies
comparison
Differential Power Analysis
ECDSA椭圆曲线数字签名算法
For Alice to sign a message m
\(e=H A S H(m)\).
Let \(z\) be the \(L\) leftmost bits of e, where \(L\) is the bit length of the group order $ n$
\(k\) randomly from \([1,n−1]\)
Calculate the curve point \((x_1 ,y_1 ) = k × G\)
\(r=x_1 \bmod n\).
\(s=k^{-1}(z+r d) \bmod n\)
return \((r, s)\)
Differential Power Analysis
Record many traces, of device using same secret (This is mostly impossible for asymmetric cryptography)
Statistical analysis to distinguish correct key
Concentrate on differences between traces -> differential analysis
Hypothesis test
对于每一个 key guess
找一个bit 分为 0 和 1 两组
如果猜测正确, 那么根据CMOS理论,这两者的trace会由显著差距
Hypothesis testing: T test
T test computes the difference of the means of two distributions
Correlation-based DPA
- Correlation-based DPA uses multiple bits and power model
- Derive abstract values using ’power model’ and statistically compare relation to measurement
- (Hamming weight power model to derive values )Assumes that 1-s require more electrical current
- Pearson correlation coefficient for finding linear relations,If relation is statistically significant,key guess correc
DPA Properties
Robust against noise because many measurements can be used to ’average’ noise
Attack effort is given in number of measurements required for success
Practical problems
- Find out which algorithm is used
- Find out when it is used
- Synchronization of trace recordings
- With EM measurements (often required because of low SNR): Unknown time and unknown measurement position
Countermeasures
- Constant execution time of cryptographic operations
- Protocol-level countermeasures: Change key frequently
- Use algebraic structure for countermeasure
Most countermeasures come with performance penalty
Usually, countermeasures are combined (e.g. masking and hiding
Boolean masking
Split all binary variables a into two parts Choose masks \(m_a\) randomly such that \[ a_m=a+m_a \] If the attacker cannot or does not exploit the Pexp (vm) and Pexp (mv ) simultaneously, the implementation is secure against DPA
Masking
Use random value and XOR value onto processed data
Attacker cannot compute intermediate values needed for DPA
Hiding
Reduce SNR
Template attack
Characterization phase
- Attacker builds templates including mean and covariance matrix (m, C) v,k for different keys k and inputs v (intermediate values)
- Probability density function of the traces is estimated
attack phase
- Attacker measures a power trace and calculates p(t|(v, k))
- Key that leads to the highest probability is considered the correct key
Key rank estimation / security level
After an attack, how to determine the security level
Power models for DPA
- Bit: The bit value 假设处理 0 和 1 时的功率消耗不同。这个模型关注单个位的值。
- Hamming weight对于内存访问来说是一个有效的模型
- Hamming distance适合攻击寄存器中的过渡
- Zero value:零值的功率消耗与所有其他值不同。这个模型关注零值与非零值之间的功率差异。
- Profiled model: 使用实际测量的功率轨迹来计算均值和标准差,从而构建模型。这是最接近实际功率消耗的模型
Classification of SCAs
- Characterization of attacked device: Profiled, non-profiled with HD,HW
- Nr. of observations
- Nr. of variables in statistic analysis: Univariate, Multivariate
- Distribution of power value: Power consumption is assumed as Gaussian distribution, no assumption
Microcontroller Security
What sensitive data could be stored in a microcontroller?
- Intellectual property
- Personal data
- Credentials
- Licenses
What are threats for microcontrollers
- Product Piracy
- Cloning
- Tampering
What are attack vectors for microcontrollers
- Side-channels
- Fault injection
- Probing
- Logic attacks
Exception(al) Failure
“异常失败”一词指的是在系统或应用程序中遇到的特定类型的故障或漏洞,这些故障或漏洞通常涉及异常处理机制的失效或误用。这种失败可能导致系统行为异常,甚至可能被攻击者利用来进行攻击
利用异常的错误信息来攻击
TODO
Fault Attacks
Induce fault
Exploit reaction of device
Faults in circuit behavior
Digital circuits require certain operating conditions to work properly: temperature range,supply voltage
By changing the operating conditions, an attacker can change the state of the circuit
Effects of a fault
- The control flow: instructions are changed, skipped, …
- Data integrity: data values changed
Leading
- Arbitrary changes of the instruction pointer.
- Arbitrary changes of data in registers or memory
Temperature
Manufacturers define upper and lower temperature bounds, wherein the device operates correctly
Glitching
Clock Glitching
Digital circuits require a reliable clock source
If the clock period is too short, not all signals can propagate through the circuit in time
Voltage glitching
- Short interruptions of the power supply may cause misinterpretation or skipping of instructions
Electromagnetic fault injection
Inject faults by inducting currents via electromagnetic impulses
Advantages
Good timing control,No decapsulation necessary
Disadvantages
Less precise than lasers
Pulse duration longer than laser pulses
Body bias injection
通过在集成电路(IC)的衬底(substrate)上施加电压,以引发故障或影响电路的行为。这种方法利用了半导体器件的物理特性,尤其是二极管效应,来操控电路的工作状态。
- Open the package打开封装是为了能够直接对IC的衬底(substrate)进行操作
- Attach a coil and a pulse generator连接线圈和脉冲发生器
- Induce a pulse into the substrate of an IC
Laser fault injection
光电效应
- Photons transformed to energy when they hit an object (E = h * frequency)
光子携带的能量能够激发物体内的电子,导致物体的电荷状态发生变化。
Charges in semiconductor create electric field
Small current is induced
Assumption
Laser fault creates a an additional current
Missing charges compensated by load on \(C_{load}\)
If enough charge is missing output goes from 1 to 0
Properties of LFI
- Requires depackaging of the IC
- Can be carried out from the frontside or the backside
front side
allow use of shorter wavelengths -> increased precision
But: Metal layers reflect laser light
Backside attacks
offer open access to all parts of the circuit
But: Requires use of infrared light to pass through silicon substrat需要使用红外光来穿透硅基板,这可能需要额外的设备和技术支持。
Rowhammer attack on DRAM
When a wordline in DRAM is repeatedly toggled, nearby rows leak charge through electromagnetic coupling
基本机制:当 DRAM(动态随机存取内存)中的一个字线(wordline)被重复地切换(切换表示读取或写入操作)时,附近的行会通过电磁耦合泄漏电荷。
重复访问:如果对一个地址进行足够多的访问(例如,约 10,000 次),这些附近的行在行刷新(通常是每 64 毫秒)之前,可能会发生值的变化
- Allows to circumvent memory protection
- Can be executed remotely
Fault models
- Characterize assumptions for attack / abilities of adversary 故障模型用于描述攻击者的假设和攻击能力。它定义了攻击需要哪些特性来成功实施故障攻击
- Attacks require certain fault model properties
- Affected bits specific or random, local or global, single or multibit
- Effect - bit flip (toggle), fixed state (always 1 or 0) or inconsistent
- Permanence permanent alteration or transient effect
- Timing precision random, loose or precise timing
Comparison of attack techniques
Fault attacks on cryptographic algorithms
Classification
- Differential fault attacks
- Safe error fault attacks
- Algebraic attacks
Simple example DFA
Induce fault 把key的某一bit变成0
然后比较结果,如果改变了,那么这一位是 1
Fault Attacks on ECC
改变 \(Q_{ki}\) 如果结果变量, 那么就知道 \(k_i\) 的值了
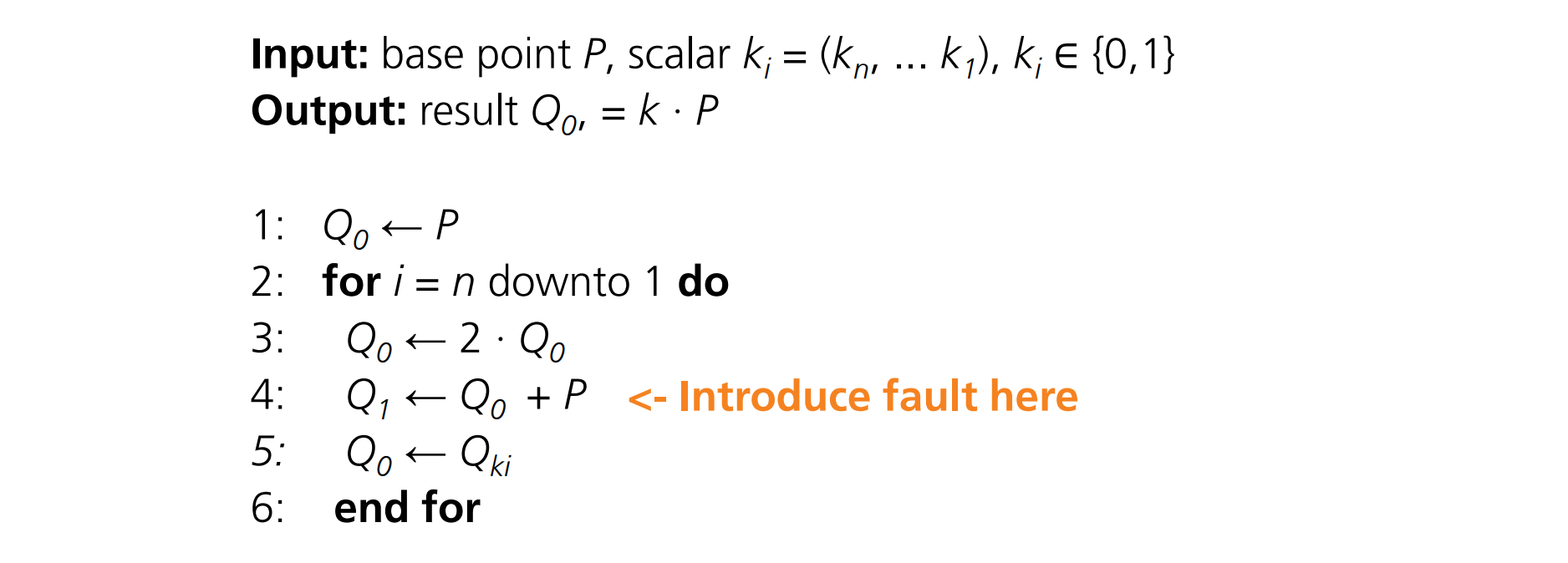
Montgomery Ladder
Introduce fault in \(Q_1\)

故障影响分析:
当
\(k_i=0\)
时:
- 计算 \(Q_1←Q_0+Q_1\)
- 计算 \(Q_0←2⋅Q_0\)
- 由于 \(Q_1\) 被正确的结果覆盖,因此故障不会影响最终结果。
当
\(k_i=1\)
时:
- 计算 \(Q_0←Q_0+Q_1\)
- 计算 \(Q_1←2⋅Q_1\)
- \(Q_1\) 保持故障状态并输出错误,因为它没有被正确的结果覆盖
Weak-curve fault attacks
Invalid point attack
Modify input base point P to P’ through fault
P’ has low point order on a weak curve
Countermeasure: Point validity check:
Invalid curve attack
Modify curve parameters
ECDLP can be solved computationally
Countermeasure: Curve integrity check:
Differential fault attack on AES
Fault Models
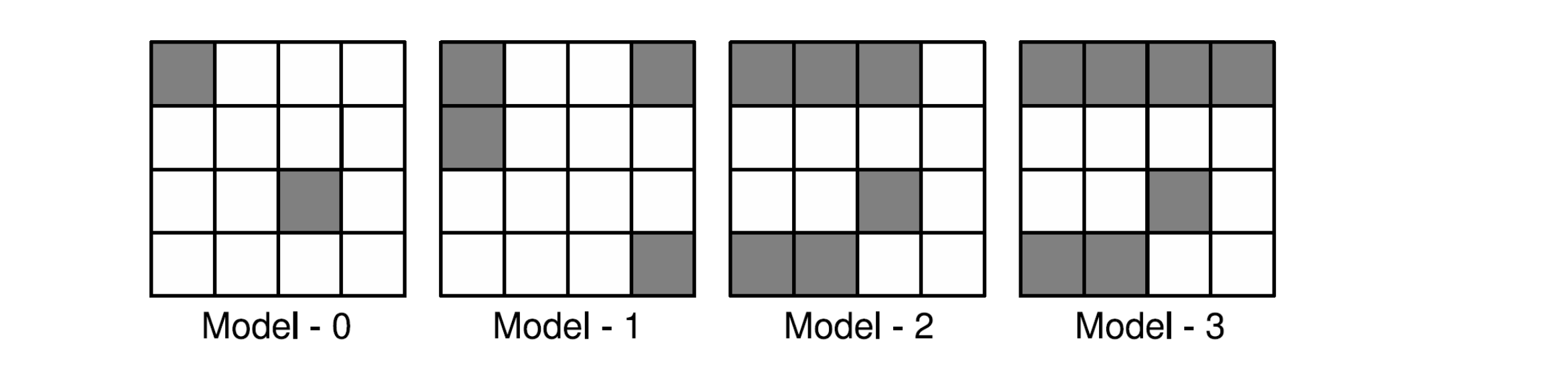
Model i: \(Mi\), A random non-zero fault occurs at most across \(i\) diagonals.
Key equations
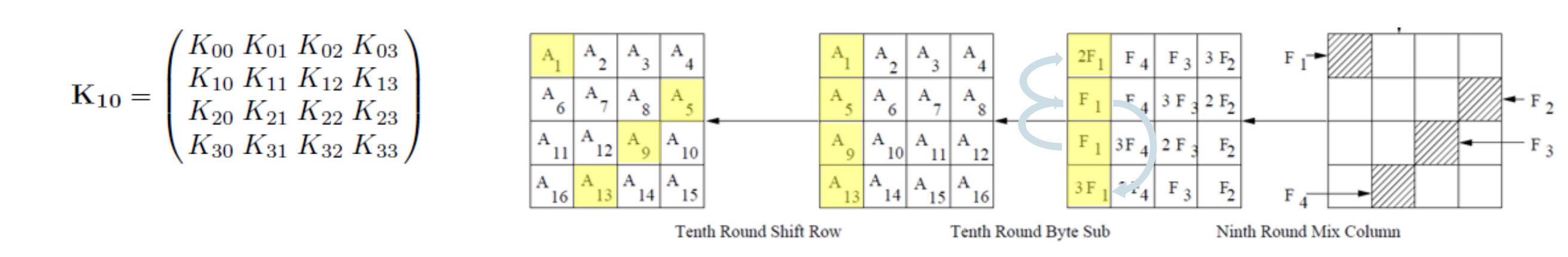 \[
\begin{aligned}
I S B\left(x_1+K_{00}\right)+I S B\left(x_1+A_1+K_{00}\right) &
=2\left[\operatorname{ISB}\left(x_8+K_{13}\right)+I S
B\left(x_8+A_5+K_{13}\right)\right] \\
I S B\left(x_8+K_{13}\right)+I S B\left(x_8+A_5+K_{13}\right) & =I S
B\left(x_{11}+K_{22}\right)+I S B\left(x_{11}+A_9+K_{22}\right) \\
I S B\left(x_{14}+K_{31}\right)+I S B\left(x_{14}+A_{13}+K_{31}\right)
& =3\left[\operatorname{ISB}\left(x_8+K_{13}\right)+I S
B\left(x_8+A_5+K_{13}\right)\right]
\end{aligned}
\]
\[
\begin{aligned}
I S B\left(x_1+K_{00}\right)+I S B\left(x_1+A_1+K_{00}\right) &
=2\left[\operatorname{ISB}\left(x_8+K_{13}\right)+I S
B\left(x_8+A_5+K_{13}\right)\right] \\
I S B\left(x_8+K_{13}\right)+I S B\left(x_8+A_5+K_{13}\right) & =I S
B\left(x_{11}+K_{22}\right)+I S B\left(x_{11}+A_9+K_{22}\right) \\
I S B\left(x_{14}+K_{31}\right)+I S B\left(x_{14}+A_{13}+K_{31}\right)
& =3\left[\operatorname{ISB}\left(x_8+K_{13}\right)+I S
B\left(x_8+A_5+K_{13}\right)\right]
\end{aligned}
\]
ISB 是 inverse Sub Bytes
\(ISB(x_1+K_{00})+K'_{00}+ISB(x_1+A_1+K_{00})+K'_{00} = ISB(x_1+K_{00})+ISB(x_1+A_1+K_{00})\)
因为 xor 就是 +, 所以 Addroundkey 第九轮没有了
Remaining key space using all the equations above: \(2^{32}\)
Fault sensor
- 光检测器(Light Detectors)
光检测器用于检测光的梯度变化。当有光照变化时,传感器会感知到这种变化,从而触发相应的安全措施。这类传感器主要用于防止激光注入攻击,因为激光注入会改变光的梯度。
- 电源电压检测器(Supply Voltage Detectors)
电源电压检测器对电路中电压的突然变化作出反应,确保电压始终在电路的容忍阈值内。如果检测到电压超出容忍范围,系统将采取措施,如重启或进入安全模式,以防止故障攻击。
- 频率检测器(Frequency Detectors)
频率检测器强制电路在特定的操作频率范围内工作。如果电路的操作频率超出预设范围,电路将自动重置。这类传感器主要用于防止时序攻击,通过确保电路运行在安全的频率范围内,避免由于时序变化引发的故障。
- 主动屏蔽(Active Shields)
主动屏蔽是一种覆盖整个芯片的金属网格,网格中持续传递数据。如果网格发生断开或修改,芯片将停止运行。主动屏蔽主要用于防止探测攻击,但同时也有助于保护芯片免受故障注入攻击,因为它使得定位电路中的特定模块变得更加困难。
Selected HW countermeasures
- Duplication / multiplication with comparison
- Time redundancy with comparison在不同时间段执行相同的计算操作,并对比结果。例如,在一次计算完成后,稍作延迟,再进行相同的计算,然后比较两次结果是否一致
- Recomputing with swapped operands
SW countermeasures
Complement hardware countermeasures ,Protection against future attack techniques,Do not increase the hardware block size
- Checksums, Randomization
- Variable,Execution redundancy
- Ratification counters and baits通过插入小的代码片段进行验证操作。例如:验证计数器:在关键操作前后使用计数器,确保操作次数正确。
- Dummy Operations在关键操作之间插入一些虚操作,这些操作不会改变实际结果,但会增加攻击者推断实际操作的难度。
- Calculate the Result and Then Compute Back 通过计算结果并进行逆运算来验证输入的正确性
Control flow integrity through sponge-based control-flow protection
Detection: random instruction after decrypt stage在程序的解密阶段(或关键计算阶段)之后插入随机指令,可以用来检测是否发生了控制流篡改。具体来说,当程序执行到这些随机指令时,它们应当不会改变程序的实际逻辑,但如果攻击者尝试通过篡改指令流来绕过保护,这些随机指令的执行结果将会出现异常。
Address:
- Corrupted communication in memory and instruction fetch
- Tampering with the processor core
Sponge-based control-flow protection
是一种通过使用基于状态的哈希函数来确保程序控制流完整性的方法。这种保护机制主要用于防止攻击者通过操控程序的控制流来执行恶意代码。
在控制流程加入patch, 用这个patch更新哈希函数, 最后检验指令的流程的哈希值是否是预期的
- Additional patches introduced for indirect calls
- Four patches vs one to avoid undesired collisions into SCFP state
为了避免碰撞,可以使用四个不同的补丁,分别处理不同类型的控制流转移
Secure Processor Architectures / FPGAs
Authentication Token
- Passwords are frequently exploited
- Second authentication factor helps
Architecture of OpenTitan
- Open source project for a secure element
- Mixture of open digital an proprietary analog components
Examples for Customizing OpenTitan
- Removal of internal NVM („flashless“)
- Post-quantum secure boot
- Cryptographic key isolation
- Authenticated debug
Post-quantum secure boot
- Leighton-Micali Signatures (LMS) : Hash-based signature
- LMS Rust implementation
- LMS hardware accelerator
- Dilithium Support for OpenTitan
Field programmable gate arrays (FPGAs)
Devices with configurable digital logic
Secure Boot
Two software authorities
Monotonic incrementing serial numbers to implement certificate revocation
Key Management
Strong cryptographic keying material required to protect sensitive information
Unique device secret stored in one-time programmable memory
Used to implement TCG’s Device Identifier Composition Engine (DICE)
Secure Update
Software vulnerabilities are difficult to avoid, a secure update mechanism is important
Software update mechanism alone is not sufficient
Additional control of device with the authenticated watchdog timer
Authenticated Watchdog Timer
The typical watchdog timer
The authenticated watchdog timer is similar, but with important differences
Memory Encryption and Enclaves
Memory encryption
- CPU: data and addresses in plaintext only
- Plaintext + ciphertext buses with encryption modules in between
Disk encryption
XEX-based tweaked-codebook mode with ciphertext stealing (XTS)
Enclaves安全区
安全区(enclave)是现代计算系统中的一种安全机制,它提供了一个隔离的执行环境,用于保护敏感数据和代码免受外部攻击或未经授权访问。
Protected mode (rings)
Trusted Execution Environment (TEE)
Goal of implementing enclaves
- Authenticate itself (device)
- Authenticate software
- Guarantee the integrity and privacy of remote execution
different enclaves
深色是trusted componet
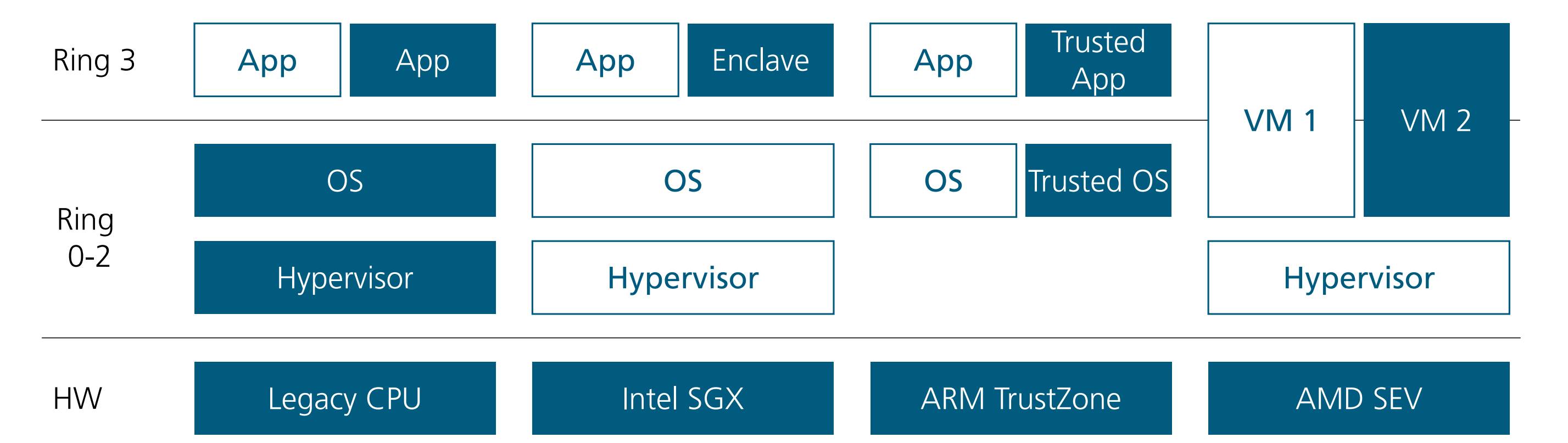
Other TEE
- AMD SEV
- ARM TrustZone
Why do we need an open-source enclave?
Existing enclave systems are proprietary and difficult to experiment with
A lot of challenges for enclaves
Open source design
- Provides transparency & enables high assurance
Keystone: Open framework for secure enclaves
- The first full-stack open-source enclave for minimal requirements
- Open framework: built modular & portable for easy extension
Minimum set of hardware
- RISC-V Physical Memory Protection (PMP)
- RISC-V U(ser)-, S(upervisor)-, and M(achine)-mode
- Entropy source available at boot time
- Root of trust (preferably a crypto engine)
- If untrusted/external DRAM –memory encryption/integrity engine
Demonstrated in unmodified processors为了在未经修改的处理器上实现安全区和其他关键安全功能,上述硬件组件是必不可少的。
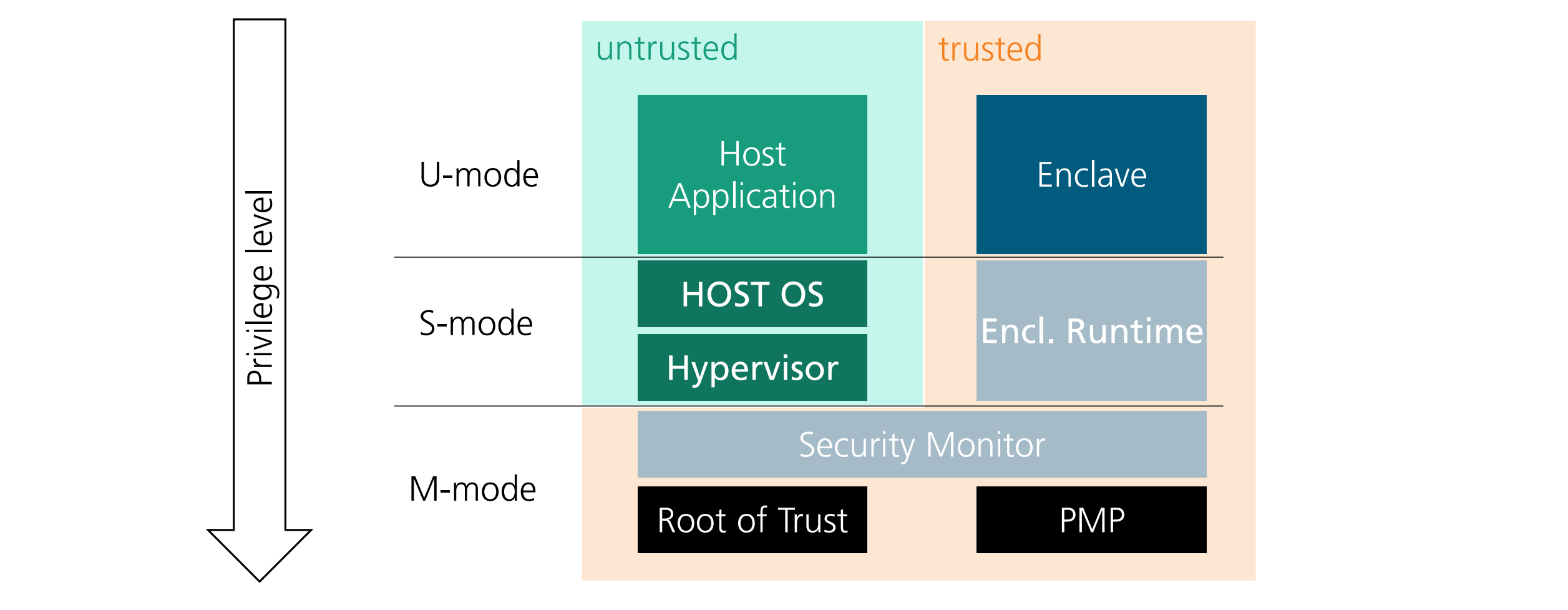
Memory isolation with the RISC-V PMP
- Special registers to control permissions of U-and S-mode accesses to a specified memory region
- Whitelist-based
- Dynamically configurable by M-mode
为了支持多个并发运行的安全区,每个“活动”的安全区都对应一个 PMP 条目。
S-Mode enclave runtime
Provides kernel-like functionality: Syscall, traps,Thread and page table management
Useful layer of abstraction
S-模式运行时提供了一个抽象层,使得用户模式(U-mode)代码只需要最低的权限来执行。这种设计方式极大地减少了代码执行的权限,降低了潜在的安全风险
通过在S-模式提供额外的功能,运行时避免了直接在安全监控(SM)中添加复杂性。
Remote attestation
远程认证是一种确保远程系统可信性的技术,特别是在创建安全区(enclave)时,RISC-V的安全监控(SM)执行特定步骤来实现这一目标
- measure the enclave 在创建安全区时,安全监控(SM)会测量该安全区。这一测量过程通常涉及计算安全区代码和数据的哈希值,以生成一个唯一的标识
- Enclave may bind a key to the enclave report
- SM signs the enclave report and hands it (+ SM report) to the user
比如 在用户发起交易时,安全区可以生成一个经过签名的报告,证明交易数据和身份验证的真实性,远程银行服务器可以验证该报告以确认交易的合法性。
Secure enclaves in a speculative out-of-order processor
- Forbid resource sharing between enclaves禁止资源共享
为了防止不同安全区之间的资源共享,从而避免潜在的安全漏洞,例如缓存集合在不同安全区之间共享带来的数据泄露风险,MI6的设计禁止了这种资源共享。这类似于操作系统中不同特权级别之间的隔离机制。
- Slowdown by not using speculation in the entire program禁用投机执行
在现代处理器中,投机执行是一种常见的性能优化技术,通过提前执行可能会用到的指令来提高性能。然而,这也带来了安全风险,例如Spectre和Meltdown攻击。MI6通过完全禁用投机执行来提高安全性,但这会导致约3倍的性能下降。
- All modules with private state are flushed on enclave entry and exit.私有状态刷新
在进入或退出安全区时,所有具有私有状态的模块(例如缓存、寄存器)都会被刷新,以防止信息泄露。这种操作会带来大约5%的性能开销,但显著提高了安全性。
- Last Level Cache is spatially partitioned.末级缓存空间划分
为了进一步提高安全性,末级缓存(LLC)被空间划分,这意味着不同安全区之间不会共享同一个缓存区块,从而减少了缓存侧信道攻击的可能性。这种划分带来的性能开销大约为7%。
- Area overhead for hardware modifications硬件修改的面积开销
为了实现这些安全特性,需要对处理器进行一些硬件修改。除了一级缓存、浮点单元和末级缓存切片之外,这些修改带来的面积开销大约为2%。
Summary
Open source enclaves reduce the TCB to hardware, security monitor and app通过开源安全区,可以将信任计算基(TCB)缩减到硬件、安全监视器和应用程序。
Limited required hw security features 开源安全区所需的硬件安全特性较为有限,这意味着它们可以在各种硬件平台上实现
Provide a larger flexibility than fixed TEEs相对于固定的可信执行环境(TEEs),开源安全区提供了更大的灵活性
Random Number Generation
Data processing inequality
The entropy of a random variable cannot be increased by any deterministic operation
True Random Number Generators (TRNGs)
Noise source: Root of security for the entropy source and for the RBG as a whole.
Conditioning: removes bias in raw data去除原始数据中的偏差。
常用方法包括块密码和哈希函数
Health test during startup and operation
Pseudo Random Number Generators (PRNG)
- Entropy input, seed, and later internal state, need to be kept secret
- Process state (‘generate’) with hash function or block cipher
- Reseeding重新播种的目的是限制已泄露种子的影响,克服生成函数的局限性,增强PRNG的安全性。
- Enables high throughput!
suppose that an adversary knows \(State_x\) .
- Backtracking resistance:Use a one-way function
- Prediction resistance: Can only be addressed by reseeding
环形振荡器真实随机数生成器(RO TRNG)
Ring Oscillator
Noise leads to jitter(抖动) in the oscillation (振荡)
XOR creates merges multiple inputs to one random response
RO TRNG通常使用多个环形振荡器的输出信号。
这些信号通过异或(XOR)操作合并到一起,生成单一的随机输出
Secure key storage and PUFs
Secure key storage
Read-only memory (ROM)
里面的值是出场决定的, 不适合作为key存储,因为可以读取
Fuses熔丝
- Metal eFuse blown by high-density current
- Bone-type layout -> area in the middle is blown电子熔丝通常采用骨型布局设计,即中间区域较窄,方便在编程时通过高密度电流将其吹断。
- Can be programmed bit by bit
- Programming creates an open circuit编程时,通过施加高密度电流,使特定位置的熔丝吹断,形成永久性开路
Anti fuses
- State not visible externally 状态不会被外界看见
- Programming establishes a connection反熔丝通过编程过程建立电连接。与电子熔丝(eFuse)通过高密度电流吹断金属形成开路不同,反熔丝是通过高电压或高电流使绝缘材料击穿,形成永久性导电路径
Physical Unclonable Functions
Example: Arbiter PUF
Based on different latency of signals, Arbiter will output 0 or 1. Due to phisical unclonability, arbitor PUF provided property of unforgerability.
信号在两个延迟链中传播,由于制造过程中微小的工艺差异,每个链路的总延迟会略有不同。
仲裁器决策:仲裁器根据两个链路的延迟差异决定输出值,通常输出为 0 或 1。
唯一性:仲裁器 PUF 可以生成唯一且不可克隆的响应,用于芯片认证,确保每个芯片都是唯一的。
防伪造:由于物理差异难以克隆,仲裁器 PUF 提供了防伪造的机制
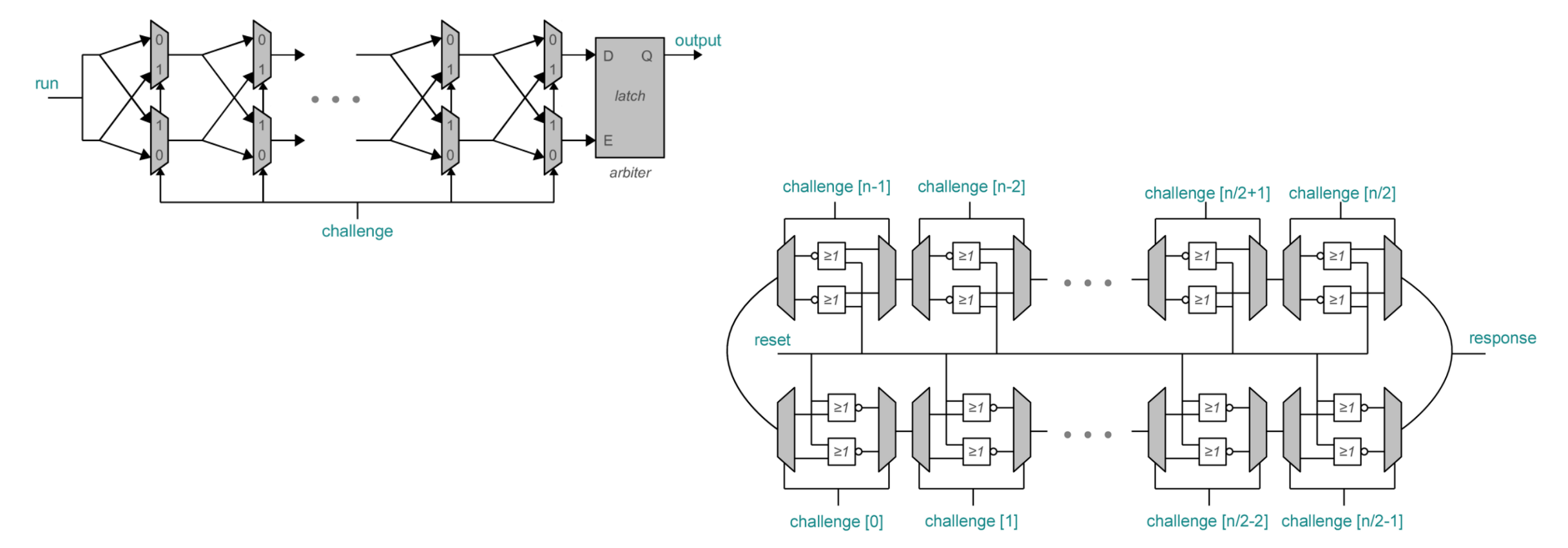
Basic PUF authentication
设备 A(验证者)生成一个随机的挑战,并将其发送给设备 B(被验证者)
设备 B 使用其 PUF 计算出对应于挑战的响应
设备 B 将计算出的响应发送回设备 A。
设备 A 比较收到的响应和预期的响应。如果两者匹配,设备 B 的身份就被验证。
- Machine learning attacks if too many challenge-response pairs were exposed
锁定协议 (Lockdown Protocol)
防止ML Attack,每次给\(c||r_1\) , 如果不对的话就不回复了,Attacker就拿不到CR pair
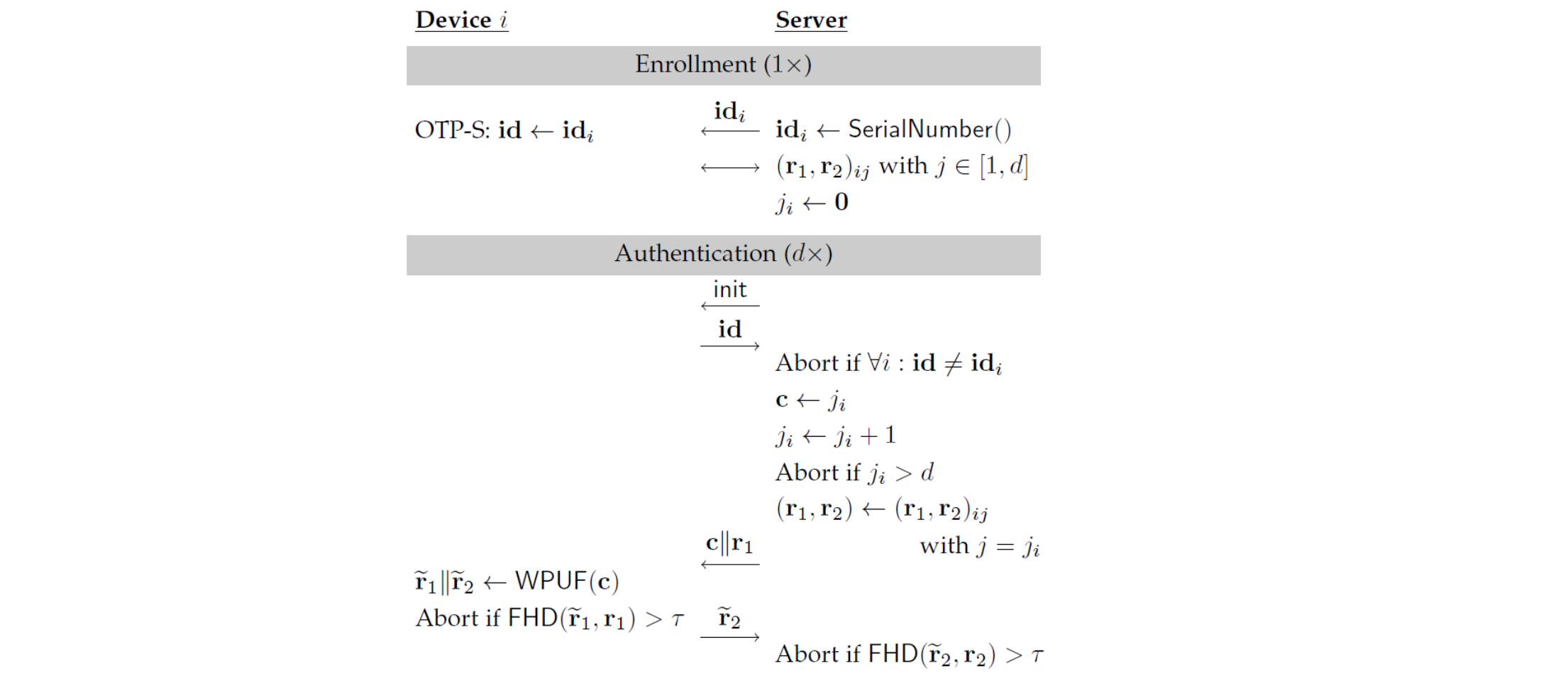
Low-cost authentication
- No crypto algorithm needed
- Implementation e.g. in stand-alone RFID tags通过在每个产品上附加低成本RFID标签
- Possible Applications: Supply chain tracking,Counterfeit伪造品 detection for consumer goods
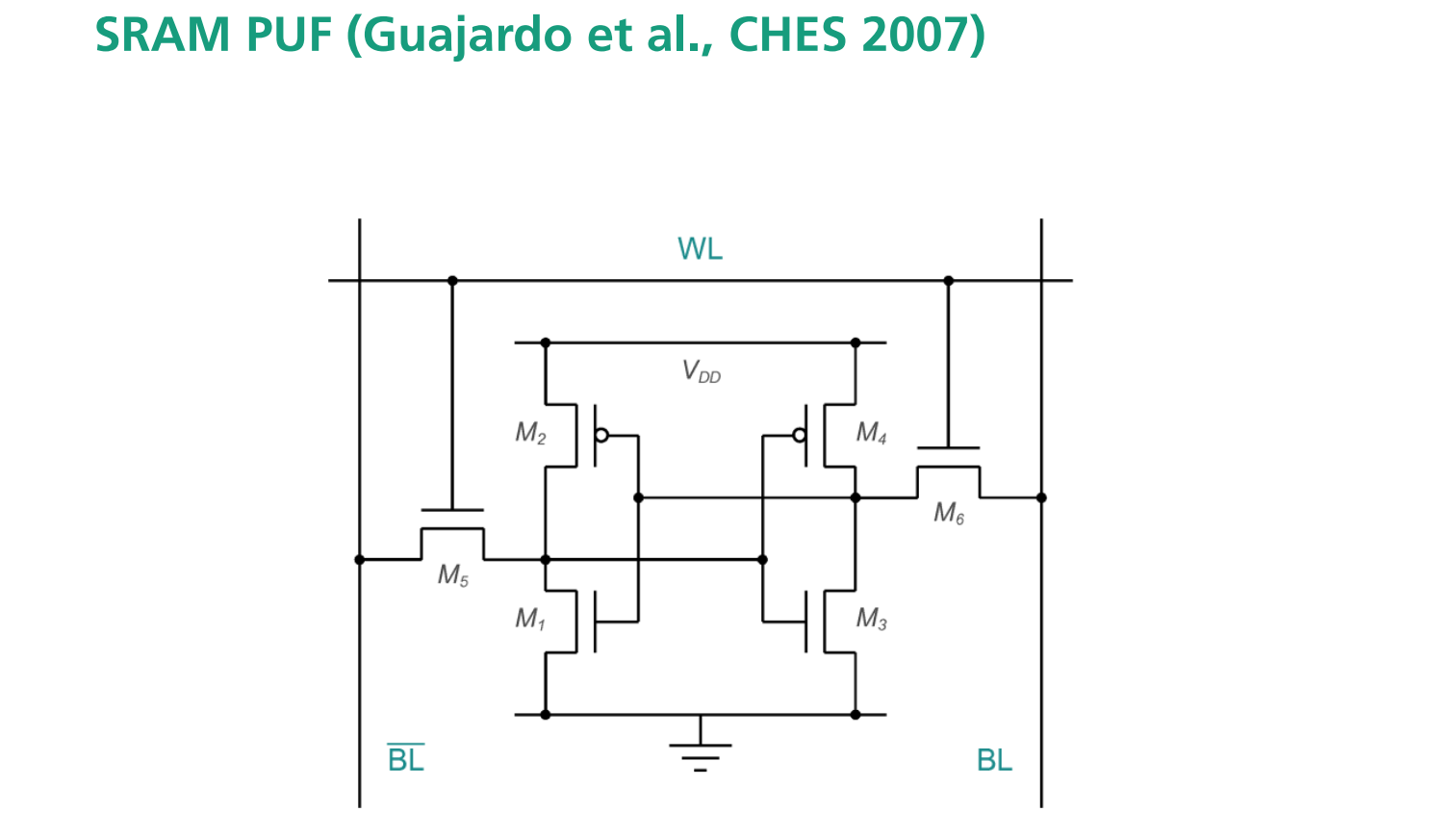
PUFs used for key generation
是一种基于SRAM存储单元的物理不可克隆函数。它利用了SRAM在上电初始化时的随机行为,当SRAM单元上电时,每个单元会随机地稳定在0或1状态,具体取决于晶体管的物理差异生成独特的硬件指纹
有 \(n\) 个 oscillators, 他们产生frequency通过multiplexer变成2个counter, 然后比较哪个大. Challenge 来选择哪个oscillator通过 multiplexer
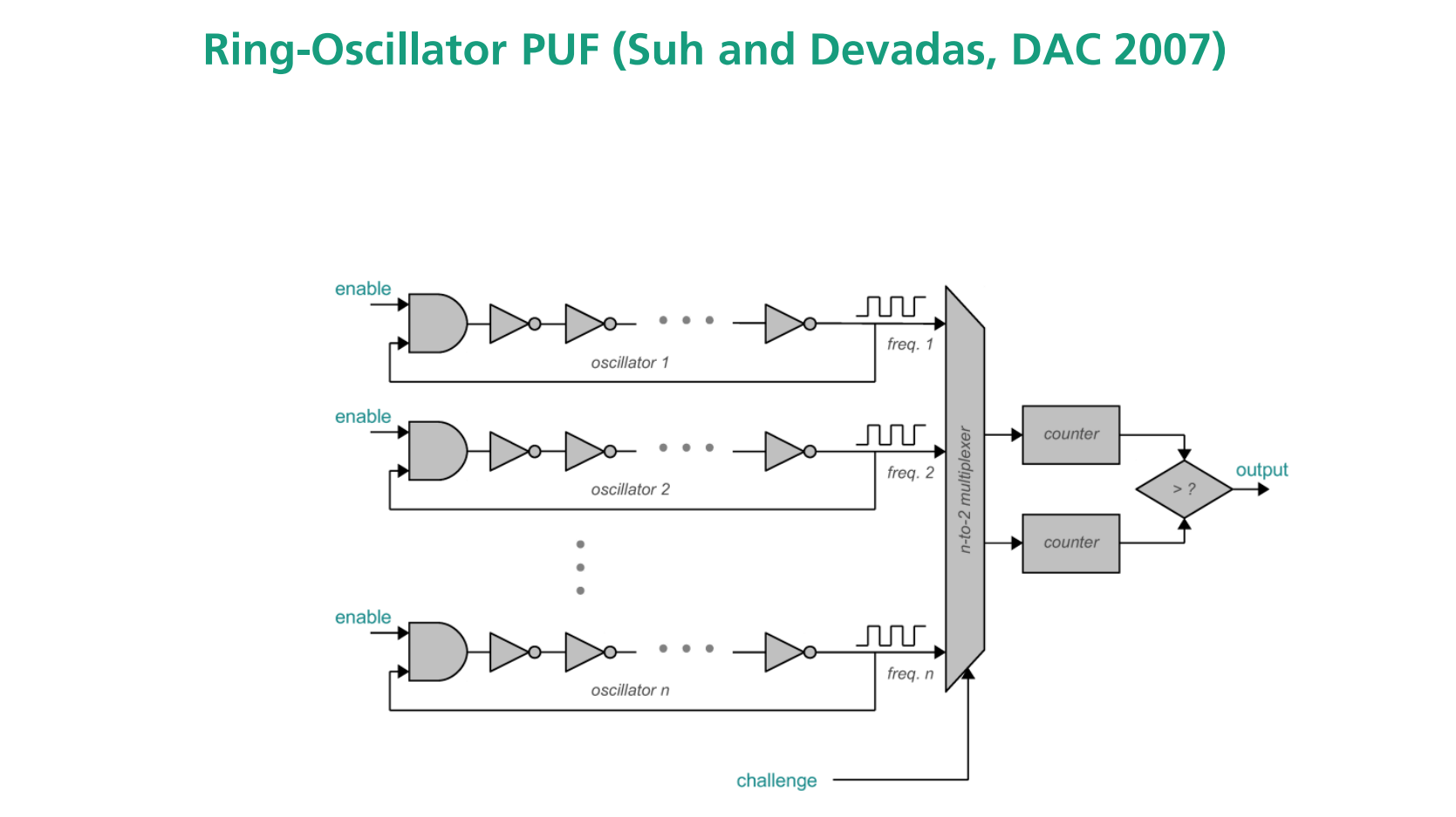
PUF keys + crypto algorithm
- Read out unique PUF reponse
- Replaces permanent key storage
- Apply standard cryptographic algorithm
PUFs for key storage – Idea
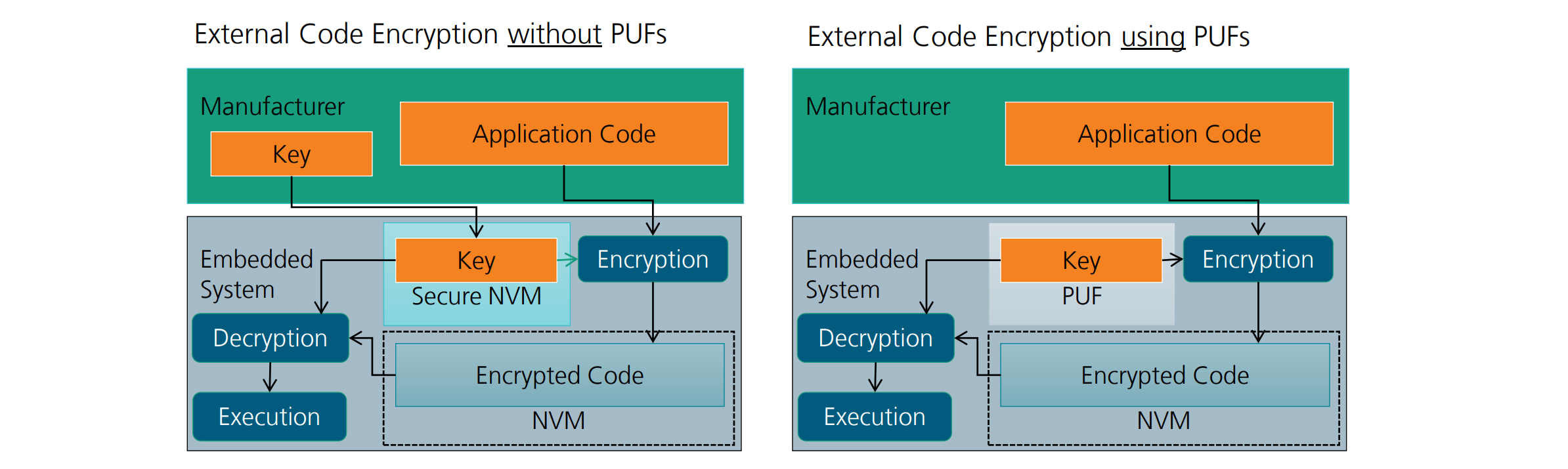
- No secured Non-Volatile Memory (NVM) → lower cost安全的非易失性存储器(NVM)
- Secret (Key) only available at runtime → harder to attack
- Can be realized if no secured NVM is available
Measuring RO Frequencies
- std shows: not i.i.d (often assumed)标准差表明这些频率数据并不是独立同分布
- Mean shows: not every pair is balanced这种不平衡可能导致偏差,进而降低熵(entropy)
在使用环形振荡器(RO)实现的物理不可克隆函数(PUF)时,频率测量是关键的一步
Temperature coefficients
Not the same everywhere -> variations in PUF response over temperature
Insights into specific device (where to place ROs),RO的位置选择对于PUF的性能和稳定性有重要影响
Modeling: use measured properties to model PUF performance before actually measuring it
Bit-Alias评估需要大量的PUF实例,这在实际设备中实现是不可行的。通过建模和仿真,可以生成大量虚拟PUF实例,进行Bit-Alias评估
use model to simulate required sample size
PUF-based tamper protection
- goal: detect and counteract physical access
- 篡改检测(Tamper-Detection)
- 篡改响应(Tamper-Response)
- 零化(Zeroization)在检测到篡改事件后,系统会立即清除敏感数据,以防止攻击者获取
确保即使在设备断电的情况下,篡改检测系统仍能工作
Our approach: a PUF-based envelope – no battery required!
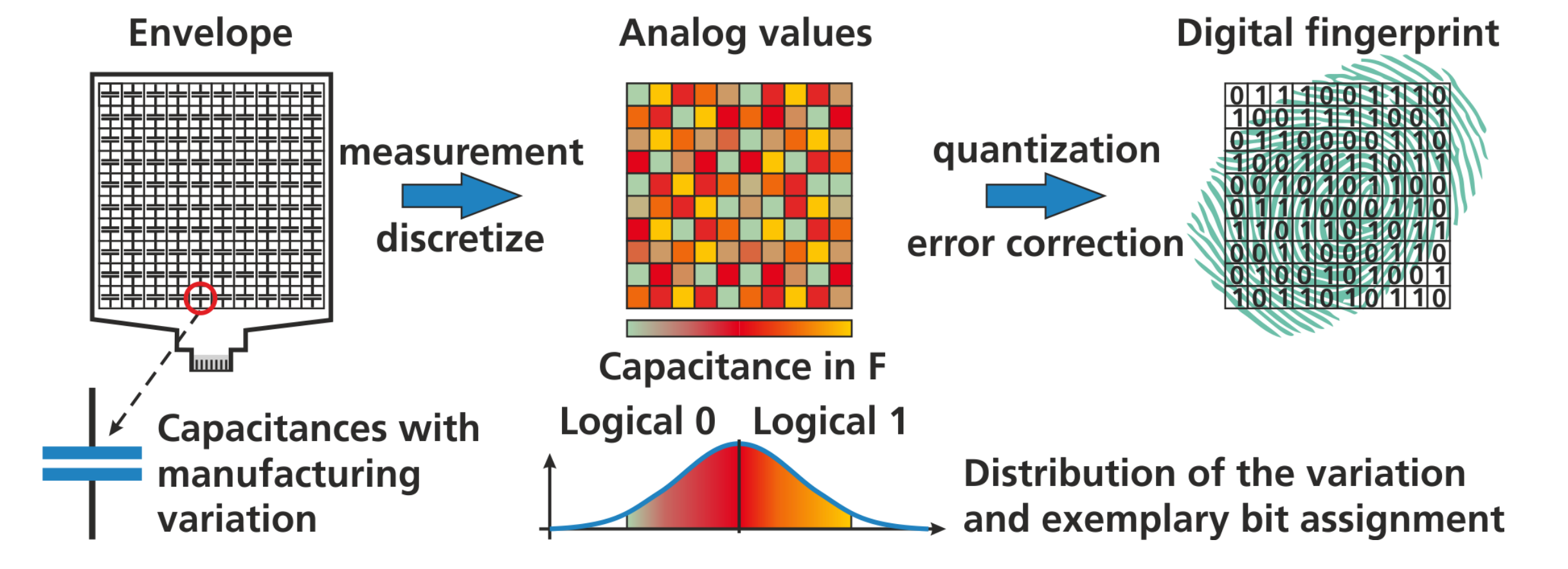
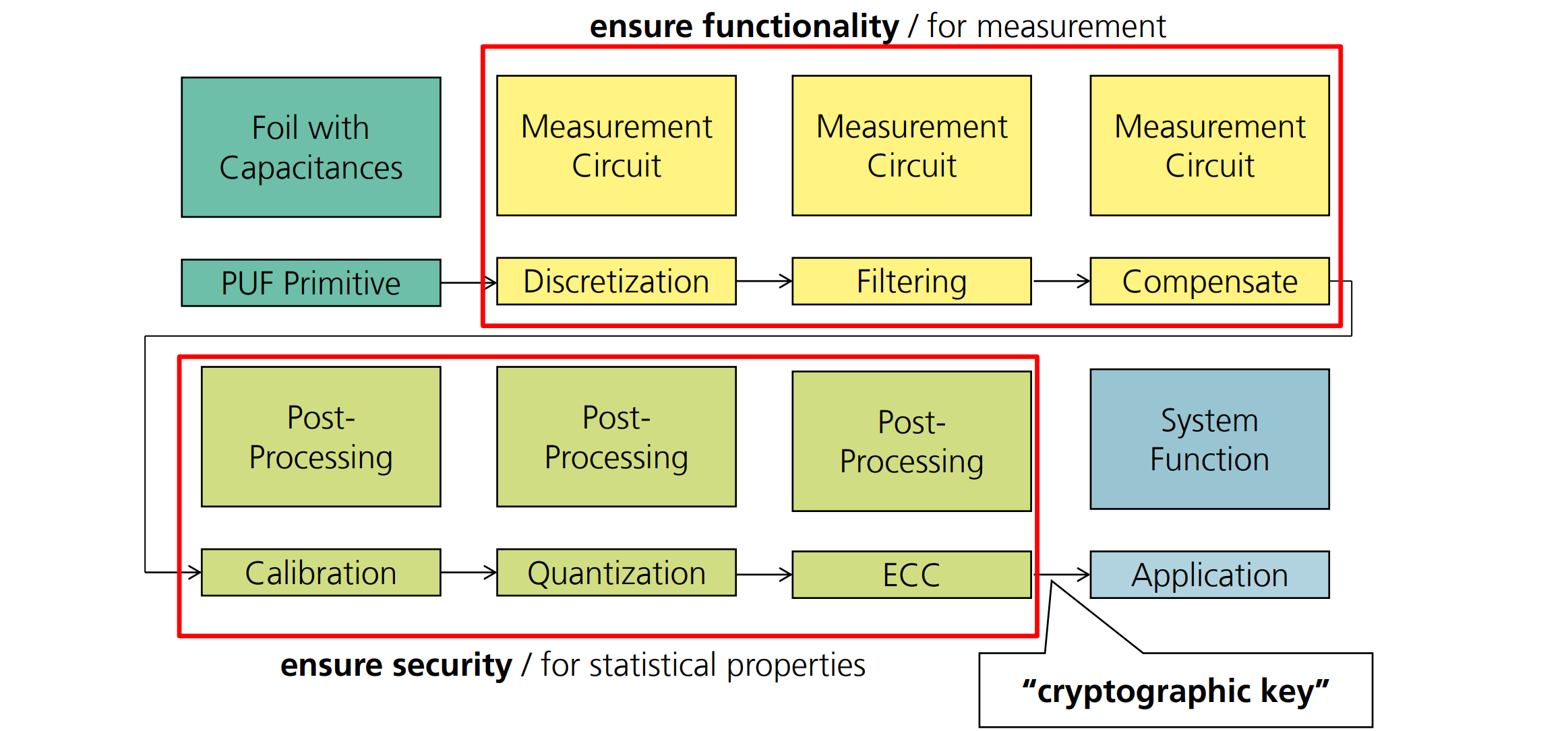
Postprocessing
用于从PUF生产cryptographic key
Trusted Electronics可信电子产品
fulfill requirements on quality and reliability 设备在整个使用寿命期间都能可靠运行。
确保在各种环境和条件下保持稳定和可靠的性能。
implement a known and complete specification设备严格按照规定的规格进行操作。
设备仅执行规格中定义的功能,不包含可以用作后门的功能。
规格中的功能在供应链中不会被后续修改
must be sufficiently hardened against attacks that change the functionality without the consent of the user防止未经用户同意的功能修改
设备需要在规格中包含安全机制。
当面对恶劣环境时,不会暴露规格外的弱点。
实现攻击通常利用规格外的属性进行攻击,因此设备必须防范此类攻击
Threats to electronics devices
- Weaknesses弱点是由于设计或制造过程中产生的错误或缺陷。这些弱点在设备的整个生命周期中可能被恶意攻击者利用
- Backdoors后门是恶意行为者故意植入设备中的隐蔽功能或漏洞,目的是在特定情况下进行利用。
- Gray-market hardware灰色市场硬件包括假冒、低质量或标签错误的设备或组件。这些非正品硬件进入供应链会导致一系列问题,包括设备性能不稳定、故障率高、甚至存在安全隐患。
Electronics value chain
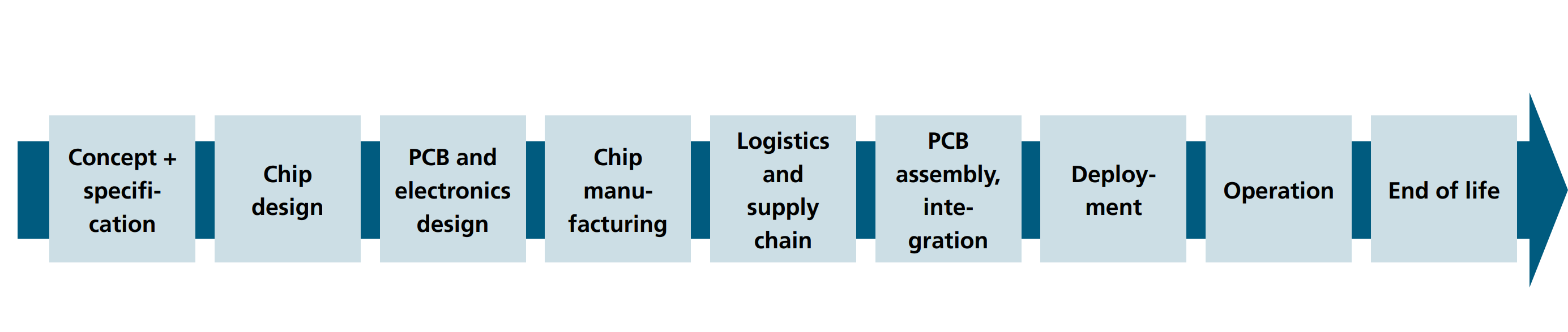
Threats along the value chain
Concept and specification,
- Incomplete or incorrect specification
- Intentional weaknesses in specifications and standards
Chip design
- Implemetation mistakes
- Ambiguous functionality
- Implementation attacks outside threat model during design time
- Design tool optimizations that remove security functionality
backdoor
- Intentionally introduced implementation errors or backdoors in in-house developments or 3rd party IP
- Design tool modifications for vulnerabilites or backdoors
PCB and electronics design
- Exposed external interfaces
- Unintentional side channels
backdoors
- Intentional side channels
- Trojan ICs and interfaces for trojan ICs
Chip manufacturing
- Undetected errors in design and mask data
- Process deviation from the specification
backdoors
- Tampering with design and mask data
- Process deviation from the specification
Gray-market hardware
- Overproduction
- Source for relabeled chips
IC logistics and supply chain
Gray-market hardware
- Reentry of discarded chips
- Source for relabeled chips
End of Life
Reverse engineering instead of recycling / destruction
Source for recycled chips
Exercise
- drow secure system architecture
SCA
- Method to Decapsulation, why need decapsulation
PUF
- why ROM not good for key storage
- describe fuse, anti fuse
- describe Arbiter PUF
- what is good for low cost authentication
- usage of low cost authentication
- why use PUF for key storage
Enclaves
- requests to implement enclaves
- goal of enclaves
- ways to realize Backtracking resistance and Prediction resistance
Secure prosessor
- root of trust
