网络空间安全
Netzsicherheit
作业
Hack 进入作业的服务器
1 | nc netsec.net.in.tum.de 20001 |
Exercise 1
首先安装一下 netcat
1 | sudo pacman -S netcat |
base64加密解密
1 | import base64 |
Networt Insecure
Do not Trust a Network Connection
网络是不安全的
Capabilities of Attackers
- Passive attacks (observation)
- Eavesdropping of messages
- Traffic Analysis
- active attacks (observation + manipulation)
- All passive attacks
- Delay
- Replay
- Deletion
- Modificatioin
- Insertion
Attacker Model
- Attacker Model = definition what an attacker can do and cannot do
- Dolev-Yao attacker model: (以后都以这个模型为基准)
- The attacker owns the entire the network
- can perform any active and passive attack
- has no control over end systems
- cannot break cryptographic primitives
The Attacker's Positon
determines her Capabilities
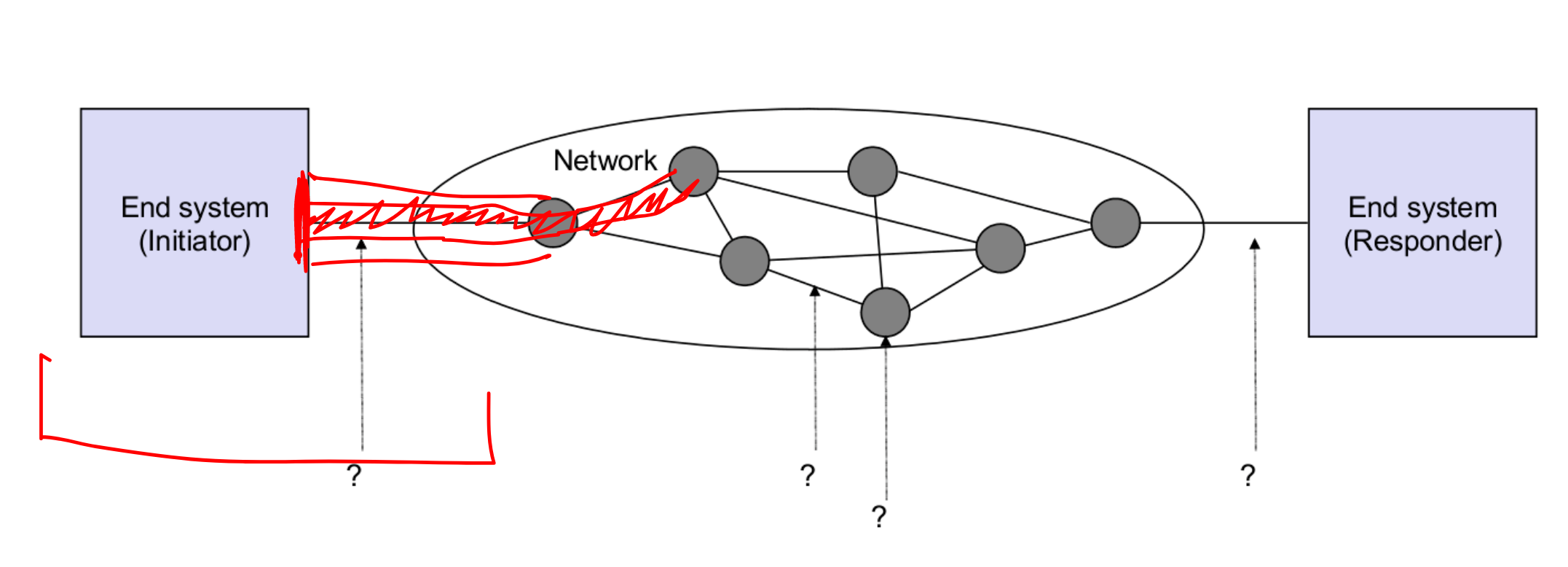
比如处在这个位置的攻击手是一个 WiFi 热点.
如果攻击收是在 Internet 中间位置
- End-user/attacker has no control on how packets are routed
- NSA/GCHQ black boxes can be basically everywhere
如果攻击手在end system(Responder)
Attacker rented a VM on the same host machine where your virtual server is running
攻击手和服务器在同一个位置
Security Goals Technically Defined
Confidentiality
- Vertraulichkeit
- Informatino must be concealed -> Attacker cannot read/understand information
- Can be achieved with : Encrypt information
Data Integrity
- Datenintegritaet
- changes to data must be noticeabe
- Can be achieved : Hash value of a file
Authenticity
Echtheit
We must know who the originator of data our communication partner is
Can be achieved: A digital signature over the hash of file
Controlled Access
- Zugriffskontrolle
- Only authorized entities can access services
- Empoly an access control system, firewall
Accountability
- Zurechenbarkeit
- Identify the entity responsibile for an event
- Employ a logging system
Availability
- Verfuegbarkeit
- Service must be avaliable and function correctly
- Important servives shall be replicated redundandly
区别 Authentication 和 Authorization
- Authentication
- Prove who you are
- associated security goal: Authenticity
- e.g: checking one's identity using a passport
- Authorization
- Defines what you are allowed to do
- Associated security goal: Controlled Access
- e.g: Is the person on the passenger list?
Threats
Def: system might exploit a vulnerability.
The actual realization of a threat is called an attack
Impersonation
An entity claims to be another entity
Forgery of information
An entity creates new information in the name of another entity
Modification or loss of information
Data is being altered or destroyed
Repudiation
An eneity falsely denies its participation in a communication act
Eavesdropping
An entity reads information it is not intended to read
Authorization Violation
An entity uses a service or resources it is not intended to use
Denial of Service
Any action that aims to reduce the avaliability
- Authorization Violation + Eavesdroppinng
- Alice obtains root rights on a router and monitors all traffic for passwords
- Impersonation + Forgery of Information
- Alice pings Carl and pretends to be Bob
LangSec
通信协议
定义了交换信息的过程和格式
比如: IP, TCP, UDP, HTTP, HTTPS
NULL Character 问题
发送的是 www.payal.com\0www.tomaten.info
收到的是 www.paypal.com 因为 \0
表示字符串结束
解决
完整检查输入的格式
Werid Machine
一个werid 的机器是可以被攻击者编程的
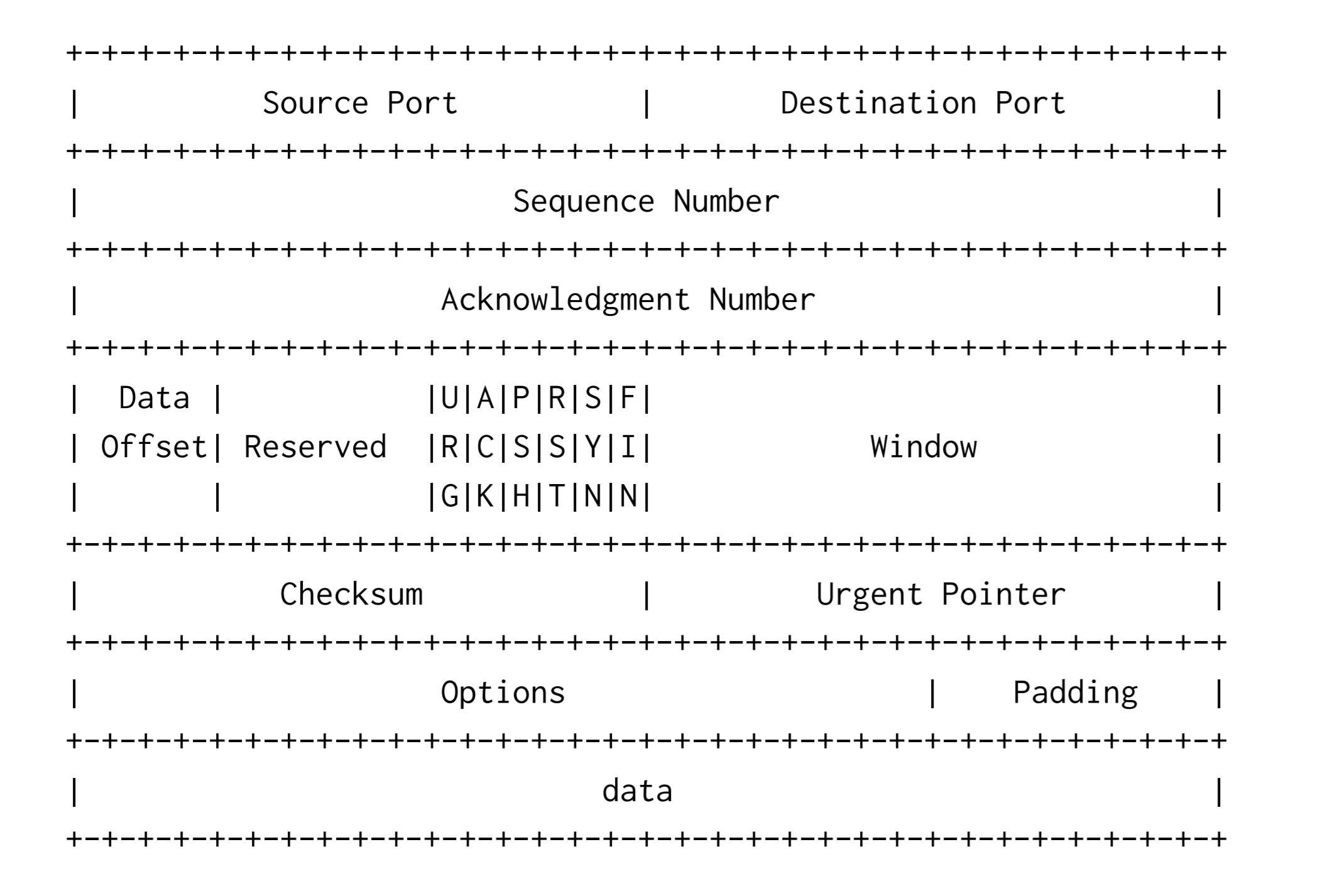
TCP
TCP的头格式
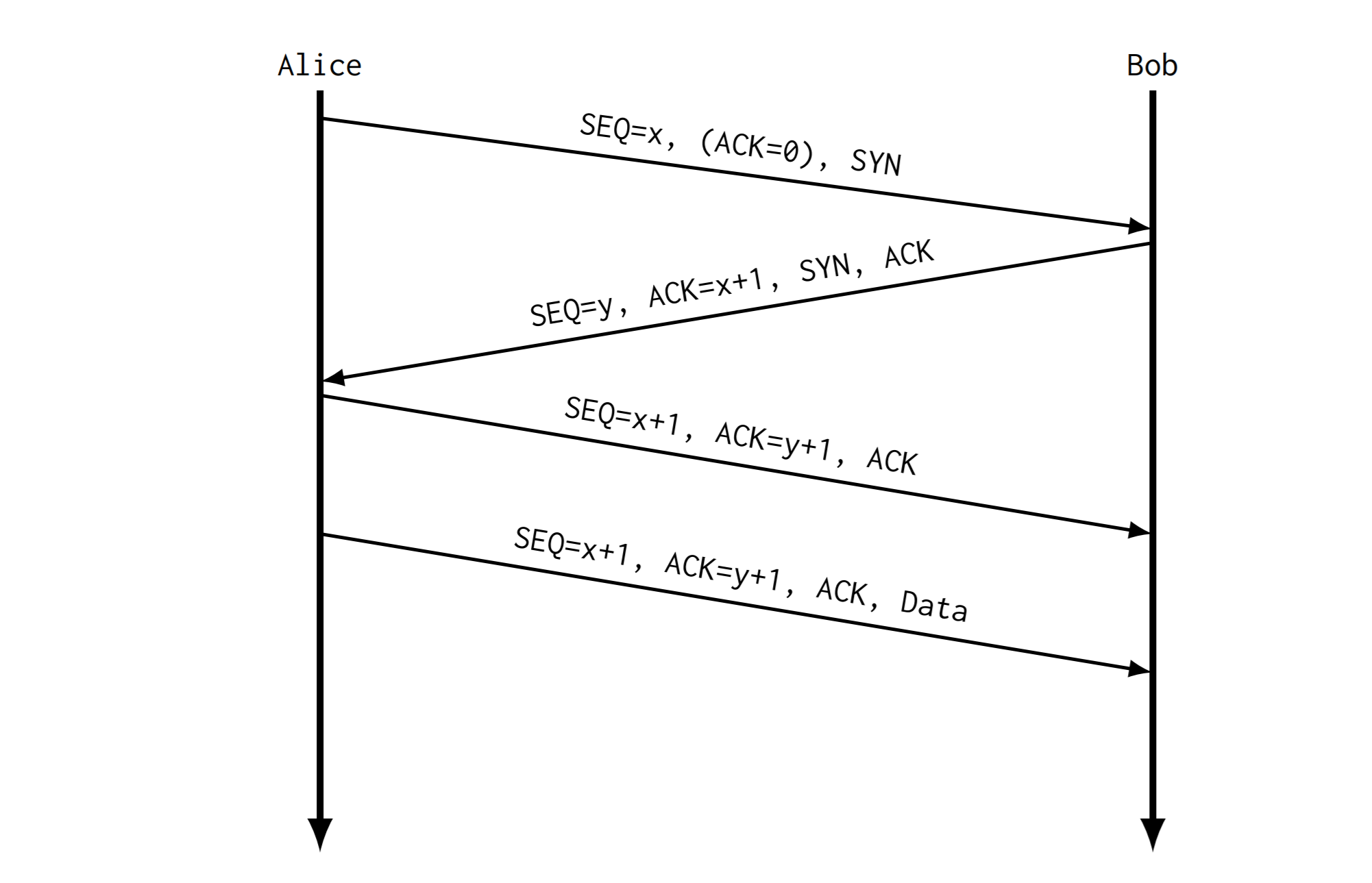
三次握手 3 way handshake
TCP 建立连接的过程通过三次握手实现:
- 客户端4发散一个 SYN 段指明要连接的服务器端口,以及初始序号ISN
- 服务器发挥包含服务器初始序号的 SYN 报文段作为应答,同时将确认序号设置为客户端的ISN+1 进行确认
- 客户端必须把确认序号设置为服务器发送的ISN+1来确认
TCP SYN Flood Attack
SYN Flood是当前最流行的DoS(拒绝服务攻击)与DDoS(分布式拒绝服务攻击)的方式之一,这是一种利用TCP协议缺陷,发送大量伪造的TCP连接请求,常用假冒的IP或IP号段发来海量的请求连接的第一个握手包(SYN包),被攻击服务器回应第二个握手包(SYN+ACK包),因为对方是假冒IP,对方永远收不到包且不会回应第三个握手包。导致被攻击服务器保持大量SYN_RECV状态的“半连接”,并且会重试默认5次回应第二个握手包,塞满TCP等待连接队列,资源耗尽(CPU满负荷或内存不足),让正常的业务请求连接不进来。
防御:TCP SYN Cookies
我们在发送序号的时候,计算一个 \(\alpha\) 发送过去
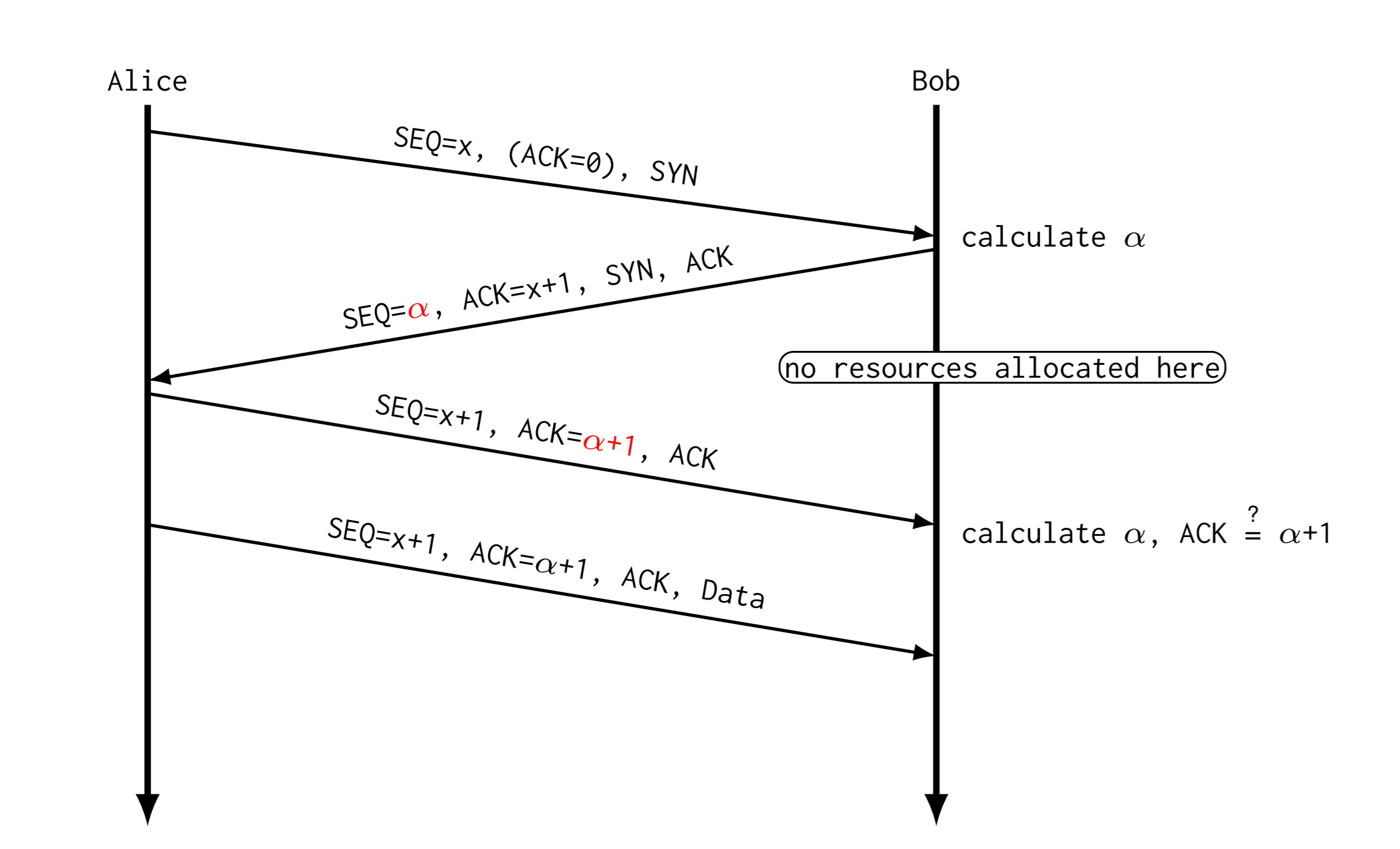
Syn Cache技术: 这种技术是在收到SYN数据报文时不急于去分配TCB,而是先回应一个SYN ACK报文,并在一个专用HASH表(Cache)中保存这种半开连接信息,直到收到正确的回应ACK报文再分配TCB。在FreeBSD系统中这种Cache每个半开连接只需使用160字节,远小于TCB所需的736个字节。在发送的SYN ACK中需要使用一个己方的Sequence Number,这个数字不能被对方猜到,否则对于某些稍微智能一点的Syn Flood攻击软件来说,它们在发送Syn报文后会发送一个ACK报文,如果己方的Sequence Number被对方猜测到,则会被其建立起真正的连接。因此一般采用一些加密算法生成难于预测的Sequence Number。 Syn Cookie技术: 对于SYN攻击,Syn Cache虽然不分配TCB,但是为了判断后续对方发来的ACK报文中的Sequence Number的正确性,还是需要使用一些空间去保存己方生成的Sequence Number等信息,也造成了一些资源的浪费。 Syn Cookie技术则完全不使用任何存储资源,这种方法比较巧妙,它使用一种特殊的算法生成Sequence Number,这种算法考虑到了对方的IP、端口、己方IP、端口的固定信息,以及对方无法知道而己方比较固定的一些信息,如MSS、时间等,在收到对方的ACK报文后,重新计算一遍,看其是否与对方回应报文中的(Sequence Number-1)相同,从而决定是否分配TCB资源。
Intrusion Detection System 入侵检测系统
- 为什么入侵检测很难?
False Negative: 本来不是入侵的行为却报了入侵, 即使概率很低。但数据量大了系统就会因此瘫痪
- 为什么我们需要入侵检测系统?
大多数系统有漏洞(Vulnerabilities), 一些攻击可以通过检测异常操作被探测.
- 我们需要检测什么?
入侵前奏(探测)(Intrusion preambles):入侵检测系统可以检测到入侵者尝试侦查系统或网络的行为,例如端口扫描或探测。 外部入侵访问 Intrusion accesses from the outside:系统可能受到外部黑客或恶意用户的入侵尝试,入侵检测系统可以帮助识别并应对这些尝试。 内部滥用行为 Abusive behaviors from the inside:有时候,系统内部的用户或员工可能会滥用其权限,例如越权访问敏感数据或滥用系统资源,入侵检测系统可以帮助监视和防止这种行为。
定义 入侵Intrusion:
侵犯已定义的安全要求 Compromise of a defined Security Requirement 入侵检测系统(Intrusion Detection System,IDS):是一种软件,具有检测和识别入侵的功能。有些会采取行动,有些不会。IDPS (Intrusion Detection and Prevention System) 会采取行动
蜜罐(Honeypot):它看起来像一个真实的计算机系统、网络或应用程序,但实际上是特意设置的,用来吸引攻击者。会对已执行的攻击进行深入检查。可以提供关于新攻击趋势的预警。 分散对手的注意力,使其转移目标的攻击。 可用作进一步攻击的来源:攻击者通过分析蜜罐的设置和针对它的攻击,可能会获得有价值的信息,如组织的网络架构、安全措施或漏洞。然后,他们可以利用这些信息来计划和执行针对组织真实基础设施的定向攻击。操纵蜜罐环境:技术娴熟的攻击者可能会操纵蜜罐环境,对其他目标发动攻击。用作重定向点:攻击者可能会利用被入侵的蜜罐来重定向和混淆他们的恶意活动。
分类
| Detection Method | Misuse detection |
|---|---|
| Anomaly Detection | |
| Data Source | Network-based |
| Host-based | |
| Detection Delay | Real-time |
| A posteriori | |
| Reaction | Passive |
| Active | |
| Analysis | Individual |
| Cooperative |
Misuse Detection 滥用检测
在数据库中存攻击代码的签名signature,检测流量的签名,频繁更新数据库。找到其中在数据库的哈希值,就说明这个数据traffic 是有害的
Advantage: * efficient detection * less false positives
Disadvantages: * only detect known attacks * more false negatives
Anomaly Detection 异常检测
Model a state of system. 一个系统的某些值会有一个状态,如果超过一个阈值,就可以发出警报.
Difficulty: * Heuristics threshold definition is complex: * Diurnal patterns(日常模式), 晚上,周末,假期,随机事件的用户会减少。 * Long-term patterns, 随着时间推移,用户增加。长期趋势会影响,
Advantage: * Can detect new attacks
Network-based
检测网络中的数据包
可以检测 * Unauthorized network access * Reconnaissance 侦察 * Abuse of bandwidth resources (DoS) * Network protocol violations
但是
- Can not analyse encrypted data
Host-based
Analyses data from individual system
可以检测: * Privilege Abuse 权限滥用 * Accidentally assigned privileges 不小心的授权 * Account compromise * Access and modification of critical data * Information leakage
Advantage: * Able to function in environments with encrypted data: Plaintext会在host被处理,可以读取内存
Real-time detection
实时检测:
拦截数据和控制流 在目标系统运行时进行信息处理 检测时间较短 影响系统性能
A posteriori
事后处理:
信息被记录 处理和分析稍后进行 检测时间较长 可以容易地并行化
Symmetric Encryption
Mode of Encryption
Name four Mode of Encryption
- Electronic Code Block Mode (ECB)
- Cipher Block Chaining Mode (CBC)
- Output Feedback Mode (OFB)
- Counter Mode (CTR)
Why is len(c) > len(m)?
m is padded with extra data to have a full block of 16 ByteWhy can't we achive Integrity and Authenticity
Integrity: The attacker could modify c. Reciver can only assume that the message was modified but not prove it.
Authenticity: The attacker could just send random c and spoof Alice's IP addressOne-Time-Pad(OTP)
Type of cipher?
stream cipherThree Requirements
- Key otp must have same size as message.
- Key otp must only be used once.
- Key otp must be a perfectly random bit stream
Security of Ciphers
Kerckhoffs’s principle
The cipher method must not be required to be secret.Consequence and Benefits of Kerckhoff's Principle
Consequence: * The cipher can be publicc * The security depends on the secret key
Benefits: * Otherwise if the cipher leaks, we have to build a new one. * For each communication partner, selecting a new key is sufficient * We can perform review procedures that increase confidence in the cipherName 2 block cipher and 2 stream cipher
Block: * AES * 3DES
Stream: * ChaCha20 * One-Time-PadAttaccking Symmetric Ciphers
Attack Scenarios
- Ciphertext-only-attack
- Known-plaintext attack
- Chosen-plaintext or chosen-cyphertext attack
What is a secure cipher
If the best known attack is brute-forcing all keys.Why OTP secure
- only outputs reveals the right m
- OTP won't be reused
- ciphertext is perfectly random
Drawback for OTP
- necesary key length in bits: length(otp) = length(m)
- otp must not be reused key generation is difficult
Modes of Encryption
一个信息 \(m\) 分层若干块 \(m_1,m_2,...\) 每一块分别加密
ECB
最朴素的, \(Enc(m_i,k)=c_i\)
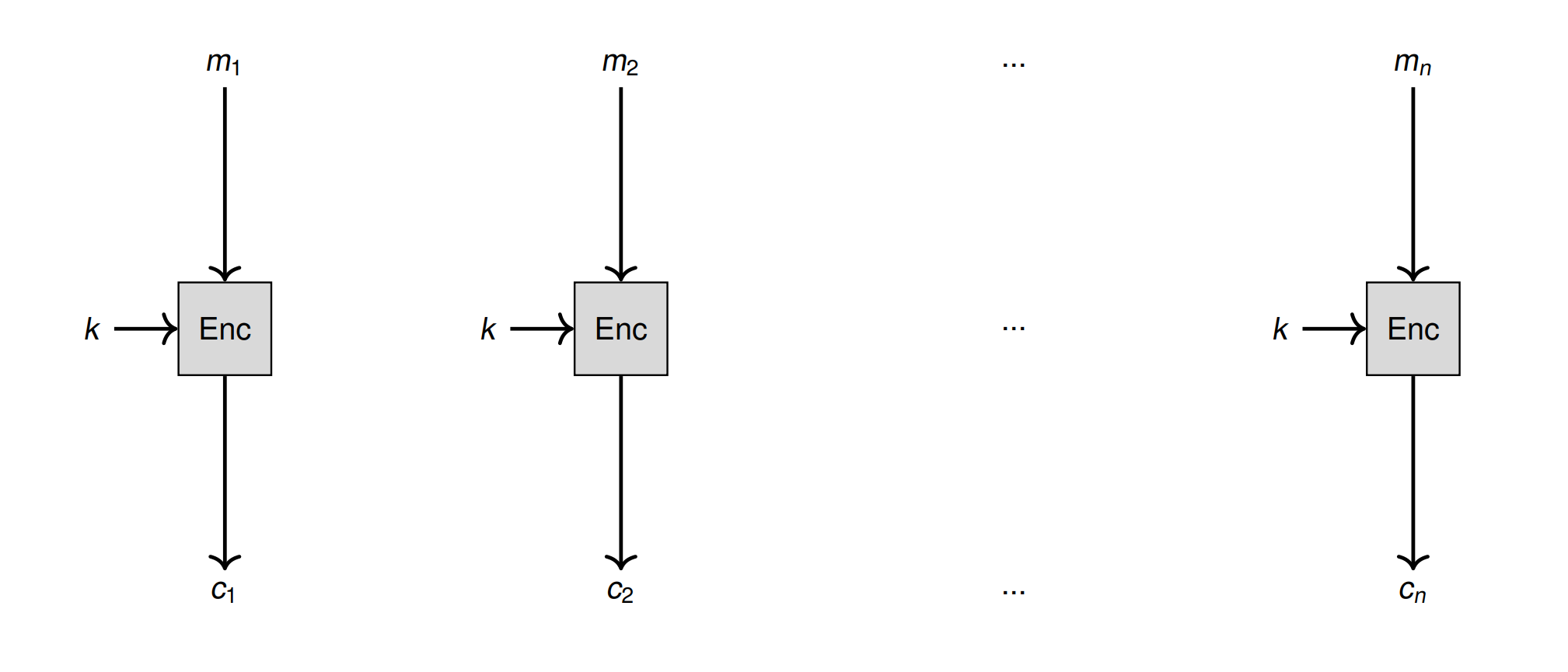
Drawback:
- Ciphertext do not have any connection with each other -> No integrity
CBC
\(Enc_k(m_i \oplus c_{i-1})\) 一开始有个 \(IV\) (fresh 不是固定的)
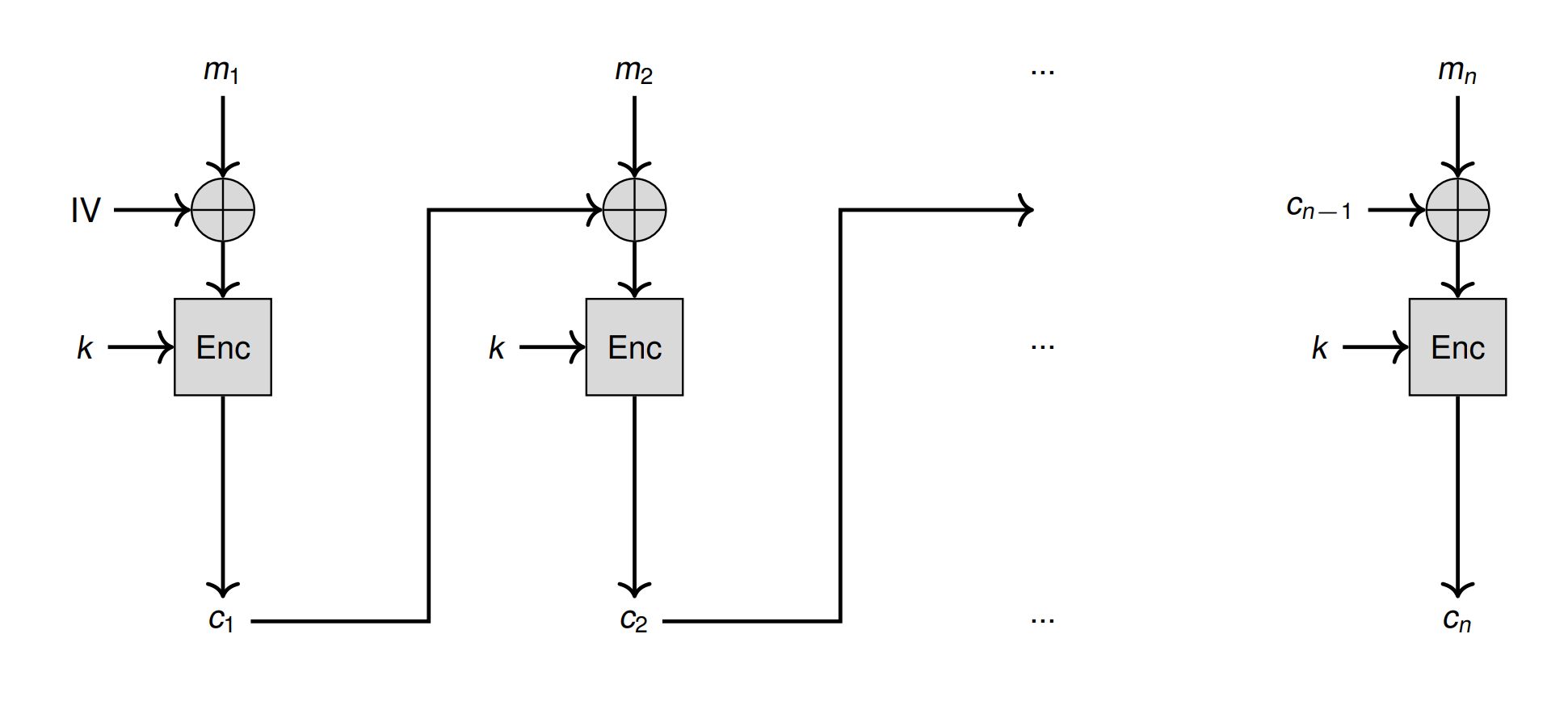
Identical plaintext -> non-identical ciphertext
No integrity protection
OFB
把 block cipher 变成 stream cipher
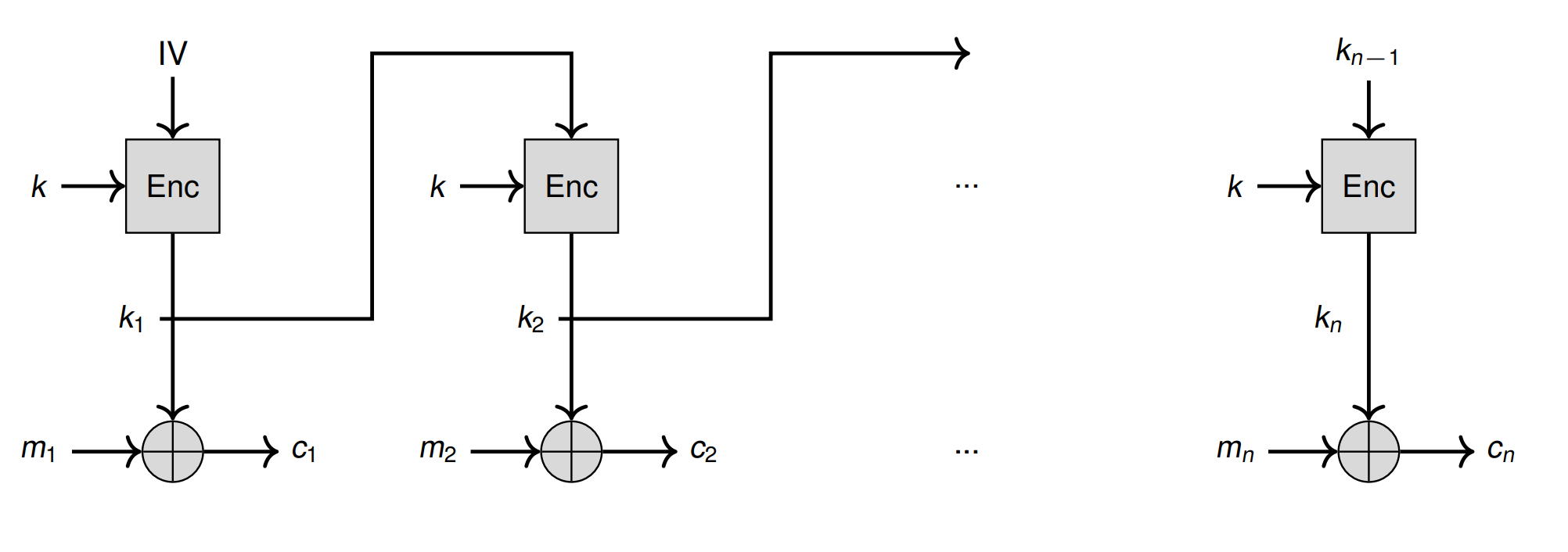
- Decryption do not depend on previous blocks (Transmissino error only affects this block)
CTR
把 block cipher 变成 stream cipher
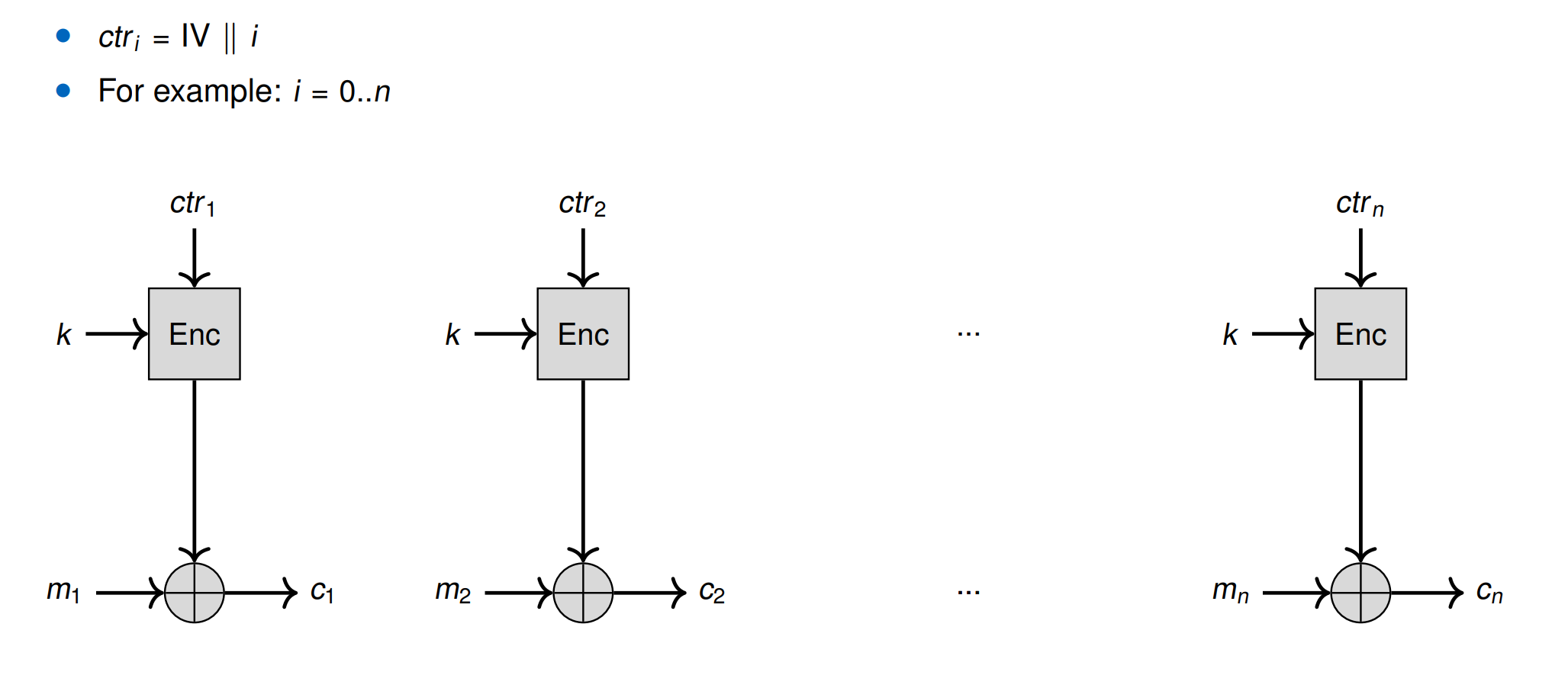
- Decryption does not depend on previous blocks.
HASH MAC
Hash function
\(h\) maps an input \(x\) to fixed length \(n\) of \(h(x)\)
- one-way: hash function, computationally infeasible to find \(x\) with \(h(x)=y\)
cryptographic hash function
one-way function (1st pre-image resistance)
Given \(x\) , computaionally infeasible to find \(x'\) with \(h(x)=h(x')\) (2nd pre-image resistance)
Important for digital signature
Collision resistance
computationally infeasible to find pair \((x,x')\) with \(h(x)=h(x')\)
Random Oracle property
computaitionally infeasible to distinguish \(h(x)\) from random n-bit value
CRC
Cyclic redundancy Check (CRC) , Why not use as cryptographic hash function?
- no 2nd pre-image resistance, no collision resistance
Integrity
No: a hash function is not sufficient to secure a message against intentional manipualtion
MAC
Include a secret key \(K\) shared with Alice and Bob.
Computes \(MAC_K(m)\) Send \(<m,MAC_K(m)>\) to Bob. Bob verify it using his key.
- prove integrity, detect tampering, can be replayed
Do Mac prove authenticity? Depends on senario
\(sMAC_k(m)=Enc_k(h(m))\) is not secure using stream cipher, using AES is secure
\(sMAC_k(m)=Enc_k(\Delta(m))\) , \(\triangle(m):=x_1 \oplus x_2 \oplus \ldots \oplus x_n\) is insecure
Construction
Based on Hash function: HMAC
HMAC: \(H(K \oplus opad | H(K \oplus i p a d | m))\)
faster than block cipher
Based on Block cipher: CBC-MAC, CMAC
CBC-MAC: not use same key for encryption
Randomness
Entropy
Measure of unpredictability
Public Key Cryptography
Secure Channels
Security channel provide
- Confidentiality, Integrity, Authenticity
- Messages received in correct order
- No duplicates/replayed messages
Usecase: VPN,TLS,Secure messenger applications(Signal)
s require a long term (symmetric or asymmetric) key to work,Exchanging/agreeing on long term keys is often done out of band交换/协商长期密钥通常是在带外进行的,即在通信通道之外的安全通道上进行
Ways
| Construction Nr. | Name | Definition |
|---|---|---|
| \(\# 1\) | MAC-then-Enc | \(\operatorname{Enc}_{k \text {-enc }}\left(m, \operatorname{MAC}_{k \text {-int }}(m)\right)\) |
| \(\# 2\) | MAC & Enc | \(\operatorname{Enc}_{k \text {-enc }}(m), \operatorname{MAC}_{k \text {-int }}(m)\) |
| \(\# 3\) | Enc-then-MAC | \(\operatorname{Enc}_{k \text {-enc }}(m), \operatorname{MAC}_{k \text {-int }}\left(\operatorname{Enc}_{k \text {-enc }}(m)\right)\) |
MAC-then-Enc:
Encryption does not provide any message authenticity/integrity!
Mac & Enc
Can be attacked when MAC is weak
Enc-then-MAC
Considered secure
Secure Channel Implementation
Message numbering
编号 $ n N$,记录上一个的编号,只有递增才接受。溢出的时候重新生成密钥
Authenticated Encryption With Associated Data (AEAD)
传递Encryption 和 MAC 包含 Associated Data
Associated data (AD): Additional non-encrypted but authenticated (header) data,
- IV, Seq number, routing informtion
Benifit:
- standarized, only need one pass
Example: GCM, OCB
Galois Fields and Galois Field Multiplication
Galois Field: 把二进制转换成多项式
Galois Field Multiplication is based on polynomial multiplication modulus a specific irreducible polynomial g(x)
乘法:乘一个多项式,Mod一个不能被分解的g(x) (类似素数)
Galois/Counter Mode (GCM)
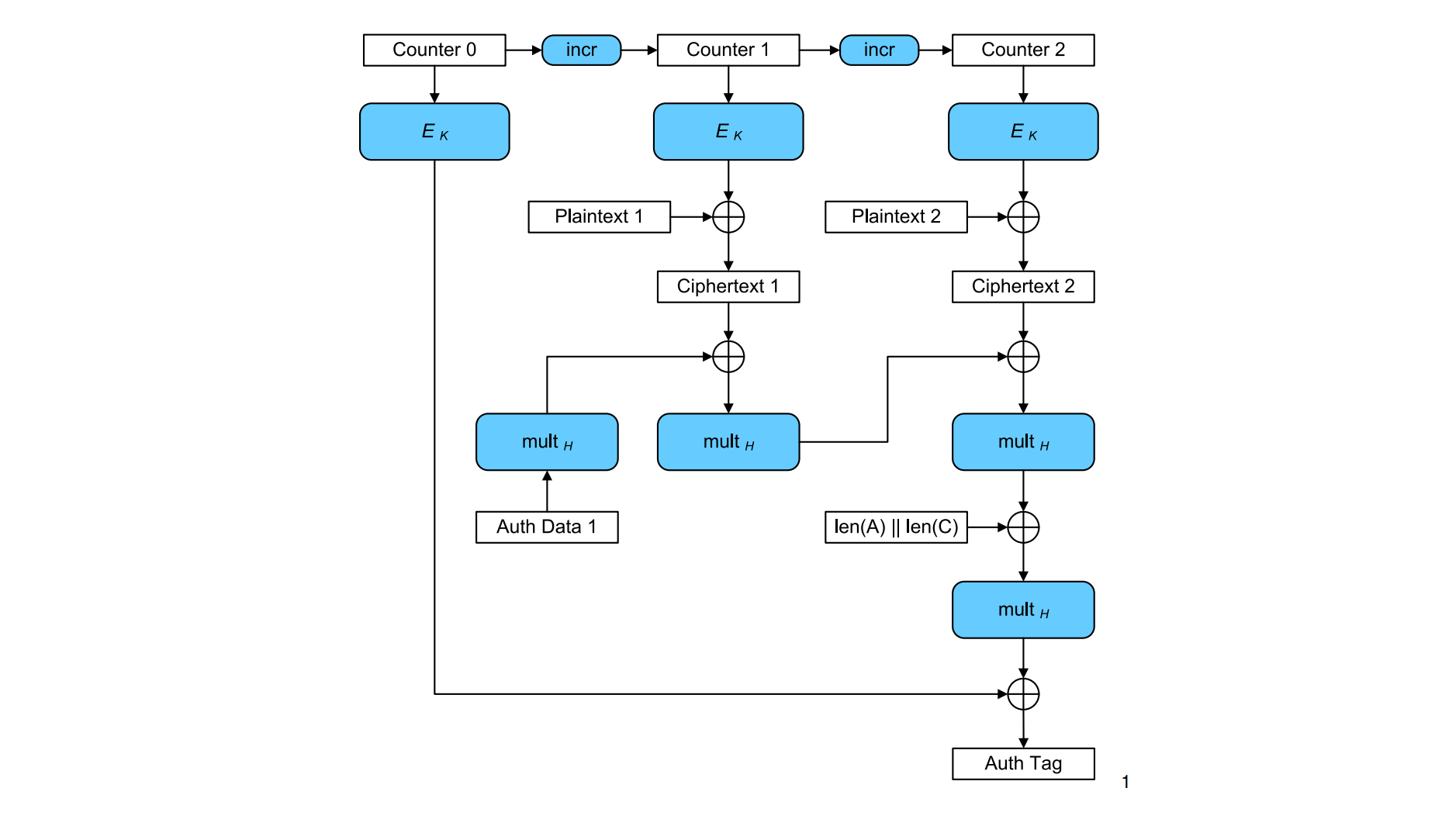
Offset Codebook Mode (OCB)
Offset0 is computed by a specific function depending on the key and a nonce
It is crucial that, as one encrypts, one does not repeat a nonce
ATTACK against Stream Cipher
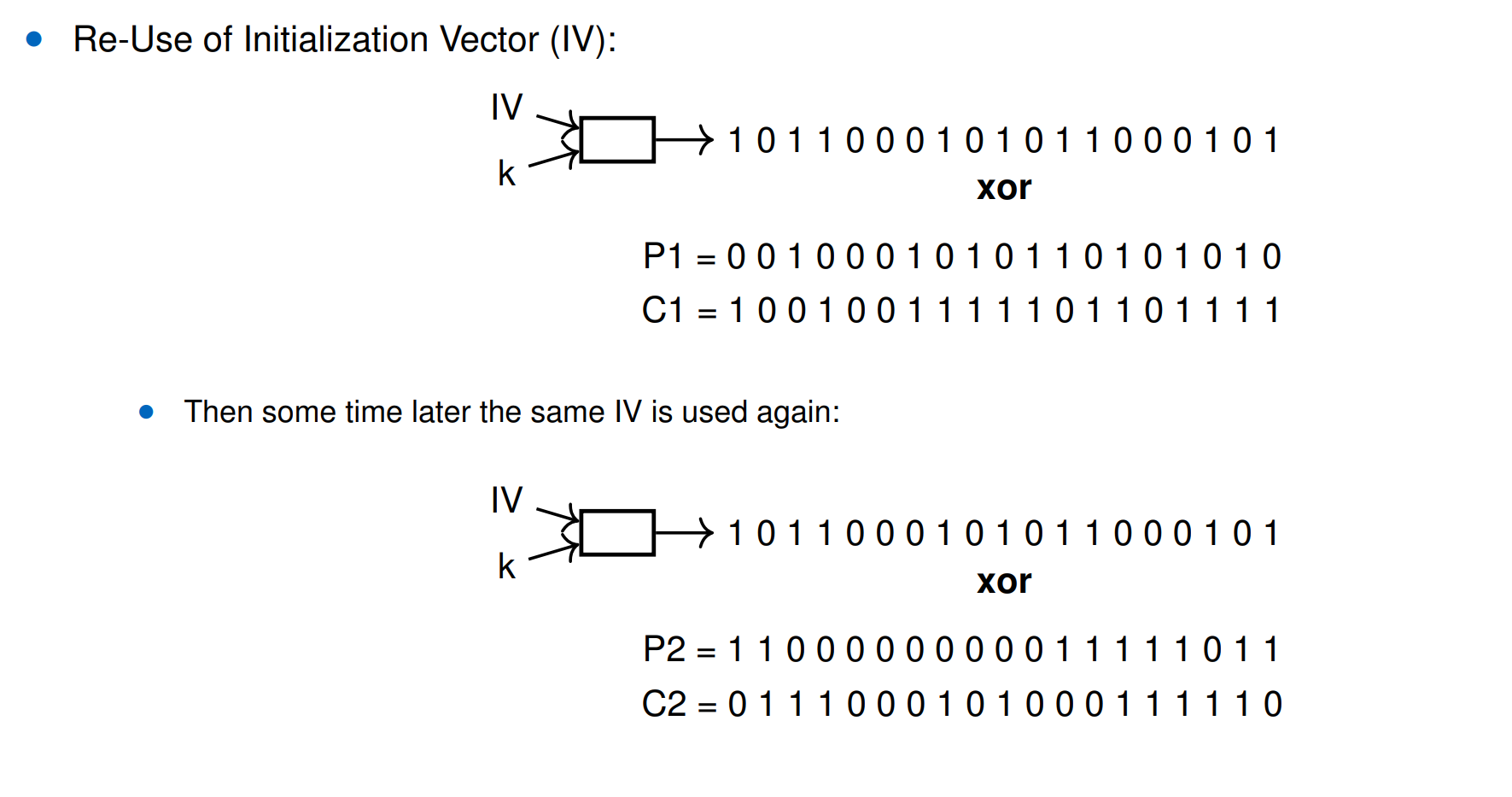
C1 + C2 = P1+P2
- Known Plaintext (e.g. P1) → attacker can compute other plainte
- Statistical properties of plaintext can be used if plaintext is not random-looking. That means if entropy of P1+P2 is low.
Padding Oracle Attack against CBC
一位位猜密文,用Padding Eror来看。如果没有Padding Error,可以用Side Channel来推断
PKI
非对称加密的优势在于公钥不需要保密。
这使得用户可以通过任意渠道分发公钥,例如:
- Alice 从 Bob 发送的邮件中获取 Bob 的公钥。
- Bob 从 Alice 的网站上下载 Alice 的公钥。
但问题在于,任何使用其他实体的公钥的人都必须确保这个公钥确实属于该实体,即该公钥是真实的,可信的。
想象一下:中间人 Eve 已经用她控制的密钥替换了公钥。
既不是 Alice 也不是 Bob 可以发现他们收到的密钥不是真实的。
由于 Eve 拥有私钥,她可以:
- 以 Alice 和 Bob 的名义计算签名。
- 解密 / 重新加密 Alice 和 Bob 之间交换的机密消息。
Manual trust establishment = high effort
Definition of a certificate
A certificate is a digitally signed binding of an identifier of an entity and the public key of an asymmetric key pair owned by that entity
Always necessary: Verification that identifier and corresponding key belong together.
creation
issuer \(I\) has a public key, KI-pub , and private key, KI-priv, X is an identifier to be bound to a public key, KX-pub .
\(\left(X, K_{X-\text { pub }}, \operatorname{Sig}_{K_{I-p r i v}}\left(X \mid K_{X-\text { pub }}\right)\right)\)
Common Forms
in hierarchical PKIs: “Certification Authority” (CA)
In non-hierarchical PKIs sometimes: “Endorser”
hierarchical PKI
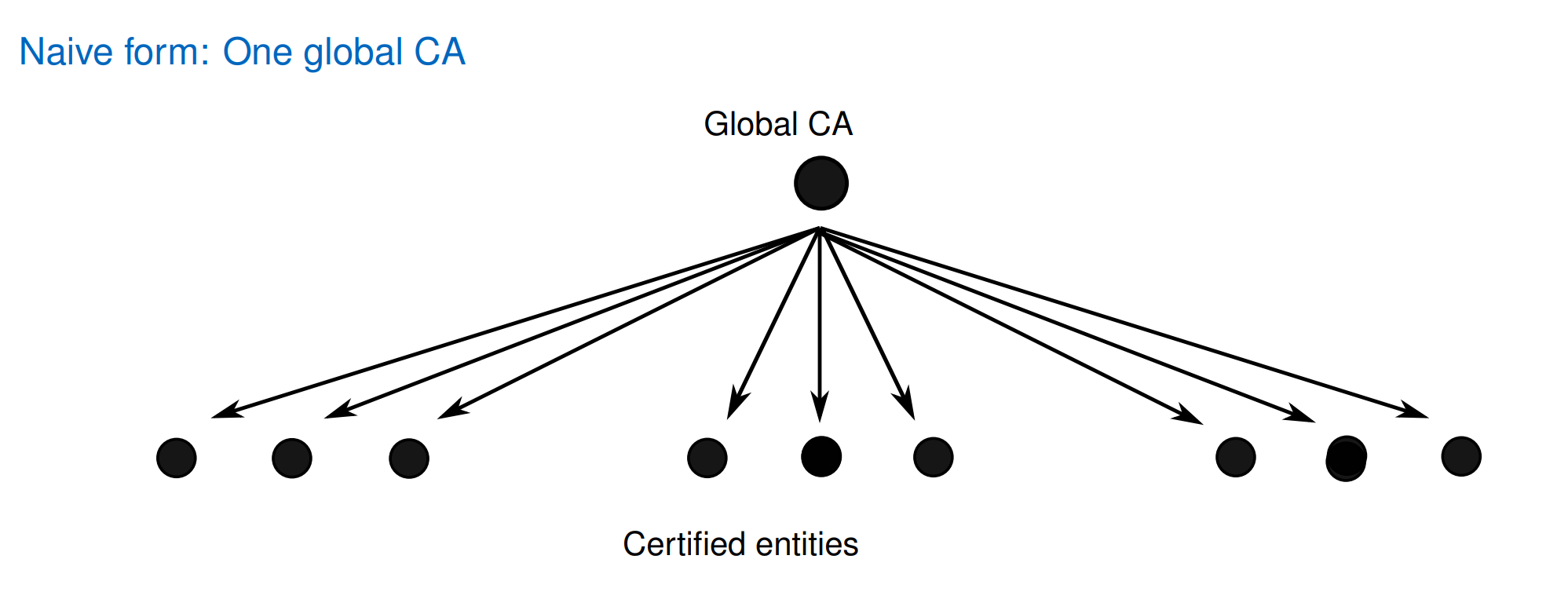
infeasible
eg. Web PKI
non-hireachical PKI
Web of trust
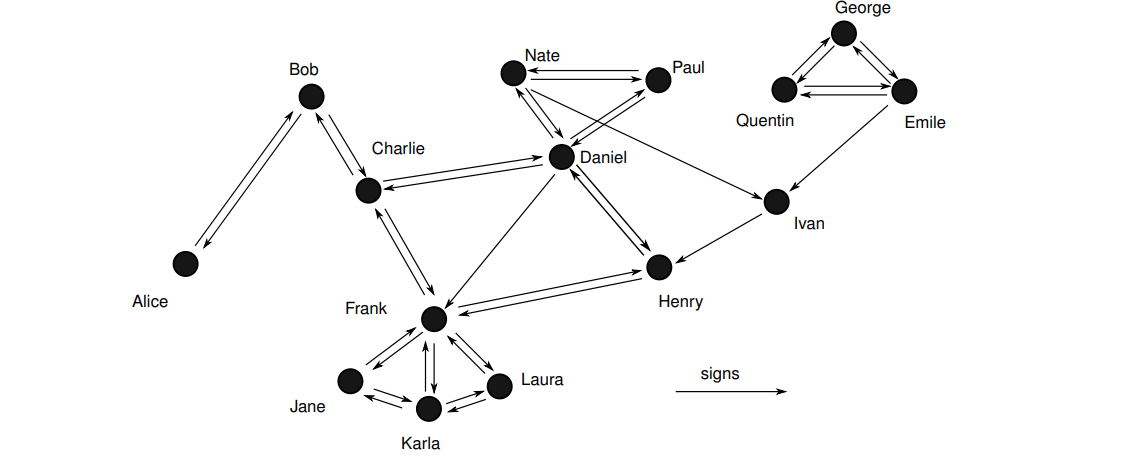
eg. OpenPGP
X.509
SSL/TLS include certificate-based authentication
Goal: protect sensitive information like cookies, user input
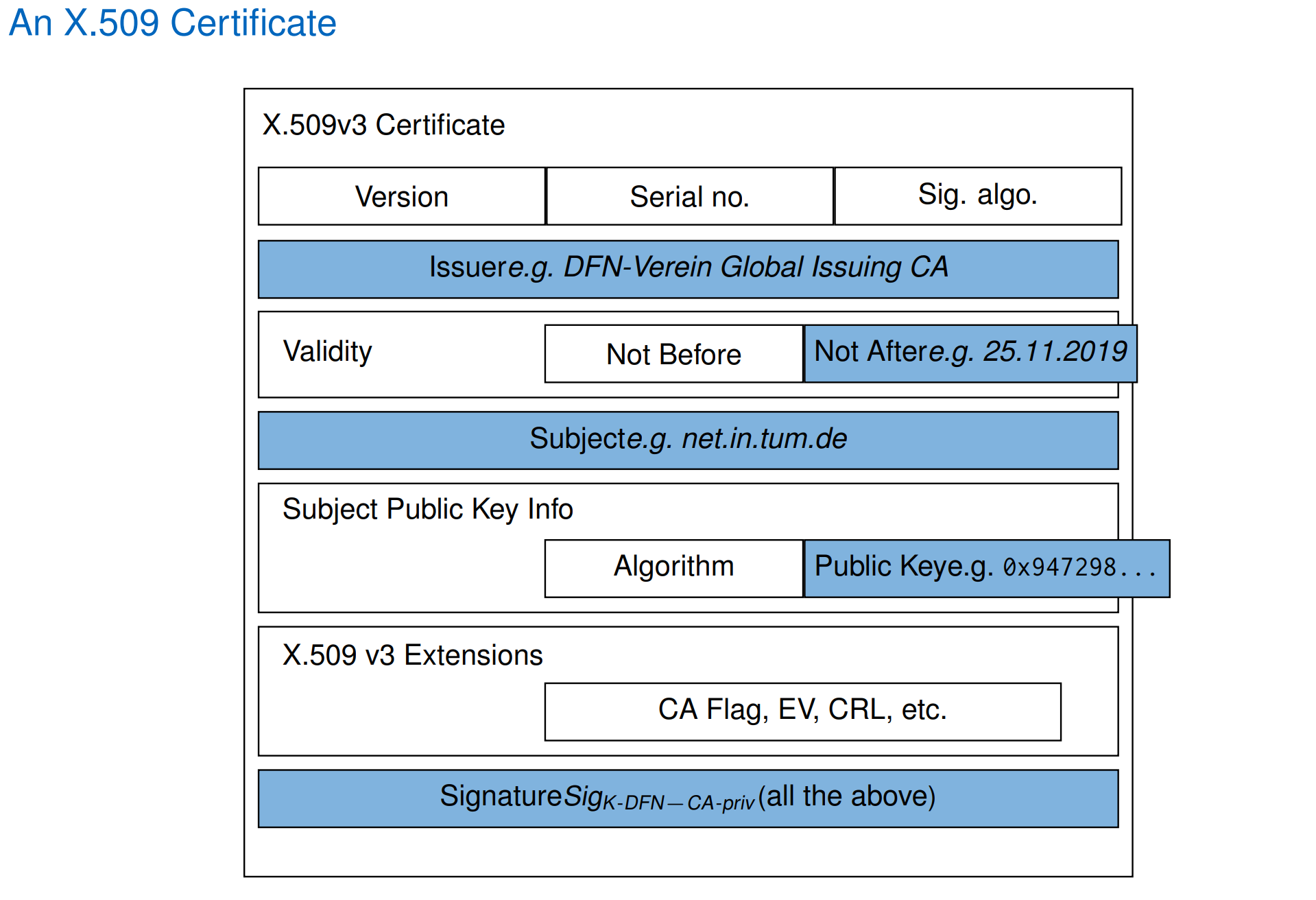
certificate includes only one domain name, called common name (CN),
it is possible to create certificates that are valid for multiple (sub-)domains:
listeed in subject alternative name (SAN), wildcard possible
CA:
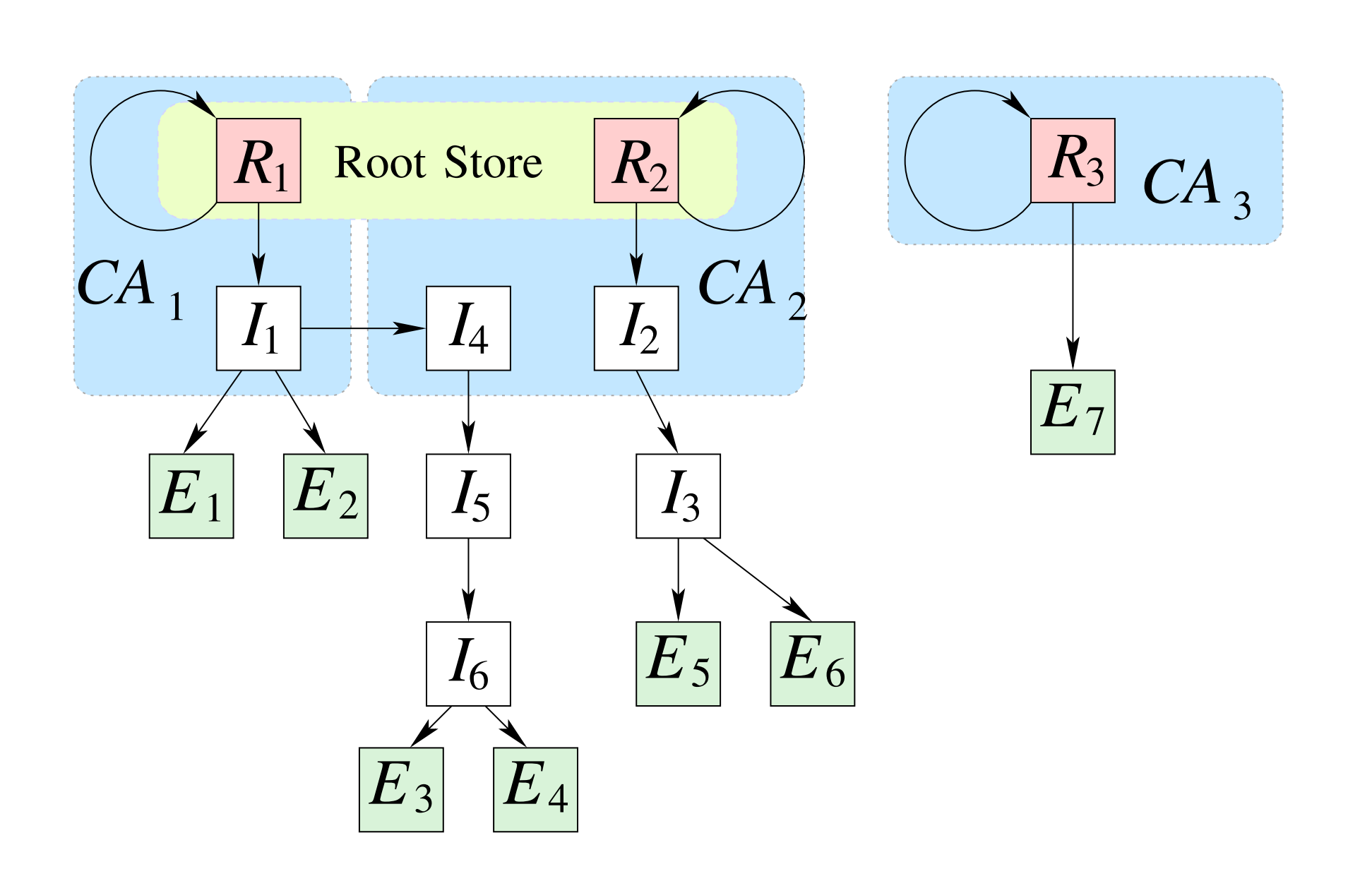
- root stores:certificates of trusted CAs, self signed
- Every application that uses X.509 has to have a root store(OS, Browser)
Intermediate certificates
part of a certificate chain, but neither a root certificate nor an end-entity certificate
reason, they are CAs, have the same signing authority as root certs
- Protect your main root certificate, private key offline
- To delegate signing authority to another organization: sub-CA
Hazard:
- SSL proxies allow the transparent rewriting of certificate chains
Corss-signing
A CA signs a root or signing certificate of another CA
- For the WWW, it completely breaks the root store model
Fact:
Your browser or your OS chooses the ‘trusted CAs’. Not you.
All CAs have equal signing authority
Any CA may issue a certificate for any domain.
The weakest CA determines the strength of the whole PKI
Certificate Issuance
How is a certificate issued in practice?
Domain Validation(DV): proves ownership of the domain
Extended Validation (EV): Additionally requires (strong) legal documentation of the claimed identity
eg. url belongs to amazon
Organizational Validation (rare), Between DV and EV; less documentation
ACME: Automated Certificate Management Environment
Step 0: ACME Client creates an “account key” (asymmetric cryptography key pair)
Step 1:
HTTP-01 Challenge Request
request challenge
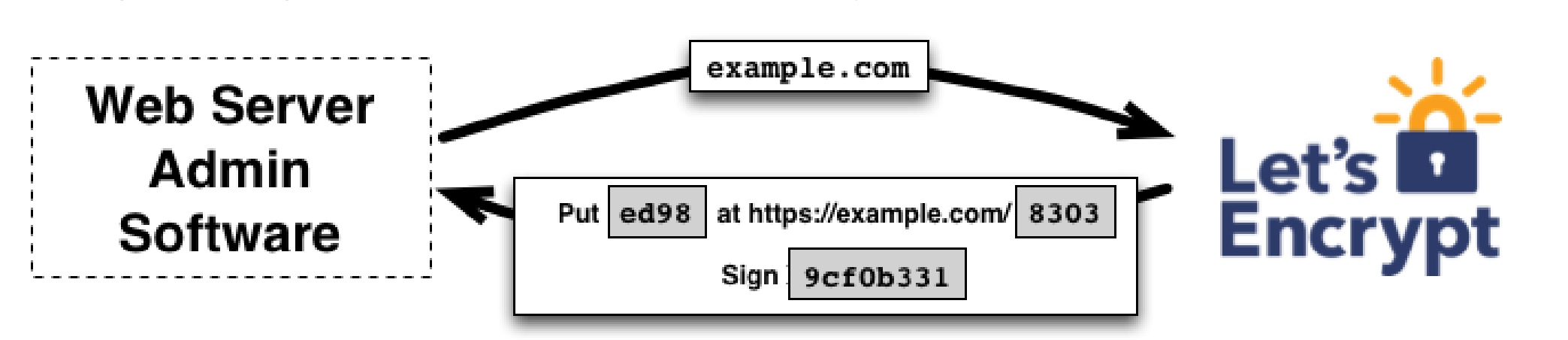
Client signs and publishes challenge. The CA can now check the published file content:
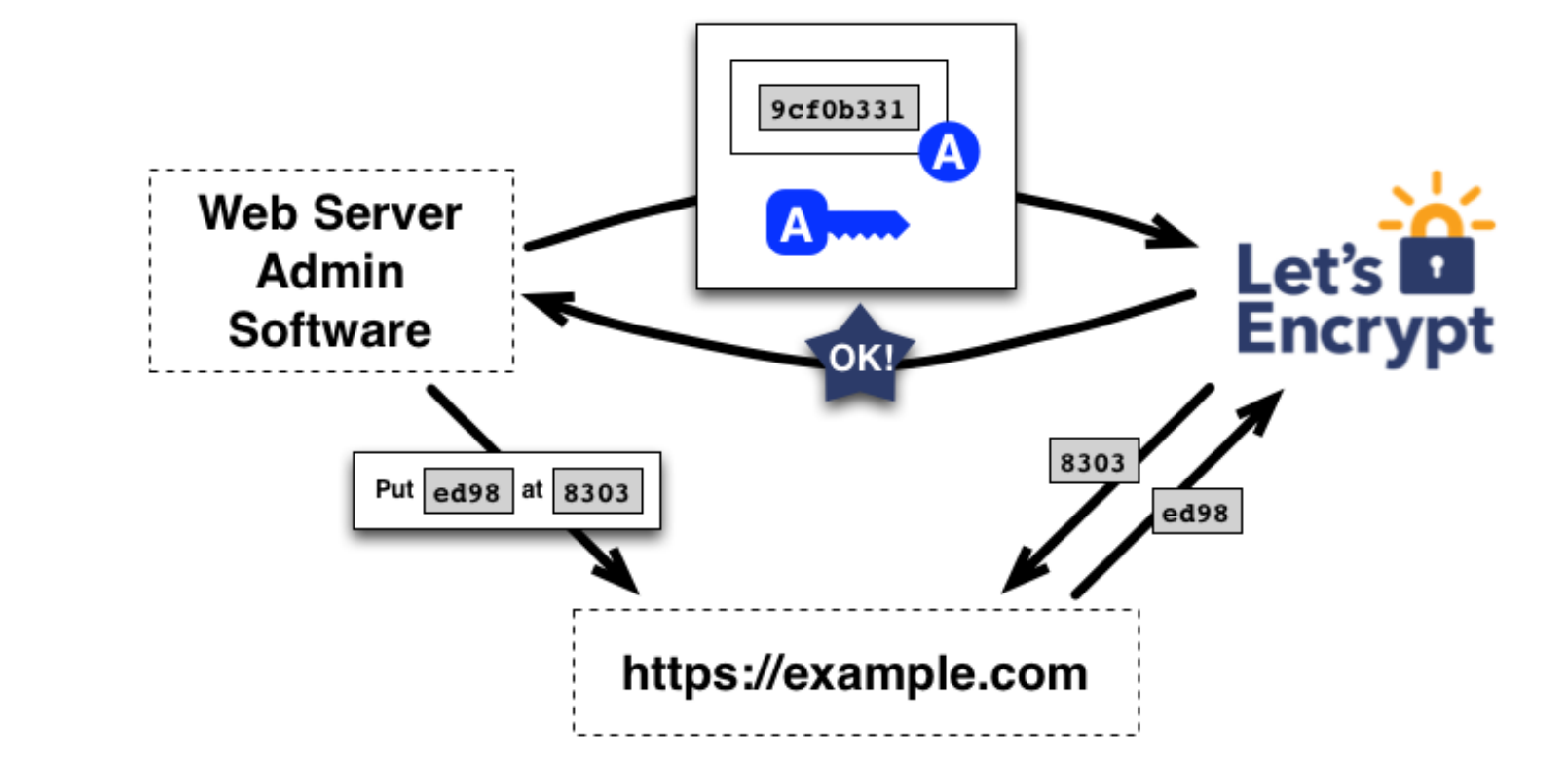
DNS-01 Challenge Verification
Client constructs key authorization from token offered by server challenge and the client’s account key
Generate SHA-256 digest in base64 • Store as DNS TXT record under _acme-challenge for domain to verify
Challenge ok ⇒ Account key pair is then “authorized”
Certificate Revocation
Certificate Revocation Lists (CRLs)
Intermediate certs should be checked, too
CRLs can grow large
Downloads of CRLs can be blocked by a Man-in-the-middle
Online Certificate Status Protocol (OCSP)
Lookups go over the network – induces latency
OCSP servers must have high availability
Privacy! OCSP servers know which sites users access
OCSP Stapling
The idea is thus that servers request fresh OCSP ‘proof’ from CA: ‘this certificate is still considered valid’
Reduces load on CA, reduces overall web page loading time, solves privacy problem
Certificate Pinning
Aim: defend against malicious certs
Idea: browser "pins" the certificate a Web server presented on first contact
shortcomming
- TOFU problem
- Life-cycle problem,Servers may (legitimately) update/upgrade their keys
- Scalability problem:Browsers cannot come pre-loaded with pins of all sites, and keep them up to date
Cryptography Protocol
Tool to draw protocol: https://plantuml.com/zh/
Alice = initiator 发送第一个消息的
Bob = Responder 不是第一个发消息的
AS = Authentication Server
Cryptographic protocols typically include
- entity authentication
- key establishment
Notation
Alice \(\rightarrow\) Bob: \(\{n\}_{K_{A, B}}\)
Alice 发送给 Bob, \(K_{A,B}\) 是 shared key, \(\{\}\) 表示encrypted and integrity-protected
entity authentication
- Authenticity of one entity is shown
- Authenticity of both entities is shown: mutual authentication
key establishment
- A key is established between some protocol participants
- Type1 : Key Transport: Some entity creates the key and sends it to other entities.
- Type2 : Key Agreement: Multiple entities contribute to the generation of the key
Boyd
if no pre-exchanged keys exist, cryptographic protocols cannot operate securely.
Goal
Forward Secrecy
key相互独立
- If long-term key is compromised, attacker cannot find out session keys for older sessions.
- If session key is compromised, other session and long-term keys are not affected.
Goals:
- Alice and Bob have a shared session key for a secure channel
- Alice and Bob have agreed on the cryptographic algorithms to be used for the secure channel
- Mutual authentication and freshness: Alice (Bob) must be able to verify that Bob (Alice) participated in the protocol run and that he (she) is “alive”
- Alice and Bob must know that KA,B is newly generated
Attack
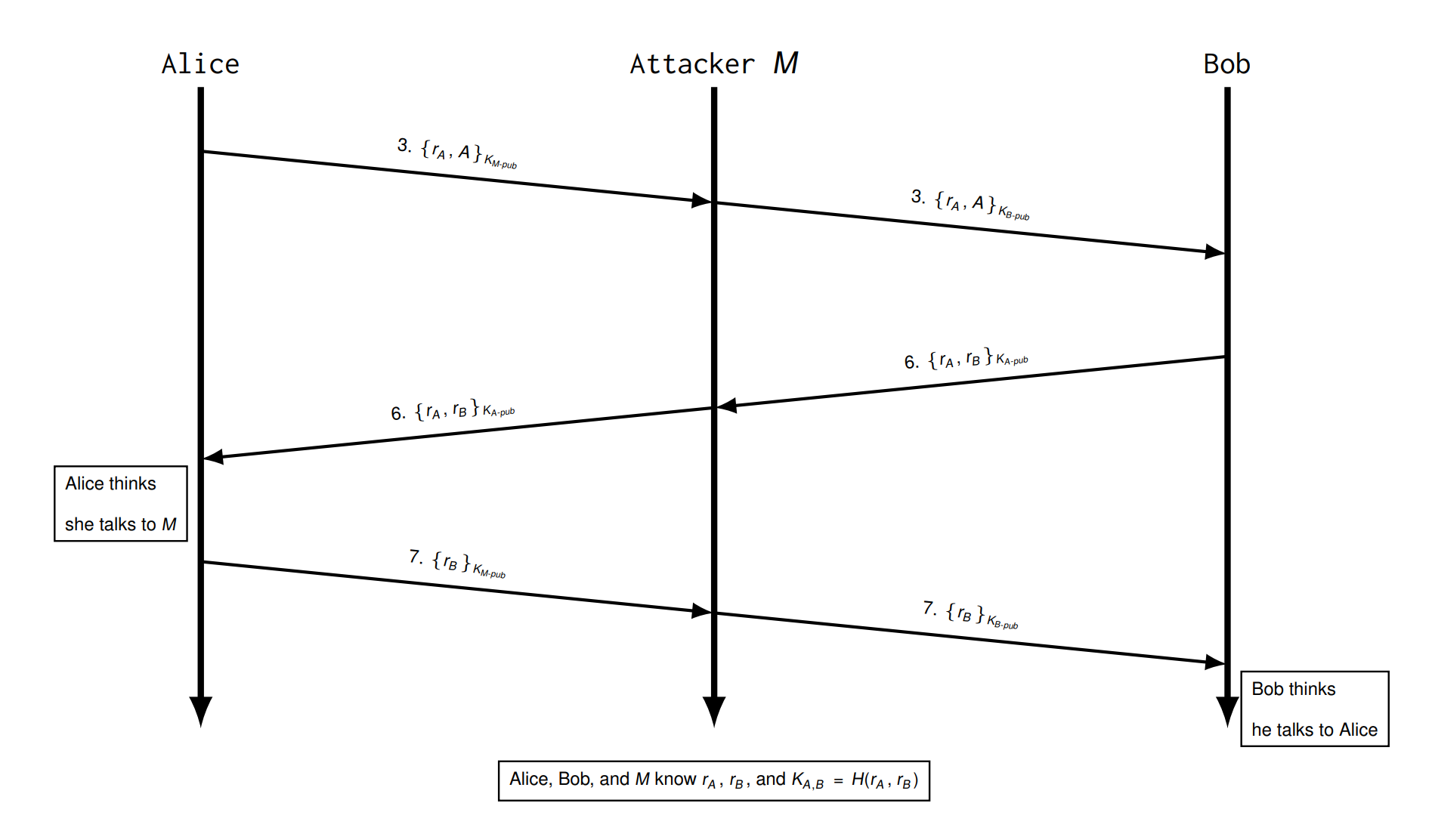
Relay attack 转发攻击
A 用 Service,Service 用Challenge Response方法验证
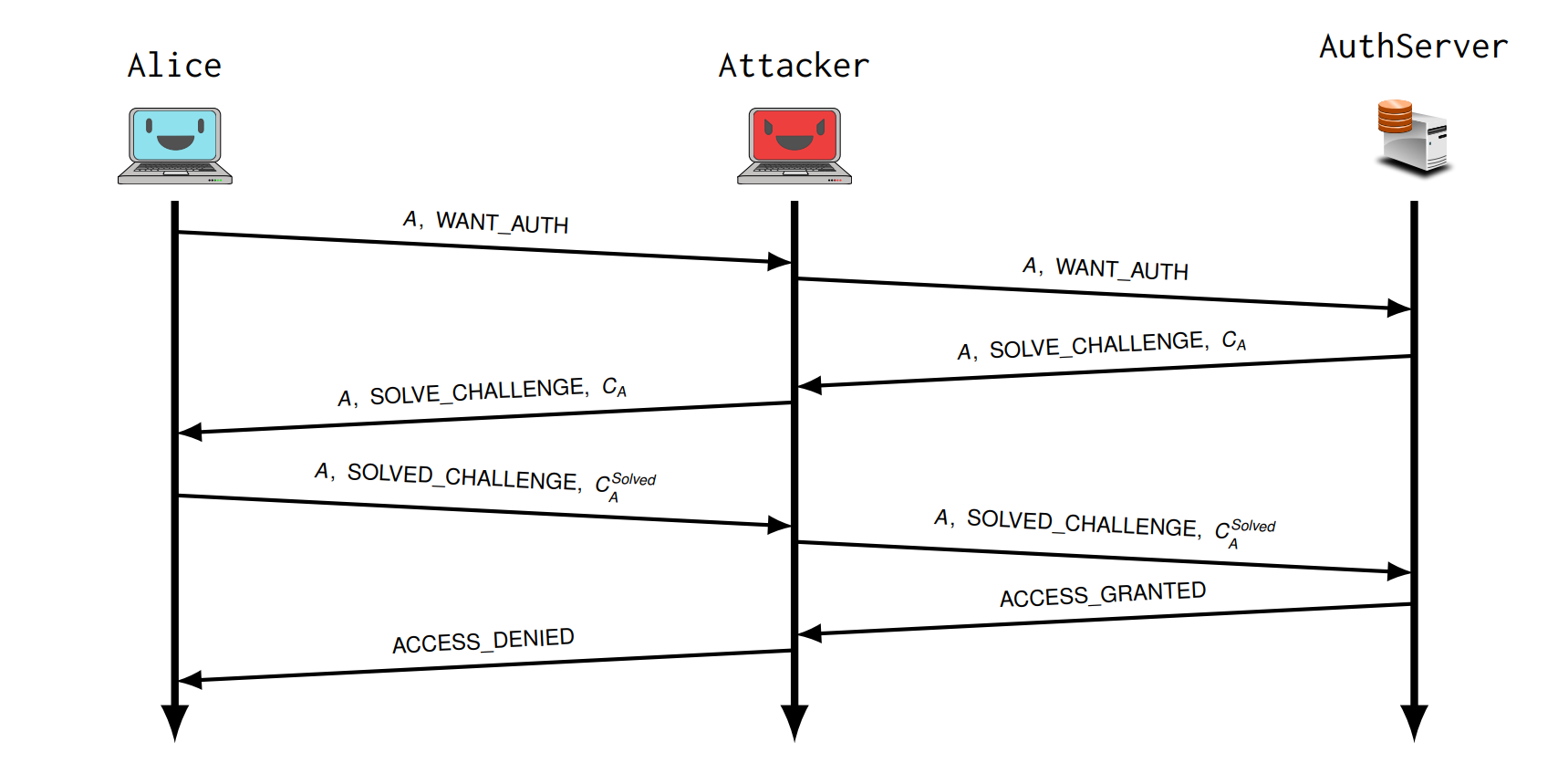
Attacker 可以 impersonate the service
Replay attack
Attacker eavesdrops or receives messages, Can later-on send message or part of message to same or other principals
Oracle Attack
Oracle=entities can do sth. a normal entity can not
Protocol Interaction attack
Replace message field in protocol A with message field in protocol B. • Example: Trick user to sign a message in protocol 1; reuse signature in protocol 2
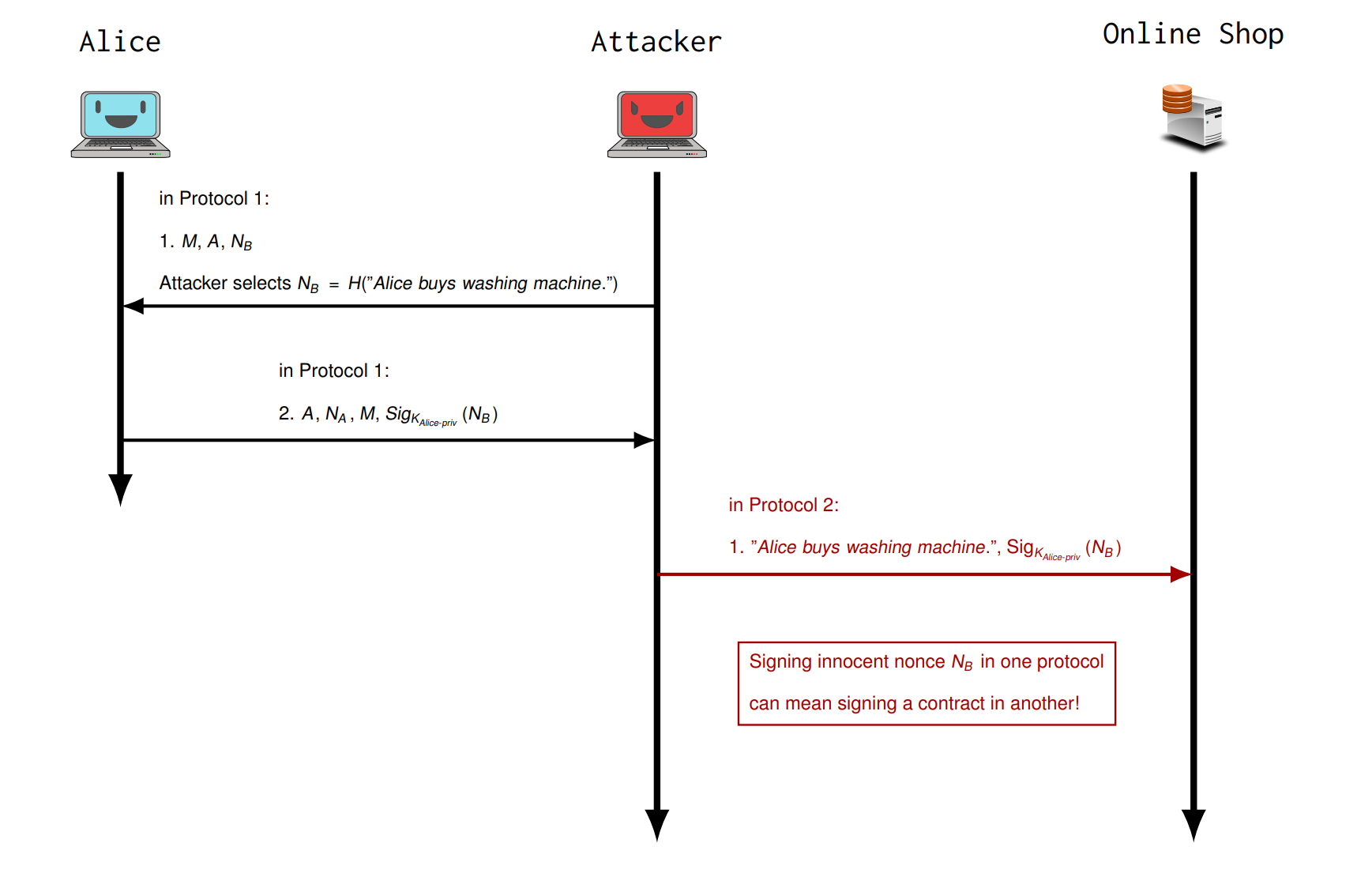
Protocol
Try 1,2 DH (with password)
本来可以用DH来交换建立共同的key,但是会被MitM Attack
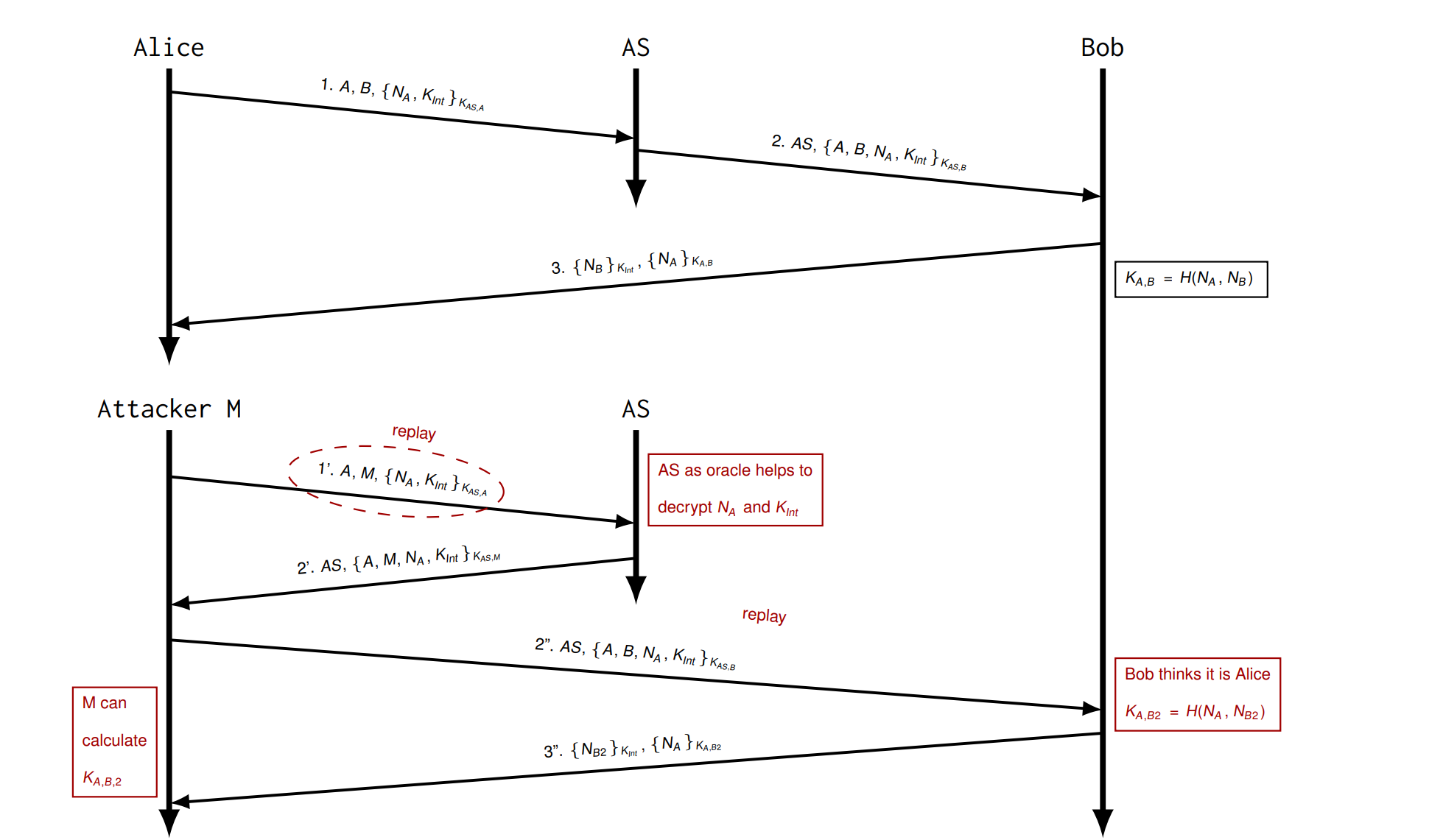
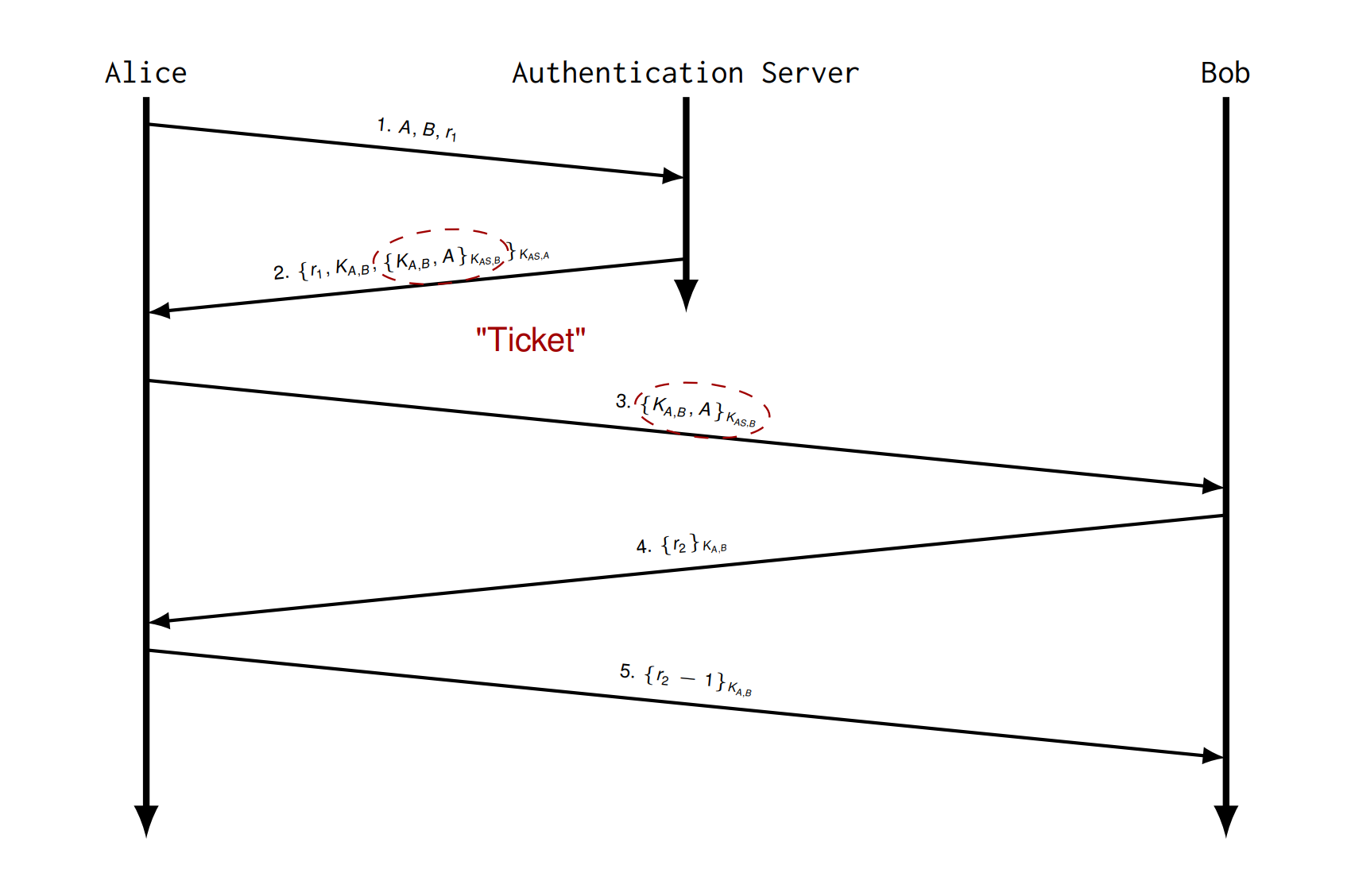
Try 3 Shared Key with AS
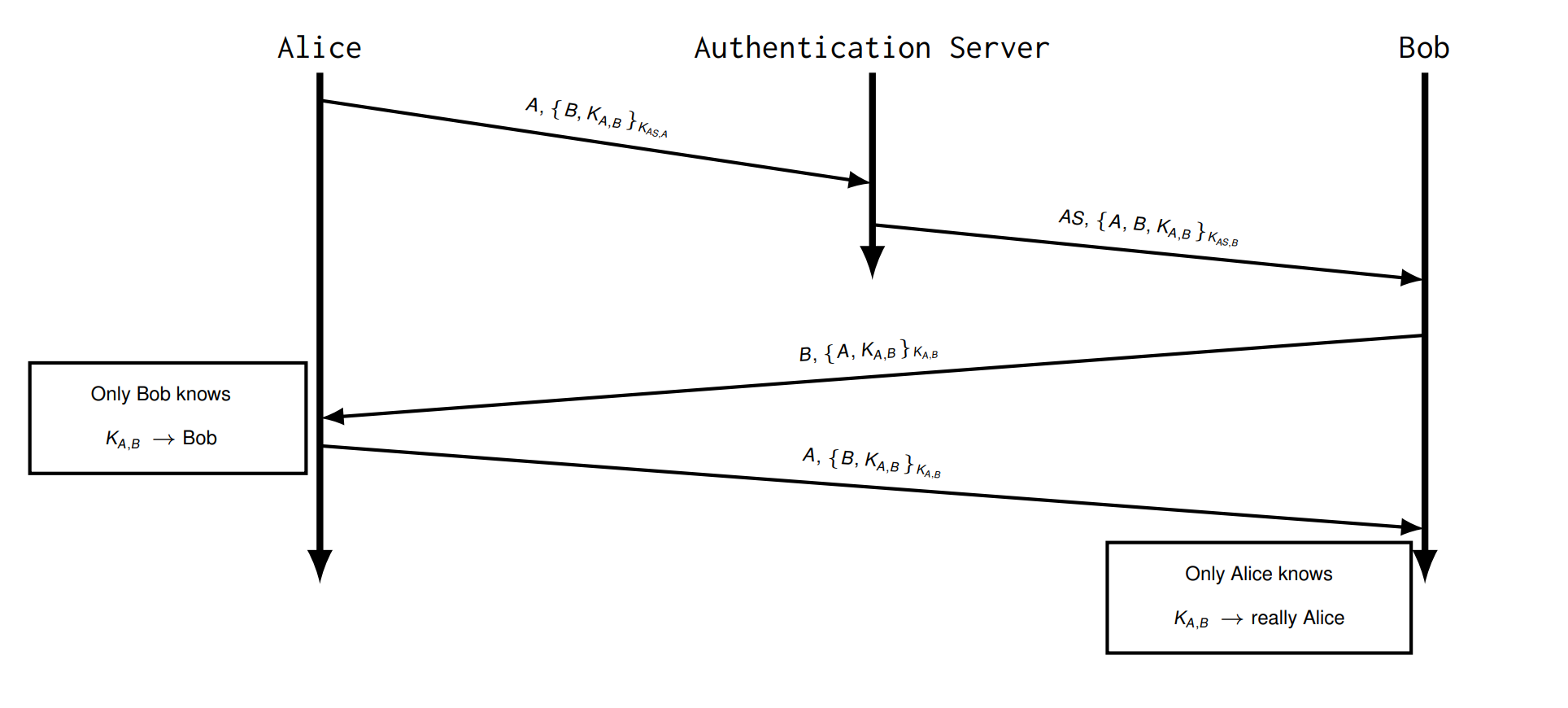
会被 Replay Attack, 因为可以记录下来 \(\{B,K_{A,B}\}\)
DoS Attack: Attacker replays Alice’s first message and causes a heavy work load in the entire network and all entities!
Try 4 Add nonce
Nonces \(N_A\) ,$ N_B$ → Principals need to keep book of "used" nonces and only accept unknown nonces.
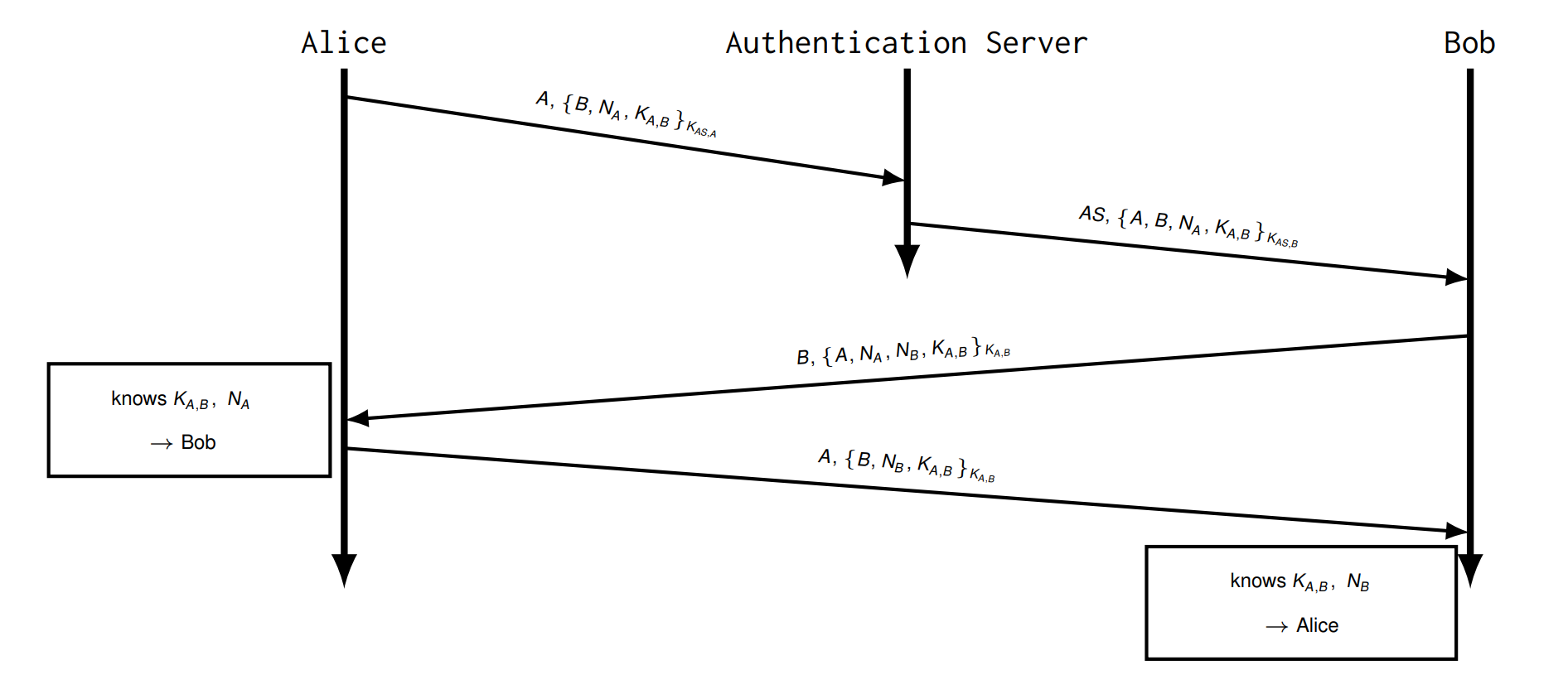
有一种会被 replay and oracle attack
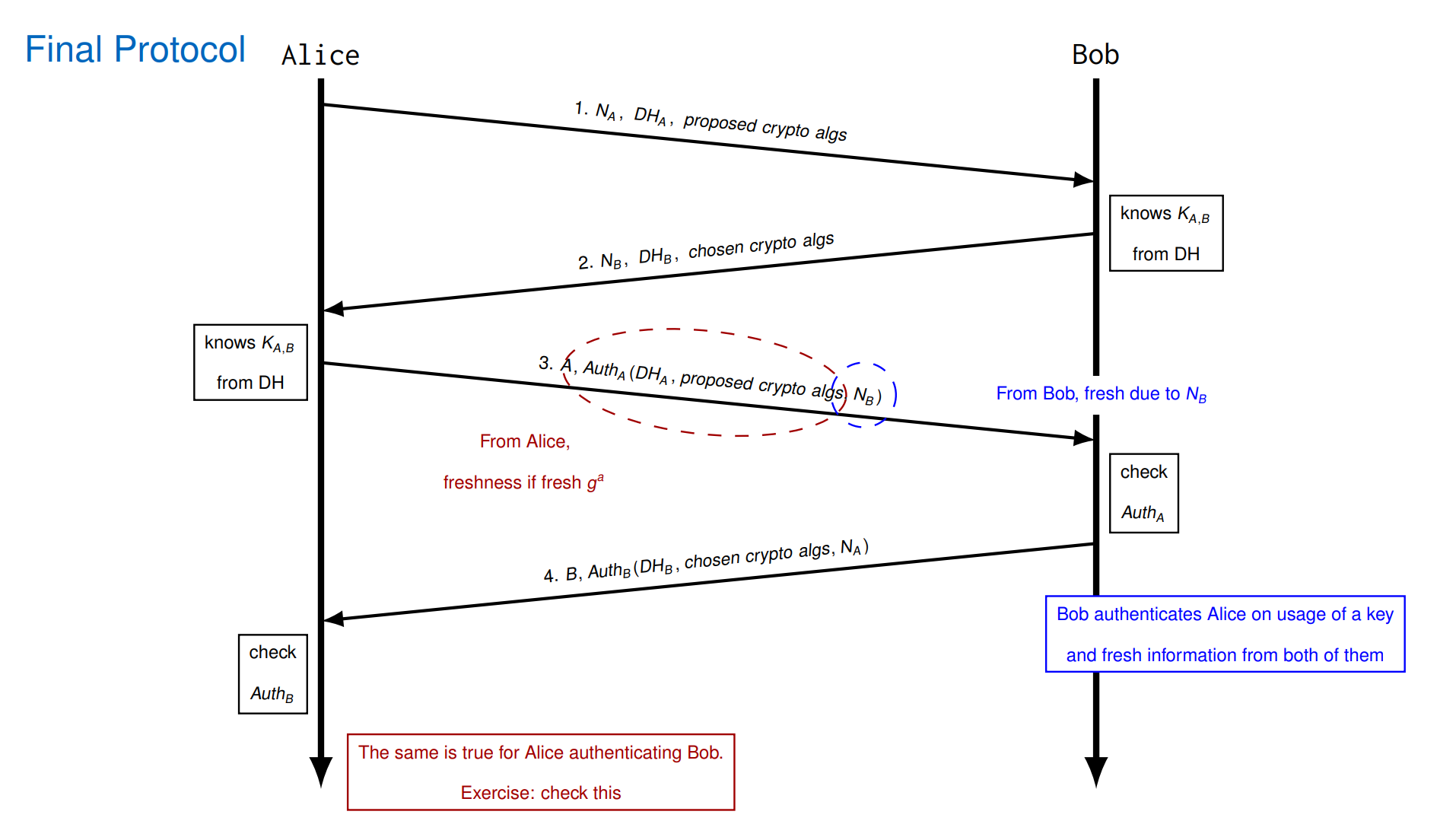
Try 5 Add forward secrecy
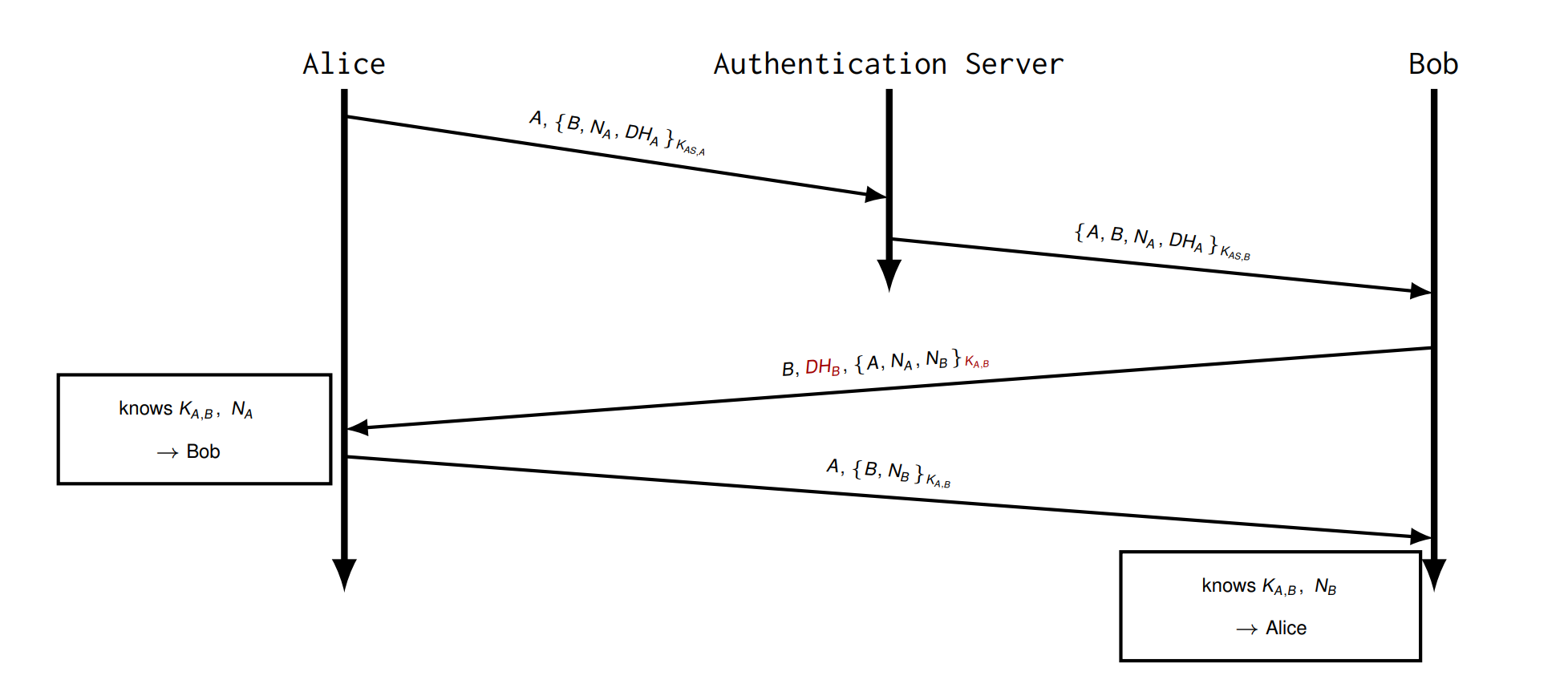
- If \(DH_B\) would be changed, Alice could not compute the same \(K_{A,B}\) .
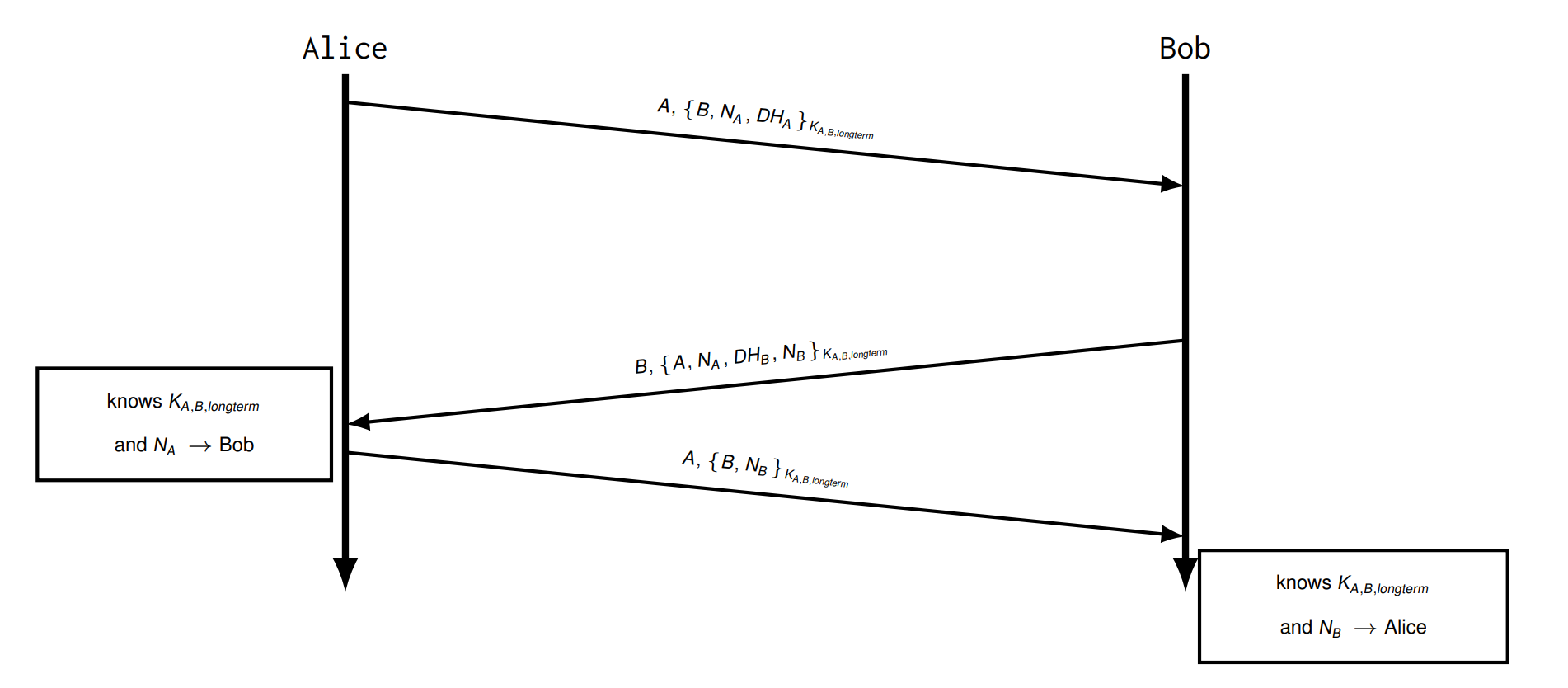
Try 6 Remove AS
Long-term key between A and B was exchanged via AS and is cached for a while
Try 7 Selection of Algorithm
cryptographic protocols should be flexible and configurable
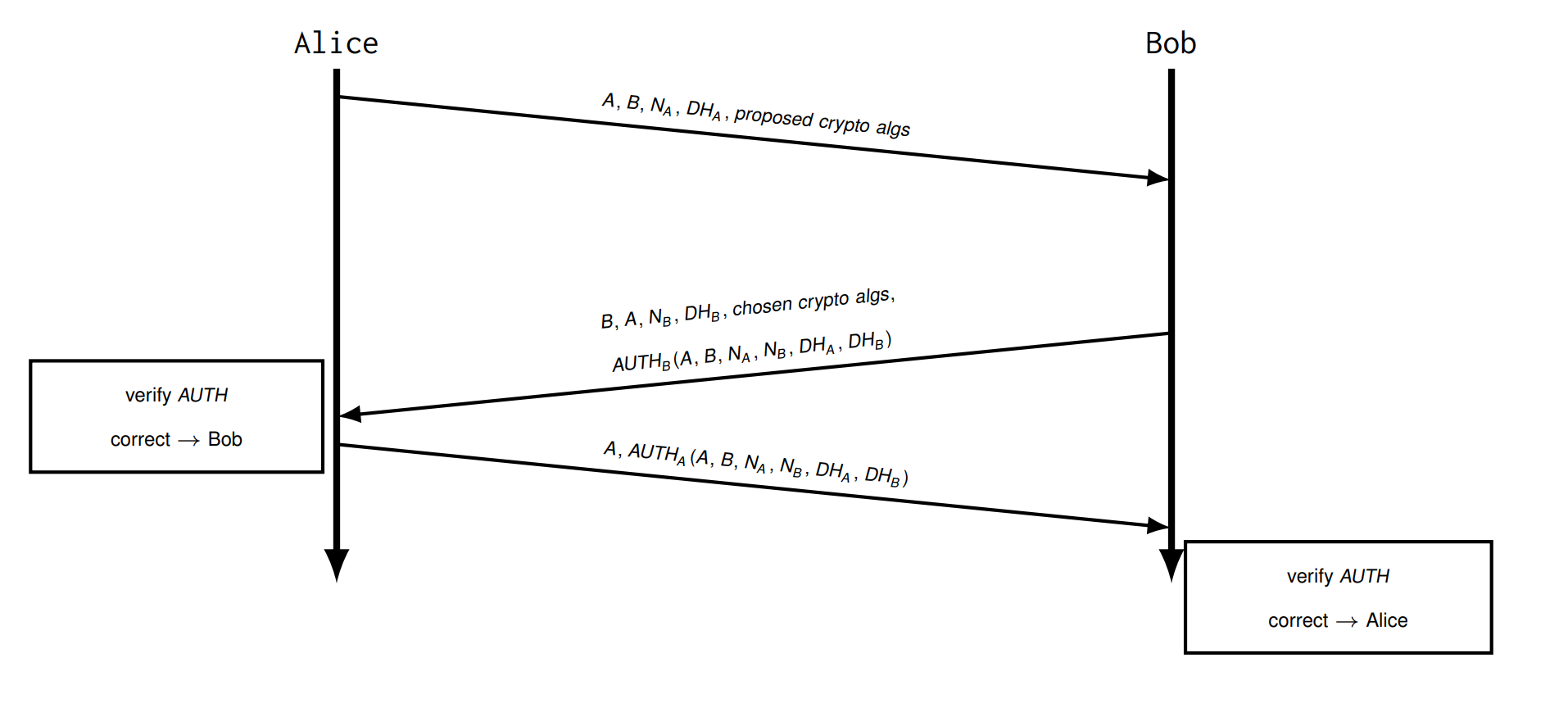
Problem: Algo are not authentiated = downgrade attack, replay attack
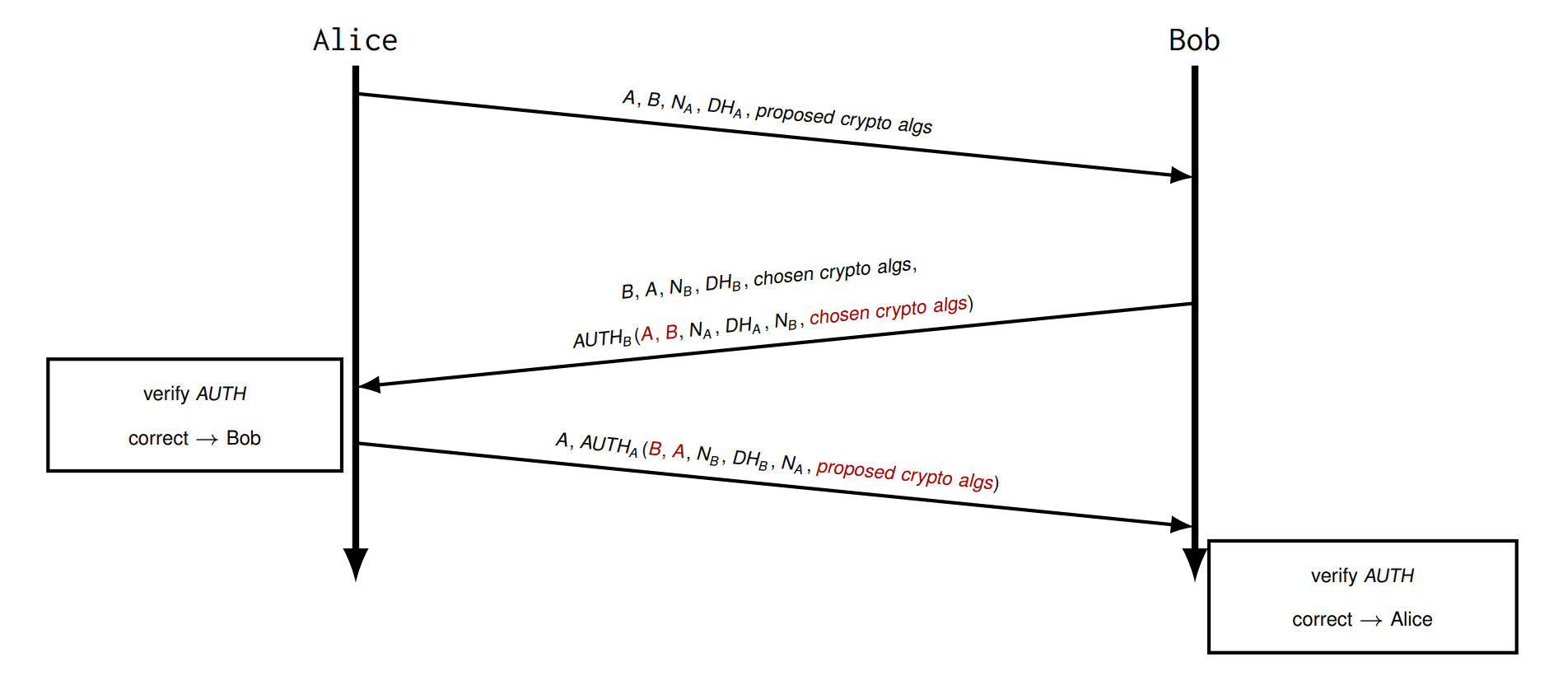
Try 8 AUTH Payload
AUTH payloads are different and contain information provided by both principals.
Final Protocol
Needham Schroeder Protocol
Symmetric
do not provide any forward secrecy
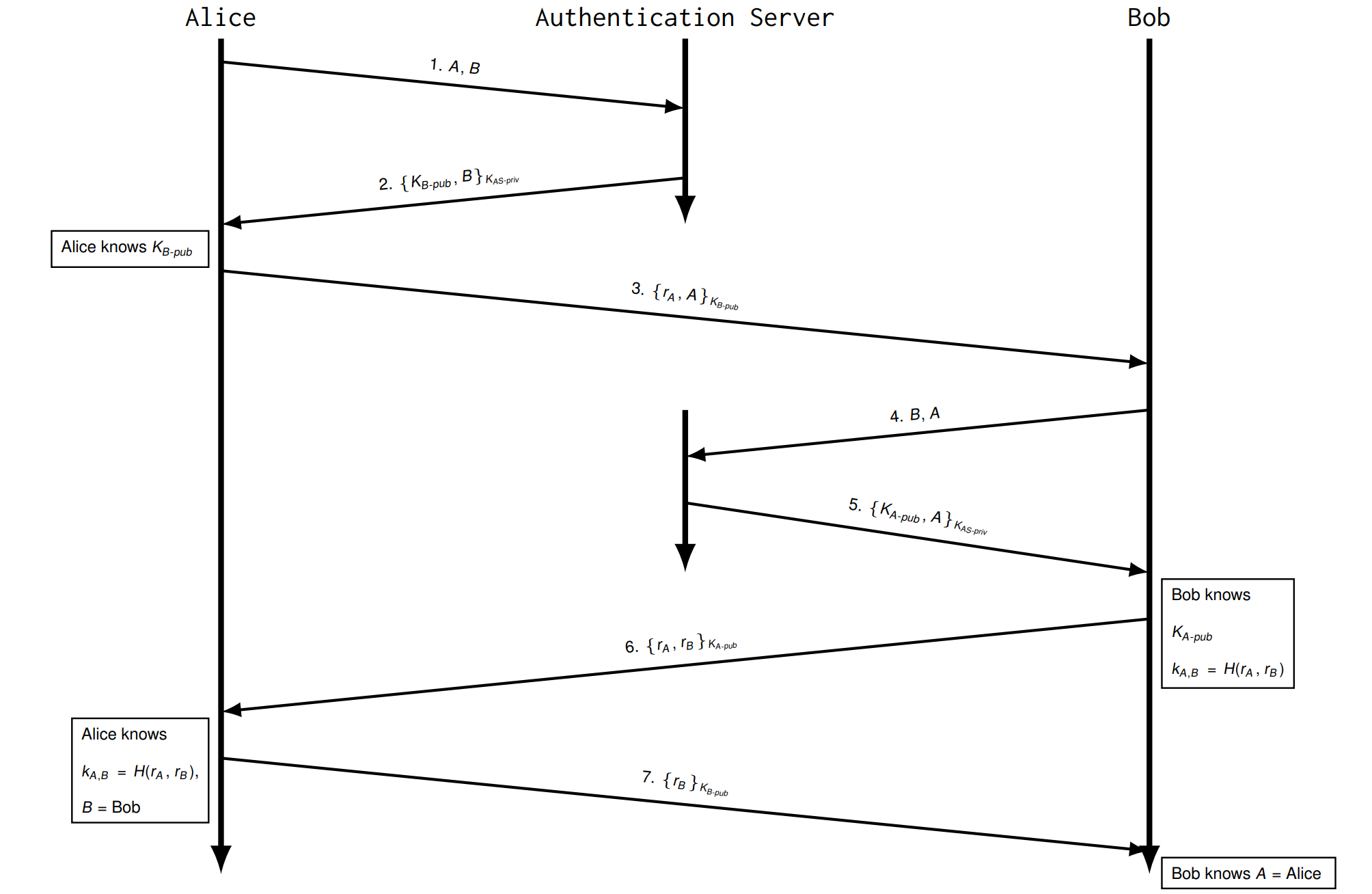
Asymmetric
Oracle attack:
Web Security
TLS is a popular cryptography protocol (HTTPS)
Client Certificate Authentication (CCA)
Push Service Architecture
软件更新推送
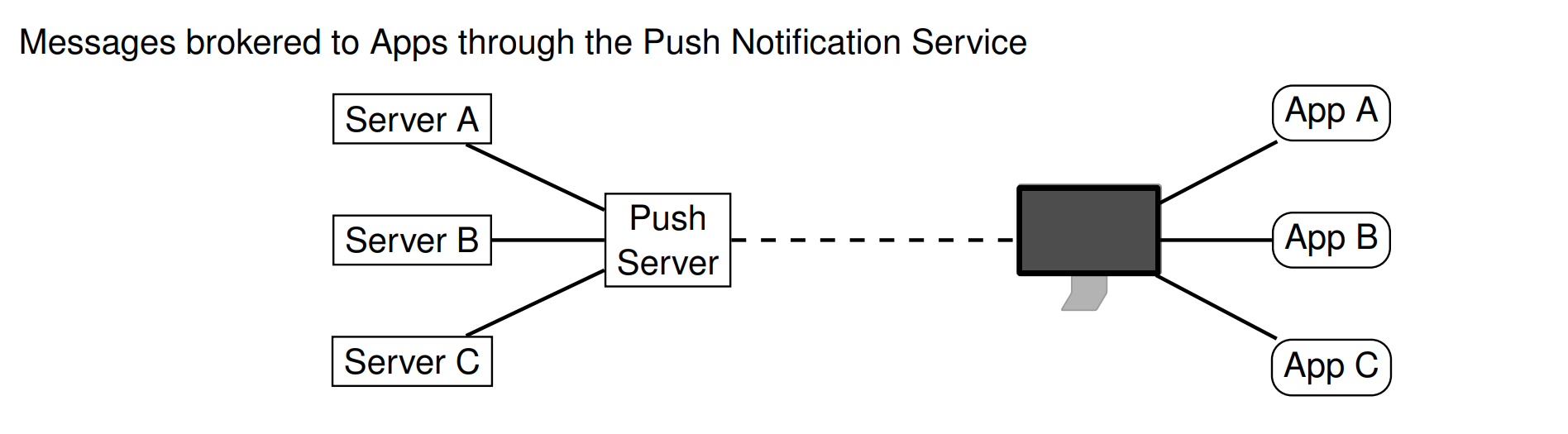
problem
- Apple Push Notification Service (APNs) is always on, service connect to push server.individulal device information leakage
Certificate Transparency
Validate CA adhere to guidelines = Public Logs
CT is Public logs for X.509
Advantage
- Adds transparency to X.509 in the hope of detecting malicious CA behavior early
- All issued certificates for a domain can be observed
Potential issues
- Needs changes on the side of CAs
- Information leak by public logs
The problem CT does not solve: Certificate Revocation
Certification Authority Authorization (CAA)
Domain name holder may restrict certificate issuance to a certain Certification Authority (CA), Realized via DNS source records
Realization
- Use newly defined DNS record type ’CAA’
- Domain owner can specify a list of CA’s permitted to issue certificates for the domain
IPSEC
用来让IP协议更安全
- data origin authentication
- data integrity
- confidentiality
- security policies
How it works
- Authentication, key exchange
- set keys and crypt algo
- secure channel
IPSEC Replay Protection
Use a sliding window
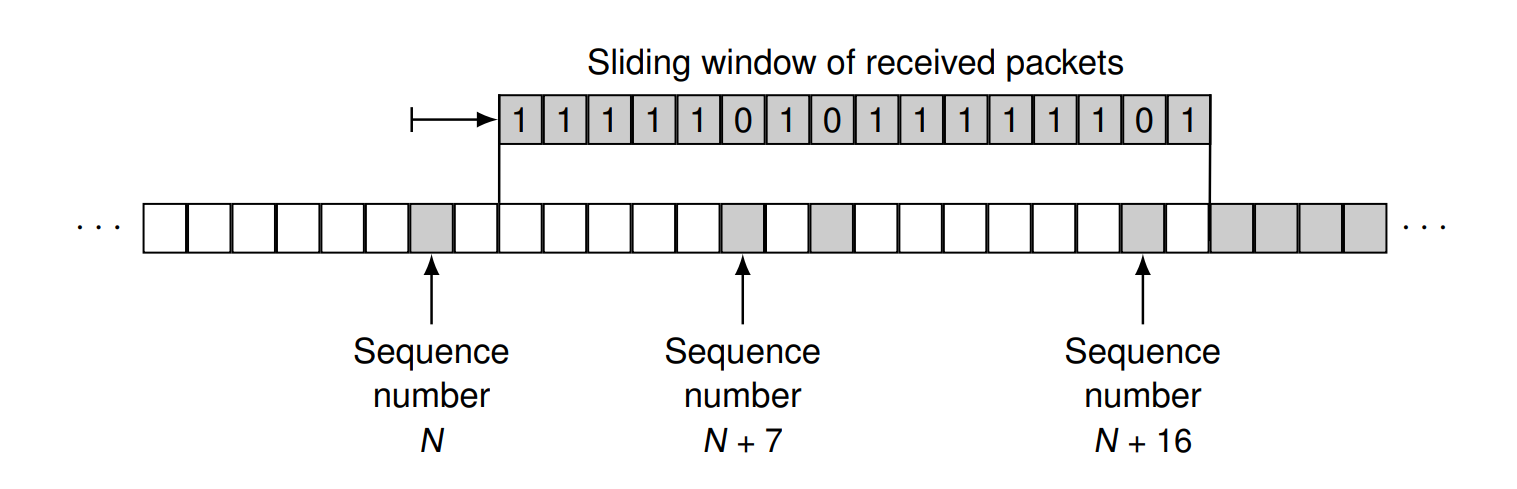
- If a received packet has a sequence number which
- is left of the current window ⇒ the receiver rejects the packet
- is inside the current window ⇒ the receiver accepts the packet and advances the window
- is right of the current window ⇒ the receiver accepts the packet and advances the window
IPSEC Security Protocol Modes
Transport Mode
- Only usable between communication endpoints
- Adds a security specific header (+ trailer if ESP is employed)
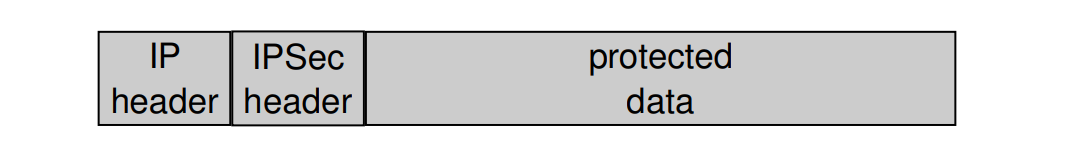
Tunnel Mode
- Usable with arbitrary peers
- Encapsulates IP packets
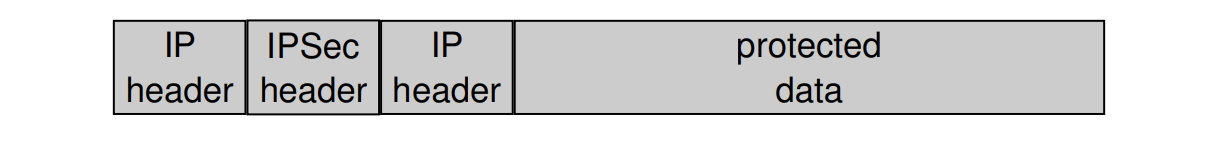
Traffic Selector
a set of properties used to characterize IP packets.
- used to define security policies
Security Policies
specifies which and how security services should be provided to IP packets.
- stored in Security Policy Database (SPD)
Security Associations
a simplex channel that describes the way how packets need to be processed
单向的通道
eg. encyption algorithm
- stored in Security Association Database (SAD)
在SAD中由 Security Parameter Index (SPI) 唯一标识
根据SPI在发送的时候加入AH/ESP头,在接受的时候映射到SA上
Encapsulation Security Payload
ESP is a generic security protocol that provides replay protection and one or both of
- Confidentiality • Encryption of encapsulated packets • Encryption of packet payloads
- Data origin authentication Creating and adding MAC to packets
Authentication Header
AH is a generic security protocol that provides
- Replay protection
- Data origin authentication • Creating and adding MAC to packets
IKEv2
- runs on UDP ports (500, 4500)
- mutual authentication
- DoS mitigation
- Integrated support for requesting an IP address (useful for VPNs)
Basic Structure
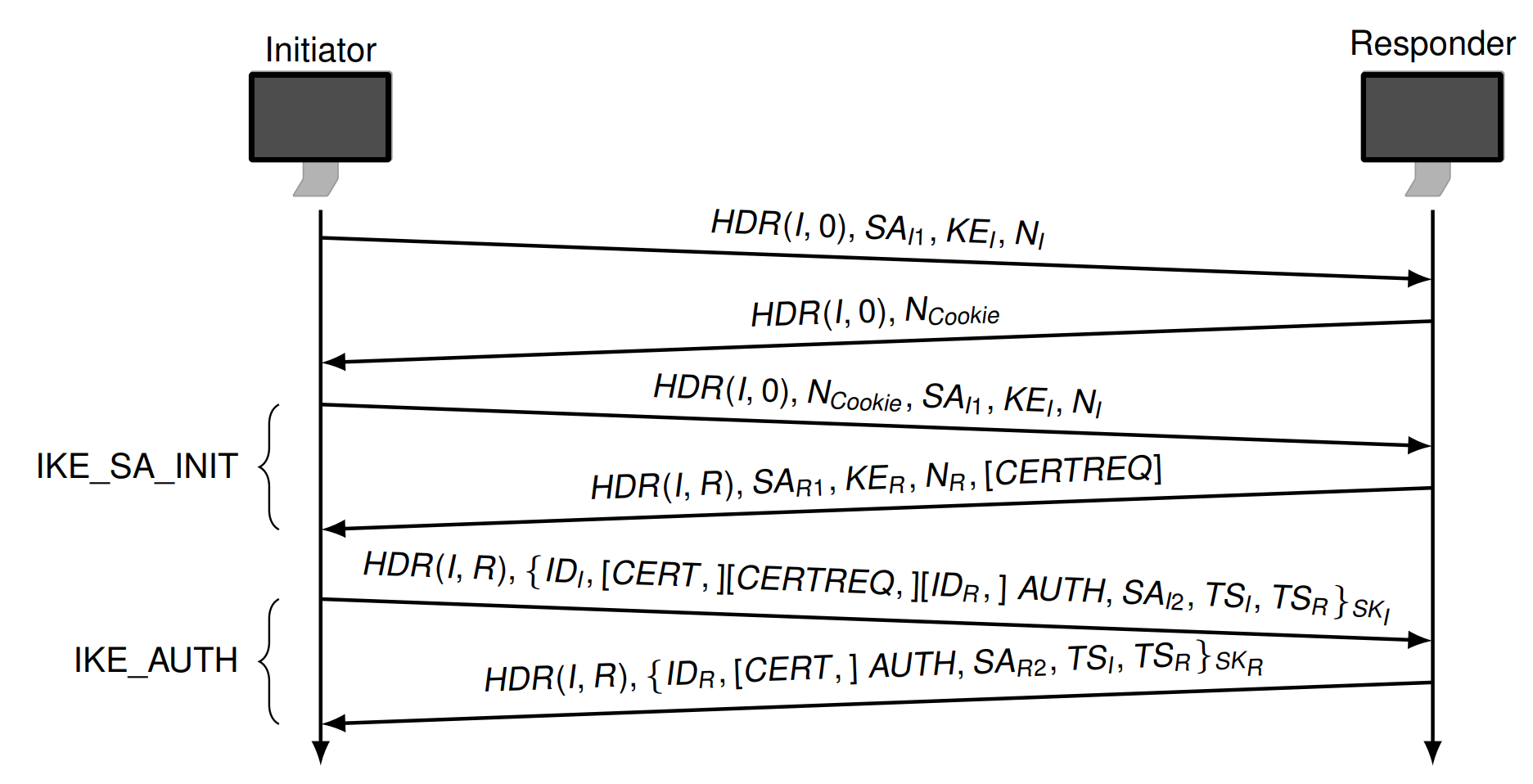
- IKEv2 communication consists of message pairs (request, response)
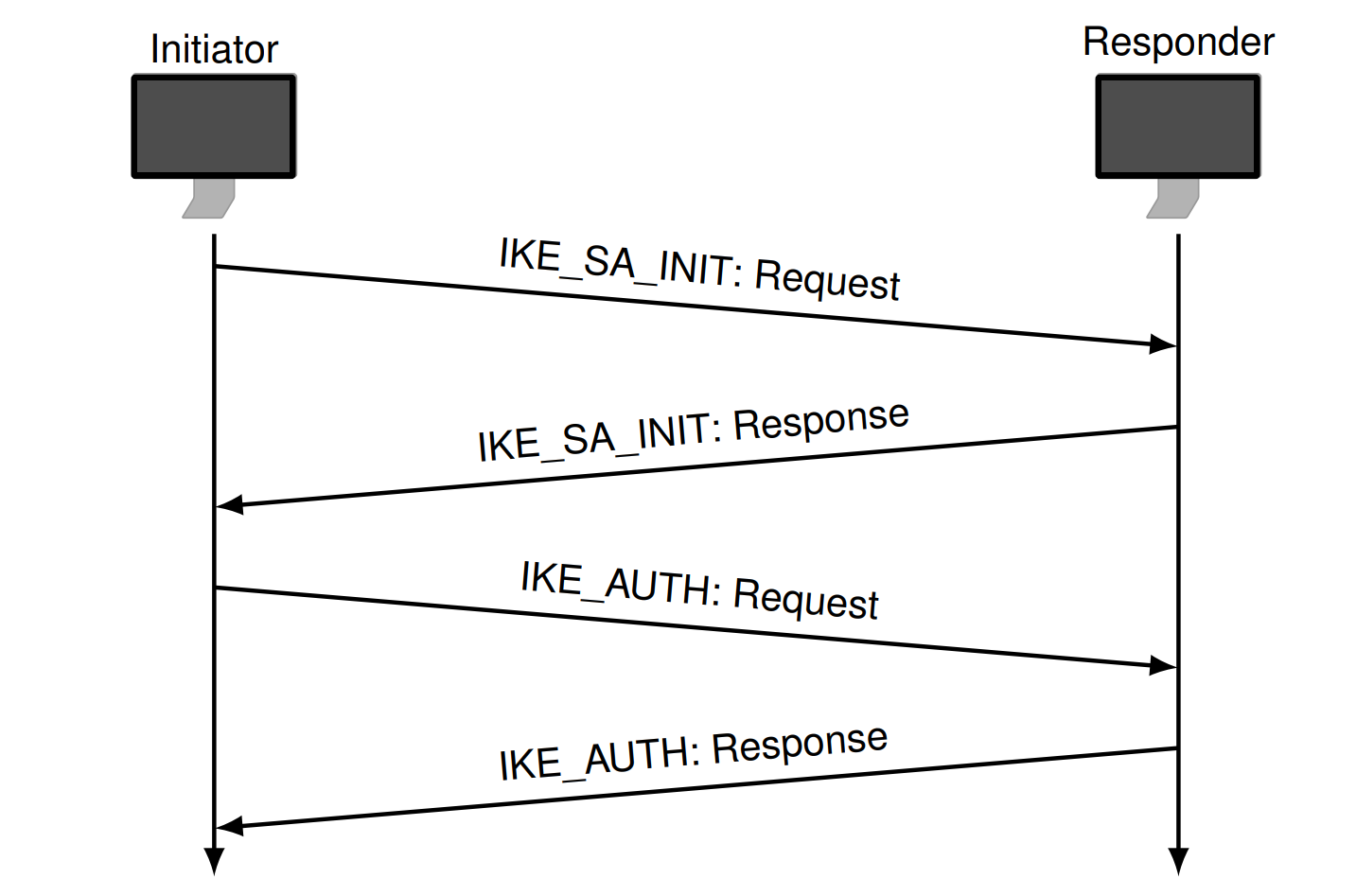
IKE_SA_INIT :
- Negotiates security parameters for a security association
(
IKE_SA) - Send nonces of DH values
IKE_SAis a set of security associations for protection of remaining IKE exchanges
IKE_AUTH:
- Authenticates the previous messages
- Creates first
CHILD_SA, set of Security Associations used to protect IP traffic with the AH/ESP protocol
IKE_SA_INIT Exchange
\(HDR(A,B)\) 是IKEv2 Message Header with SPI A and SPI B
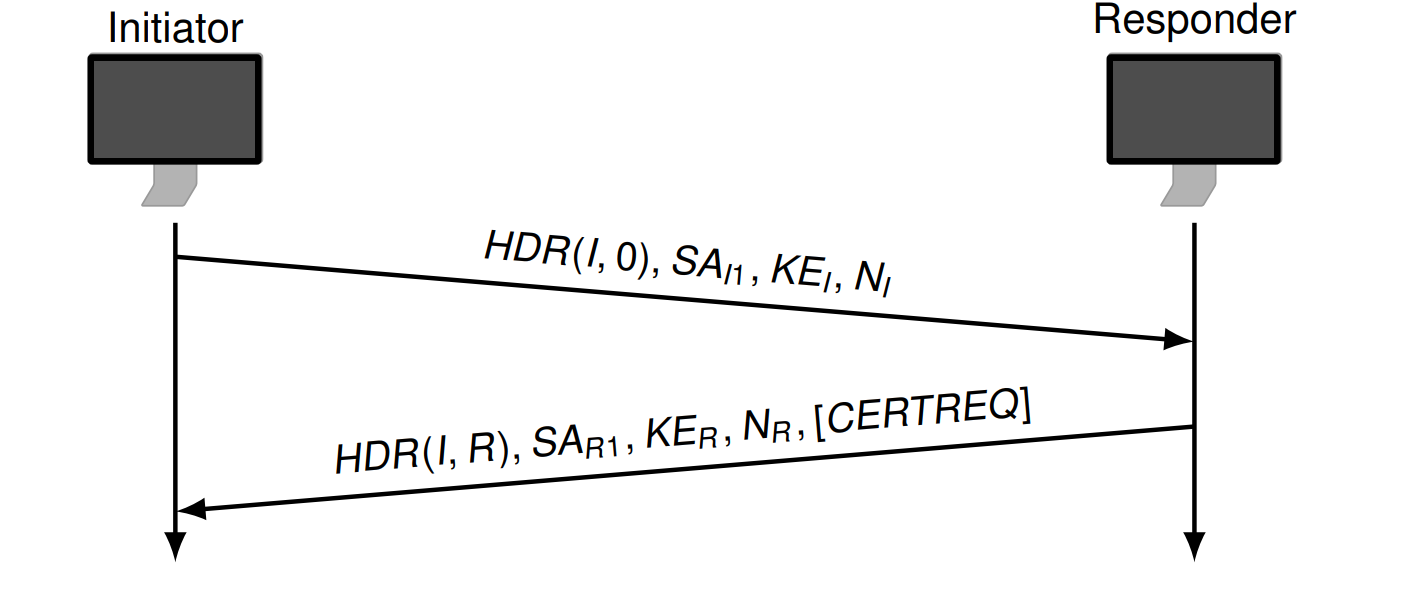
\(SA_{I1}\) 发送者支持的加密算法
\(SA_{R1}\) 接收者从 \(SA_{I1}\) 里选择的
KE: DH values
N: Nonces
Key Generation
prf is used iteratively \[ S K E Y S E E D:=\operatorname{prf}\left(N_l \mid N_R, g_{I R}\right) \]
\[ S K_D\left|S K_{A l}\right| S K_{A R}\left|S K_{E l}\right| S K_{E R}\left|S K_{P I}\right| S K_{P R}=\widetilde{p r f}\left(S K E Y S E E D, N_l\left|N_R\right| S P I_l \mid S P I_R\right) \]
IKE_AUTH Exchange
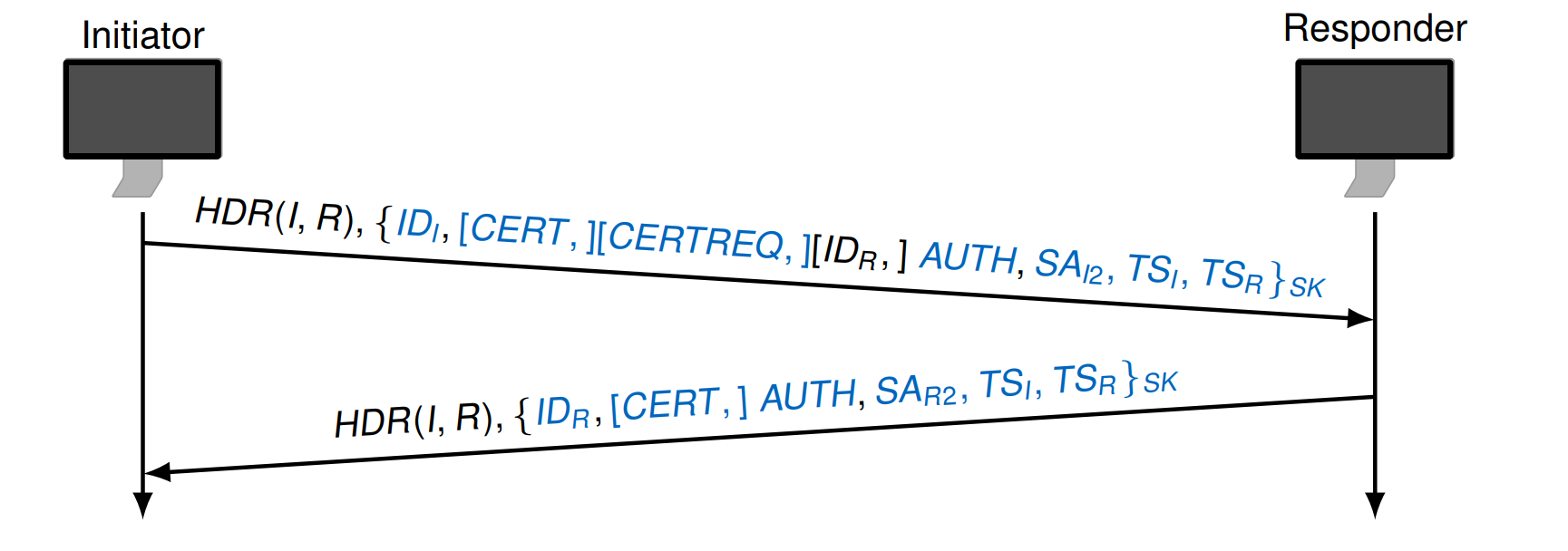
ID 用来验证身份
The remaining payloads {SAI2, SAR2, TSI, TSR } are used
to establish the first CHILD_SA
Authentication
Initiator signs:
(IKE_SA_INIT request payload \(\left.\left|N_R\right| \operatorname{prf}\left(S_{P I}, \overline{I D}_I\right)\right)\)
Responder signs:
(IKE_SA_INIT response payload \(\left.\left|N_l\right| \operatorname{prf}\left(S K_{P R}, \overline{I D}_R\right)\right)\)
Protection against flooding attacks
Advanced Feature
- Traffic Selector Negotiation (TSN)
- INFORMATIONAL Exchange
WireGuarrd
Privacy
Understanding of privacy
Privacy is mainly constituted by confidentiality of information and a mechanism of selective access control. Furthermore, privacy is often considered equal with anonymity, i.e. keeping the identity confidential.
Privacy protection Goal
- Unlinkability: The inability to connect and combine initially separate information
- Transparency: The ability to observe the data handling and processing of a system
- Intervenability: The ability (by data and system owners) to influence all planned or ongoing processing of personal data
General Data Protection Regulation
Fundamental Goals: Protection of personal data and individuals stay in control of their data. Harmonize legislation over whole EU, enable easy lawful data flow.
Scope
This Regulation applies to the processing of personal data wholly or partly by automated means and to the processing other than by automated means of personal data which form part of a filing system or are intended to form part of a filing system.
Secure Multiparty Computation (SMC)
The parties, or players, that participate are called \(P_1, \ldots, P_n\) Each player \(P_i\) holds \(x_i\) , players agree on some function \(f\), Their goals is to compute \(y=f\left(x_1, \ldots, x_n\right)\) while making sure that the following two conditions are satisfied
- Correctness: the correct value of y is computed; and
- Privacy: y is the only new information that is released
Modelling Adversaries
Adversarial Behaviour:
- Semi-honest: Follows the protocol specification. Tries to learn more than allowed by inspecting the transcript
- Malicious: Follows any arbitrary strategy
- Covert: Follows any arbitrary strategy, but is averse to being caught
Adversary threshold structure:
- Honest Majority Setting: The adversary controls a minority of all computing parties
- Dishonest Majority setting: The adversary controls up to n-1 of n computing parties
Oblivious Transfer(OT)
Input: Alice holds two strings (M0, M1), Bob holds a choice bit c
Output: Bob receives Mc but learns nothing about M1−c ,Alice learns nothing about c
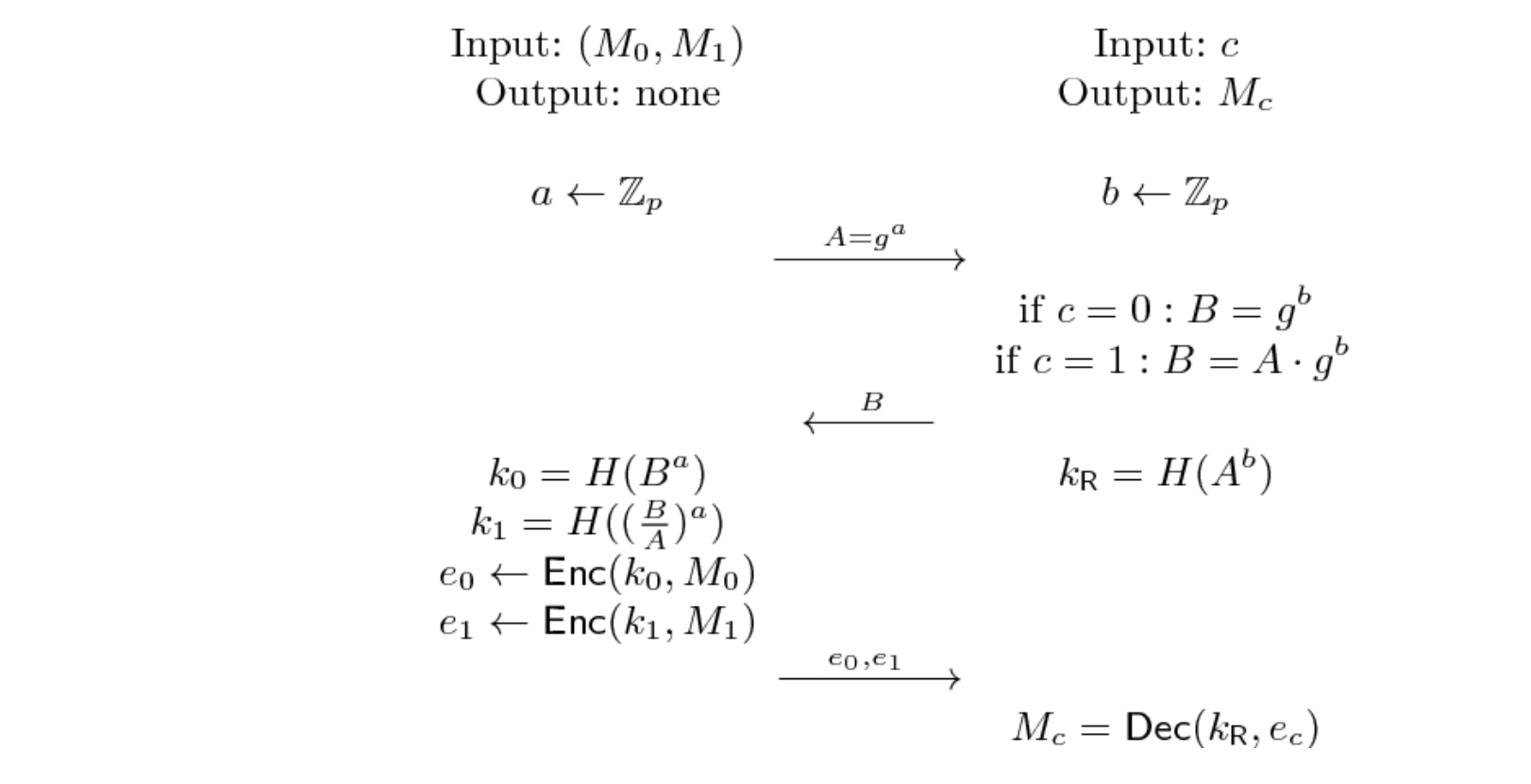
Yao’s Garbled Circuit Protocol
Inputs are protected by the cryptographic security assumptions of Symmetric Encryption and Oblivious Transfer.
BGW
BGW: Inputs are protected by a polynomial (Sharmir’s) secret sharing.
GMW
Inputs are protected by an XOR-secret sharing and the security assumption of Oblivious Transfer.
Sharemind
Inputs are protected by an additive/replicated secret sharing and the cryptographic security assumptions of Shared Random Number Generators.
Additive Secret Sharing with Beaver Triples
Inputs are protected by an additive secret sharing and the security assumptions of the utilized method to construct Beaver Triples.
Exercise
Exercise 1
Six Security Goals
Confidentiality, Authenticity, Data Integrity, Availability, Accountability, Controlled AccessRelationship between integrity and authenticity
authenticity implies integrityFor each of the six security goals, find an example of what the security goal can do to increase security.
Confidentiality: Control messages should be encrypted to prevent some third party from gaining inside knowledge
Authenticity: Devices inside our CPS should only accept control messages created by known/authentic and authorized entities.
Data Integrity: We need to make sure that modifications to the control messages can be spotted before the command is executed and causes harm
Availabiblity: The log server that logs the control messages must be able to perform its duty constantly.
Accountability: We log control messages to prevent disgruntled employees who intentionally damage the plant from getting away with it.
Controlled Access: All interfaces of the CPS to the outside world can only be used by authorized, known entities.What are the two types of network-level attackers?, What can each attacker do?
passive
- eavesdrop
- traffic analysis
active attacker
- all passive attack
- modify, replay, delay, delete, forge messages
Are there some attacks which are never detectable? Are there some attacks where it may not be decidable whether it is caused by an attacker or just a random error?
Eavesdropping and traffic analysis are entirely passive and can thus not be detected. Delaying, dropping messages may be detectable to a certain degree. However, the delay may also be induced due to unreliable transfer over the Internet If no additional security services are used, like digital signatures, it may be hard to differentiate between random transmission errors and random-looking malicious message modifications.Exercise 2
To understand: TCP SYN Cookies
Bob use hash function \(h(key, src_{ip})\) as SEQ
Verify: calc ACK, check if ACK = hashvalue + 1
draw TCP 3-way handshake
ACK = Sent_SEQ + 1 SEQ = Last_SEQ + 1
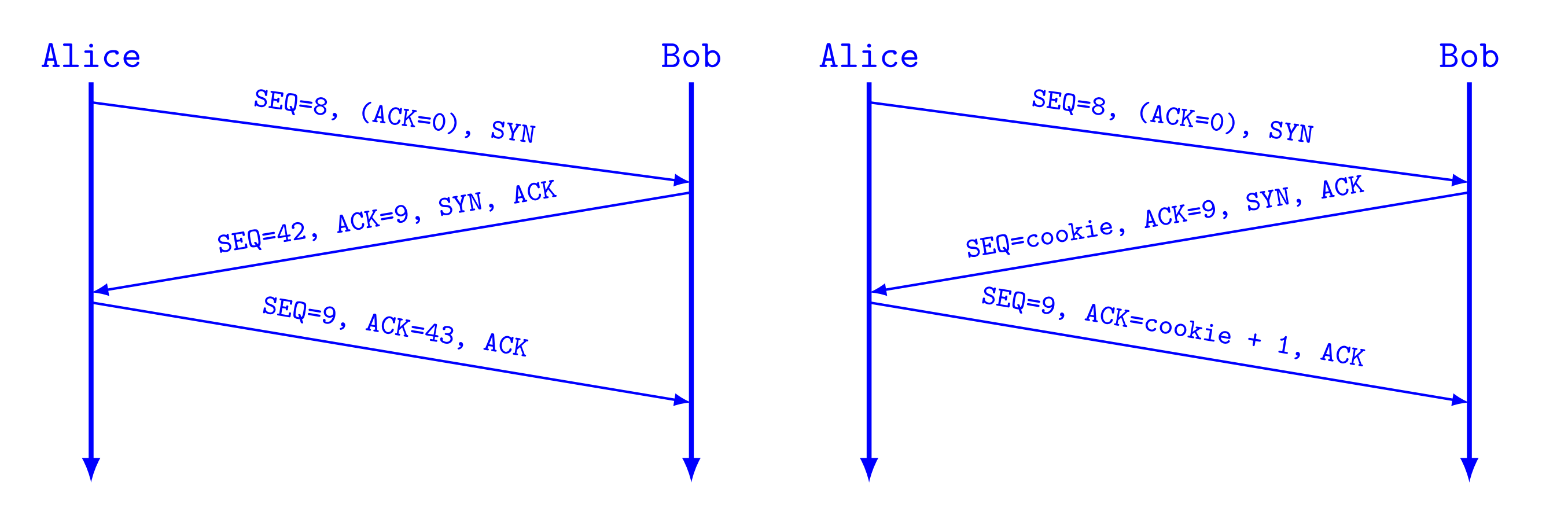
Name Advantage of TCP SYN Cookies
- Server does not need to allocate resources after the first SYN packet.
- Client does not need to be aware that the server is using SYN cookies.
- SYN cookies don’t requires changes in the specification of the TCP protocol.
Discuss the relationship between Integrity and Authenticity.
If we can guarantee integrity of, for example, a data item, we achieve that this data item cannot be changed without us noticing. However, we do not know that, for instance, Alice is the origin of the data item. Outlook: Integrity is often achieved by hashing data which creates a checksum (hash).
If we can guarantee authenticity of a data item, we know that, for instance, Alice has created it. However, if Bob changes the data item, its origin has changed, and its authenticity is voided. Outlook: In practice, authenticity is often achieved by combining hashing and signing
Think about a scenario where Authorization and Authentication are both needed.
Access Control system, Alice can modify and read, Bob can only read. First check authority, then determine user's access rights.Can you think about a scenario where some actions/events/... are authorized, but no authentication is needed?
Network firewall, usually does not (need to) authenticate communicating parties. However, it authorizes some communication events based on a rule list and discards othersExercise 3
Three security components as defined in the chapter ‘Firewalls and Security Policies’
- Security Goal
- Security Policy
- Security Mechanisms
Important port 22,53,80,443,25
SSH: 22 DNS: 53 HTTP: 80 HTTPS: 433 Clients : > 1023 SMTP: 25
Consequence: The source address is not specified
clients might spoof arbitrary IPsConsequence: The interface is not specified
The Internet can send arbitrary spoofed packets to your Zone 1.Configure Stateless
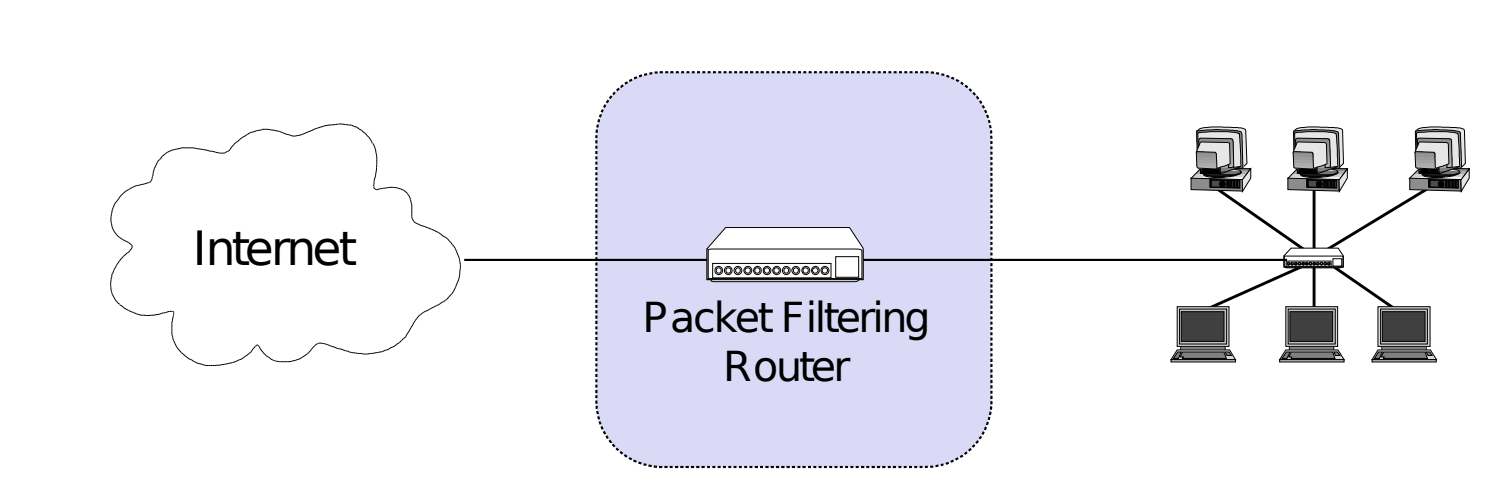
ACK: ANY or YESwhat are architectures of firewl
Simple Packet Filter Architecture
Dual-Homed Host Architecture
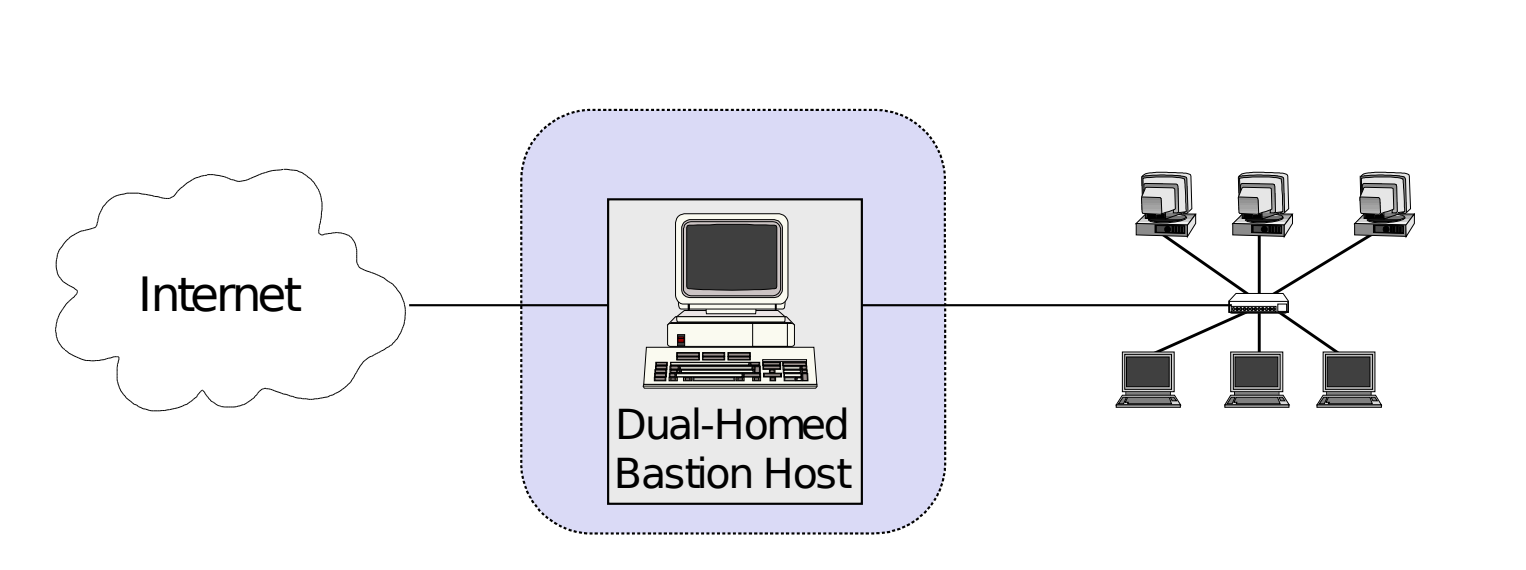
Screened Host Architecture Server in host area
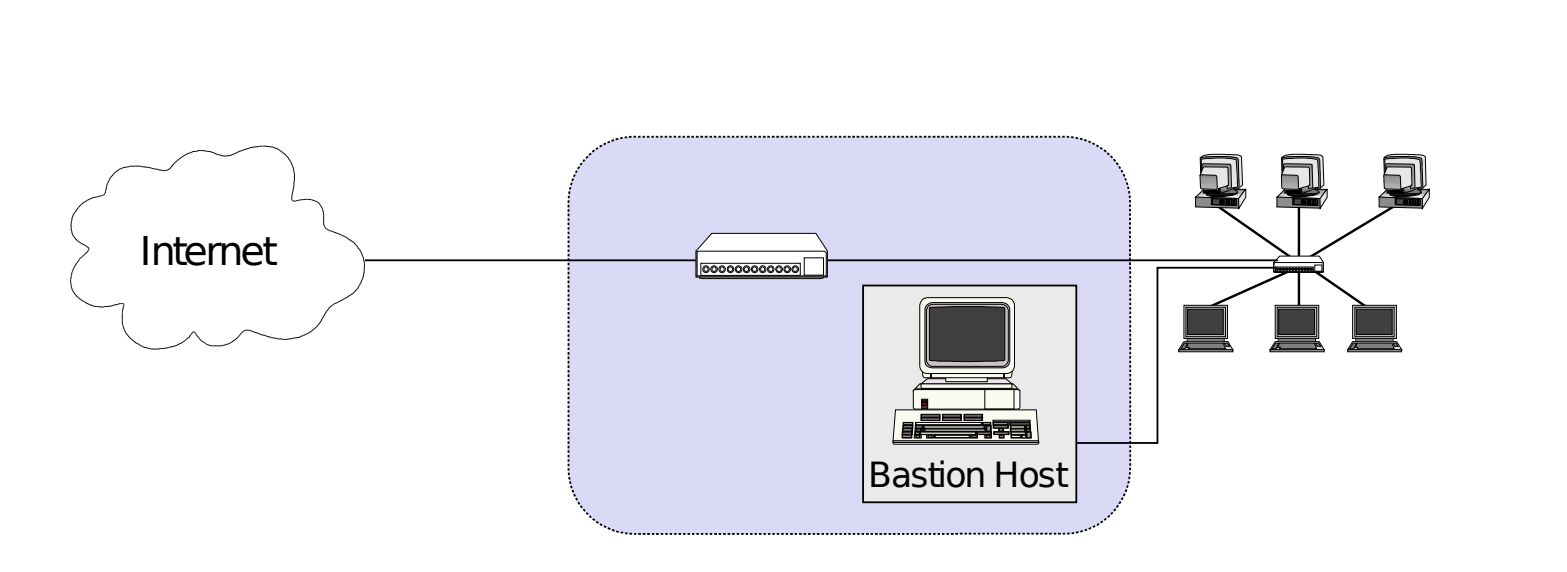
Screened Subnet Architecture 3 NICs
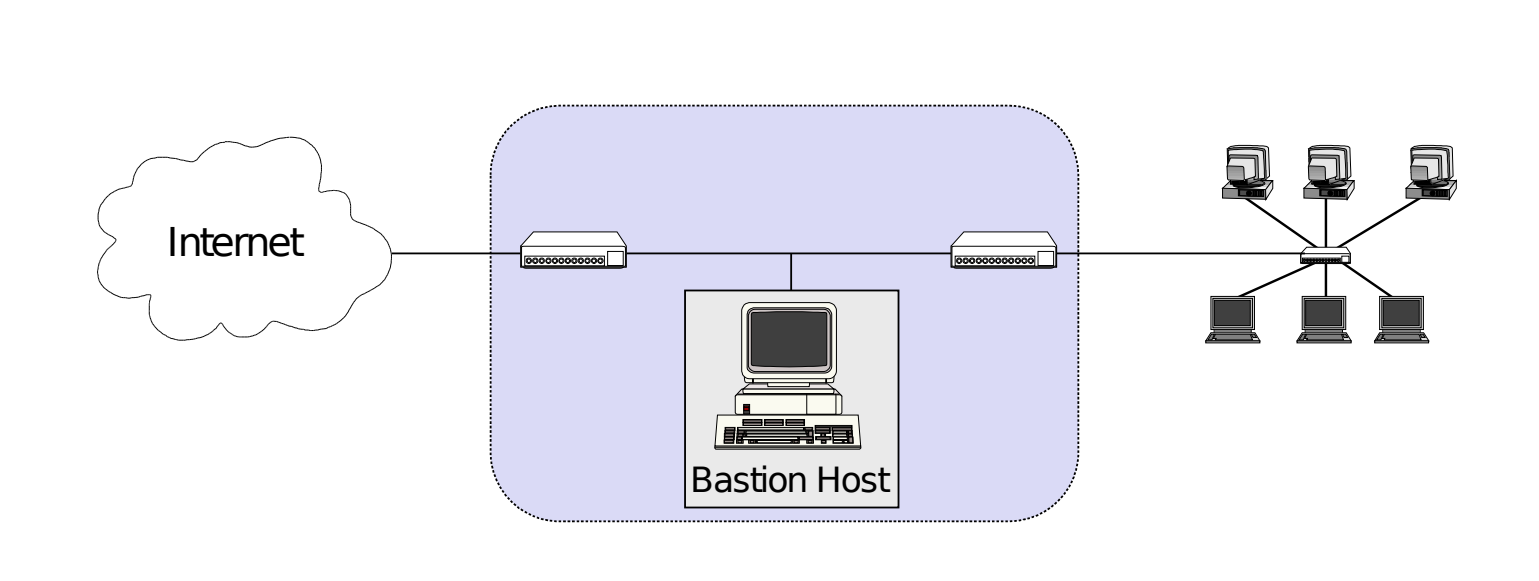
*What is a Bastion Host
- a host that is more exposed to the hosts of an external network than the other hosts of the network it protects.
What is Intrusion and IDS
- Intrusion: Compromise of a defined Security Requirement
- Intrusion Detection System: Software that has the function to detect and identify intrusions
Classification of IDS
Detection Method:
- Misuse detection
Store signatures of attacks in a database Monitor traffic for signatures Frequently update signature database
- Anomaly Detection
Model a normal or expected state of a system,Raise alarm if the current state differs more than a certain threshold
Data Source:
Network-based
Host-based
Detection Delay
Real-time
A posteriori
Reaction:
Passive
Active
Analysis
Individual
Cooperative
Compare Misuse Detection and Anomaly Detection
Misuse:
- Only known attack
- Very efficient detection
- Less false positives
- More false negatives
Anomaly:
- Able to detect new attacks
- Heuristics threshold definition is complex
- More false positives
What can IDS detect (HIDS, NIDS)
HIDS:
- Privilege Abuse
- Accidentally assigned privileges
- Access and modification of critical data
NIDS:
- Unauthorized network access
- network scans
- Abuse of bandwidth resources
Trade off for HIDS
running a HIDS would add performance drawbacks by real-time monitoring of the host activity.
Exercise 4
What is a measure for unpredictability?
Shannon Information Entropy
\[ H(X)=-\sum_x P(X=x) \cdot \log _2 P(X=x) \]
Shannon Information Entropy can be interpreted as the expected amount of bits, needed to encode the output of Xwhat is cryptographic hash function
Collision resist
One way
Random Oracle property
Modes of Encryption, name and draw
Electronic Code Book
最朴素的, \(Enc(m_i,k)=c_i\)

Cipher Block chaining
\(Enc_k(m_i \oplus c_{i-1})\) 一开始有个 \(IV\) (fresh 不是固定的)

Identical plaintext -> non-identical ciphertext
No integrity protection
Output FeedBack
把 block cipher 变成 stream cipher

- Decryption do not depend on previous blocks (Transmissino error only affects this block)
CounTeR
把 block cipher 变成 stream cipher

- Decryption does not depend on previous blocks.
Explain how a block cipher works, stream cipher
- A block cipher operates on input data of a fixed length, called block. Input block and key produce an output block of the same length as the input block.
- Stream ciphers make use of the ⊕ (XOR) operation and a key stream
How to compute HMAC
HMAC: \(H(K \oplus opad | H(K \oplus i p a d | m))\)Exercise 5
the random oracle property is requested for hash functions. Why can a construction of a hash function with random() or true randomness not work?
Hash function must be deterministic. For example, we could not decrypt RSA-OAEP if G and H were not deterministic.Salting
- If two users use the same password, the random r will guarantee that the hashes are not the same.
- It protects users with weak passwords against pre-computation.
- An attacker would need to compute a dictionary attack for each r
Why is it not a problem if r is known to an attacker?
No attacker will pre-compute rainbow tables for all combinationsActually, one should not use a “general-purpose” hash function like SHA256 at all to store passwords.Why are they needed and how do they compare to hash functions?
- General-purpose hash functions are designed to be computed efficiently
- Users are choosing weak passwords. Those functions are carefully designed that they also do not parallelize well, even with special hardware. They – of course – also use salting!
Exercise 6
Describe RSA
\(n = p \cdot q\) choose \(e \cdot d \equiv 1 \bmod \phi (n)\)
public key: \((n,e)\) secret key: \((n,d)\)
Enc: \(c \equiv m ^ e \bmod n\)
Dec: \(m = c^d \bmod n\)Describe OAEP
enhanced RSAWhat is threshold cryptography
- The private key does not exist in a central form but is split into n fragments or partial keys. A threshold signature can only be computed if at least t partial keys are involved.
Advantage of threshold cryptography
- The private key is more difficult to compromise, as the attacker needs at least t partial key in order to successfully compute a signature
- As the key resides on n different nodes, a threshold-cryptography-based signing system can still work if at least t nodes remain online
- For the same reason, it is less likely that the private key gets lost
Why use DKG involving a dealer
- With distributed key generation (DKG), the key never exists in its combined/centralized form.
- The dealer might keep a copy of the key split into fragments and use it for adversarial purposes
differences between verifying a threshold signature and a signature created with traditional asymmetric cryptography
No difference: In both worlds, the signature can be verified using the public key that corresponds to the centralized or distributed private keyExercise 7
What is the general purpose of a X.509 certificate?
Without any help, we do not know who owns which public key. A certificate solves this issue by creating a verifiable/authentifiable binding between an entity’s identity (name, email address, URL, etc.) (person, server, service, etc.) and a public key owned by that entityExplain why Root Certificates are self-signed and why the self-signed Root Certificates need to be included in a Root Store.
- Root CAs are the trust anchors of a PKI. Hence, Root Certificates need to be deployed via Root Stores
why private Root CA keys should not be used to perform "every day tasks"
A Root CA’s private Root Key skroot is one of the most valuable keys in a PKI. This is because countless sub-CAs and even more entities’ certificates depend directly or indirectly on it. The best practice for a Root CA is to create a new sub-CA and delegate signing power to it.what certificate revocation is and when we need to do it
Certificate revocation means a certificate is marked as being invalid before it expires.
- the private key skx that belongs to the certified public key pkx is lost or compromised
- A certificate can also be revoked if the ownership of the certified identity changes
Explain how CRL and OCSP works, what the problems of both are.
CRL
- CRL means that a CA periodically publishes a list of revoked certificates. The browser downloads this list and checks that the certificate it received from the server is not revoked.
- Downloading and checking the CRL is a time-consuming task.
- the CRL needs to be fresh, and the browser needs to be able to download it
OCSP
- a challenge/response protocol where the browser asks the OCSP server if a certificate is still valid
- OCSP has the same freshness problem as CRLs.
- an attacker can block requests, and browsers will most likely soft-fail.
- the OCSP server learns what sites the browser (= user) visits, which is a privacy issue.
What does certificate pinning mean
a computer has a list of "expected" certificates/public keys of websites. If the website presents an unexpected certificate, the browser can stop the connection attempt and warn the user.What problems does certificate pinning have
- the "trust on first use" problem: e browser does not know if the certificate it pins is authentic.
- Pinning is also problematic, as certificates can change for legitimate reasons like renewal.
Exercise 8
Attack on Cryptographic Protocols
Exercise 9
Problems of combining TLS-CCA with APNs
APNs is always-on, One of the first things your phone does in a new network, is logging into the APNs service. * ⇒ Possible user monitoring, tracking and censorshipWhat is CT
Public logs for X.509
What Advantages and problems does CT have
Adds transparency to X.509 in the hope of detecting malicious CA behavior early
All issued certificates for a domain can be observed
Needs changes on the side of CAs
Information leak by public logs
CAA record meaning (;, norecord,
issue xxx.com)
; means no CA can issue
no record : all can issue
issue xxx : xx can issueWhat CA checks for CSR
obtain CAA records for every DNS domain name in the Cert’s SANs. For wildcard domain names, you need to obtain the base domain.What DNSSEC try to solve
However, the original design of DNS did not include any security features. In order to prevent MitM and spoofing attacks, DNSSEC adds authenticity and integrity protection to DNS replies.
How DNSSEC is realized
DNS resource records (RRs) are grouped into RRsets based upon their type.The resulting RRset is digitally signed, using public key cryptography. The signatures are stored in a new record type (RRSIG) alongside the existing records for a zone.
How many keys does every Zone have? Why?
4 keys in two keypairs:
- Zone-Signing-Keypair (ZSK). Private key only signs resource records.
- Key-Signing-Keypair (KSK). Private key only signs ZSK pubkeys.
Which improvement does the NSEC3 resource record provide?
While providing authenticated denial of existence, use of the original NSEC record type enables an attacker to enumerate all domains in the respective zone.
The NSEC3 record type impedes this practice by saving the cryptographic hash of the next secure domain name, instead of its plaintext.
In order to enumerate zone names with NSEC3 records, an attacker thus would need to find a reasonable preimage for the next-owner-name hash in every NSEC3 resource record.Why Mode of encryption
- need when length of msg > length of block size
- reuse the same key, avoid identical ciphertexts for identical messages.
Are modes of encryption necessary for stream cipher
NO. A stream cipher generates a key stream and XORs the plaintext with it. You can request a key stream of arbitrary size and directly encrypt (⊕) messages of arbitrary length with it. However, the key stream generation must not depend on the secret key alone. Otherwise, the same keystream would be generated and identical messages would be encrypted to same ciphertexts. Hence, it is necessary to add randomness (IV) when initializing the key stream generator.Exercise 10
secure the communication between their servers. However, some of their services require connection via plain IP and don’t support communication over secure channel implementations on higher OSI layers (e.g., TLS). Which solution do you recommend?
Use a secure channel implementation such as IPSecWhat can IPSEC Provide
The secure channel transparently protects IP traffic and allows the legacy services to run. IPSec provides data origin authentication, connectionless data integrity, confidentiality, all configured through security policies.only require authenticity, but not confidentiality of exchanged messages. Which secure channel protocol would you employ in that case?
- AH and ESP offer authentication protection. However, besides the payload,
- AH additionally protects the preceding IP header
- AH offers more protection in this case. If both ESP and AH are applied, ESP should be applied first (as the inner layer), s.t. AH protect the outer IP header.
What is communication endpoints and cryptographic endpoints
- Cryptographic Endpoints: Entities that process IPSec headers
- Communication Endpoints: Source and destination of an IP packet
Two Mode of IPSEC and when to use
- Transport Mode: cryptographic endpoints are also the communication endpoints
- Tunnel Mode: at least one cryptographic endpoint is not a communication endpoint.
Draw structrue of Packet of two modes
transport mode:
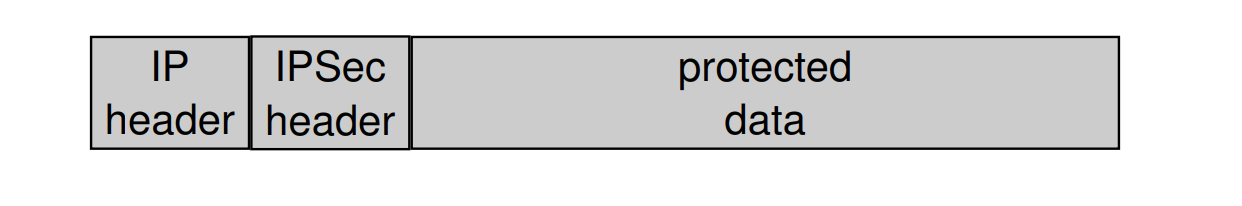
tunel mode
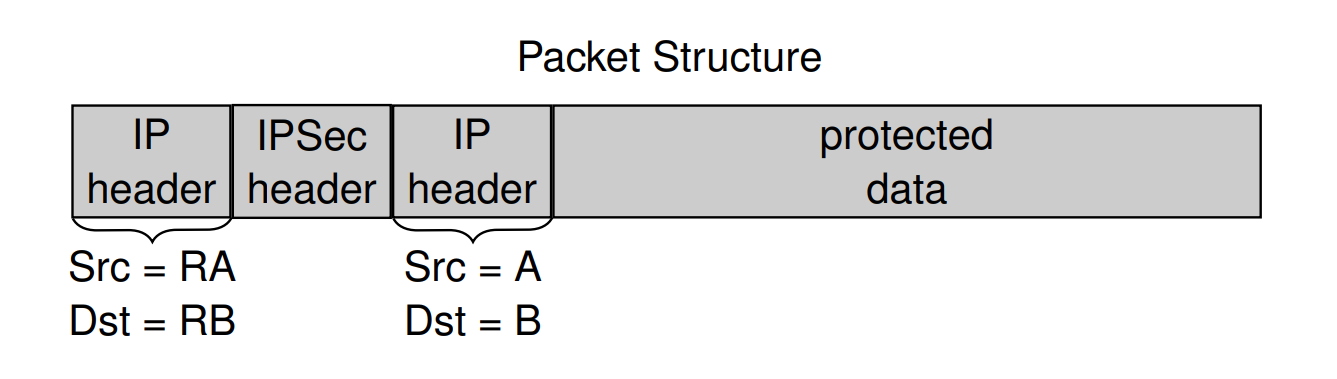
Definition of an IPSec Security Policy (SP) and a Security Association (SA)
- SP: Description of how security services should be provided to (categories of) packets
- SA: Explicit packet transformations for simplex channel between to communication parties
a bidirectional IPSec secure channel with both AH and ESP protection for their traffic. How many SAs are instantiated on every peer at the end of the process?
A SA represents a simplex channel for exactly one type of transformation (e.g., AH). Bidirectional communication requires two SAs for each transform, resulting in four SAs for two transformations in duplex mode.Is it a good idea to manually configure SAs? Why?
Bad:
- The chosen keys/algorithms might be insecure and/or not provide PFS
- Manual configuration is error prone
- Manual configuration doesn’t scale
(Understand IKEv2) An IKEv2 protocol run between Initiator and Responder begins with two (Request, Response) exchanges. After the exchanges are done, which data has been negotiated? What has been established?
Two exchanges:
- IKE_SA_INIT: IKE SA parameters, nonces, DH values
- IKE_AUTH: Initiator/Responder identities, Auth previous messages, prove knowledge of secrets, first CHILD_SA parameters After the two exchanges, an IKE security association, as well as an IPSec child security assocation have been established. All messages and the identities of Initiator/Responder have been authenticated.
Exercise 11
Adversary Model
Adversarial Behaviour:
- Semi-honest adversaries: Adversary follows the protocol specifications but tries to learn private inputs (also called honest but curious)
- Malicious adversaries: Adversary can follow an arbitrary protocol
Adversary threshold structure:
- Honest Majority Setting: The adversary controls a minority of all computing parties
- Dishonest Majority setting: The adversary controls up to n-1 of n computing parties
computation protocol be secure
- Input Privacy: Inputs of each party need to remain private under the assumptions of the chosen adversary model
- Correctness: Output of the computation needs to be correct under the assumptions of the chosen adversary model
Summerize: GMW, Yao’s Garbled Circuit protocol, BGW, Sharemind, Additive Secret Sharing using Beaver Triples
- GMW: Inputs are protected by an XOR-secret sharing and the security assumption of Oblivious Transfer.
- Yao’s Garbled Circuit Protocol: Inputs are protected by the cryptographic security assumptions of Symmetric Encryption and Oblivious Transfer.
- BGW: Inputs are protected by a polynomial (Sharmir’s) secret sharing.
- Sharemind: Inputs are protected by an additive/replicated secret sharing and the cryptographic security assumptions of Shared Random Number Generators.
- Additive Secret Sharing with Beaver Triples: Inputs are protected by an additive secret sharing and the security assumptions of the utilized method to construct Beaver Triples.
Construct Shamir’s secret shar
(n,k) constructs a random polynomial of degree k-1, ree 4. Each computation party’s share corresponds to one point of the polyomial. At least five parties are needed to solve an equation of degree 4, thus reconstructing theCaluculate number of encryptions
number of gate * 4(entries per gate) * 2 (encryptions per entry)How to calc a*b secretly
By resharing s1, s2, s3 before exchanging themMore Exercise
what is Kerberos
Kerberos is an authentication and access control service for workstation clusters
Design goals of Kerberos
- Security
- Reliability
- Transparency
- Scaleability


